126
a. Add a user account on the server. (Details not shown.)
b. Configure the authentication, authorization, and accounting settings. (Details not shown.)
Verifying the configuration
1. From the navigation tree, select Security > Authentication > RADIUS.
2. Verify the configuration of RADIUS scheme macauth.
3. From the navigation tree, select Security > Authentication > ISP Domains.
4. Verify the configuration of ISP domain macauth.
5. Use the user account aaa and password qaz123wdc to pass MAC authentication.
6. From the navigation tree, select Security > Access Control > MAC Authentication.
7. Verify that the number of online users is not 0 on GigabitEthernet 1/0/1.
RADIUS-based port security configuration example
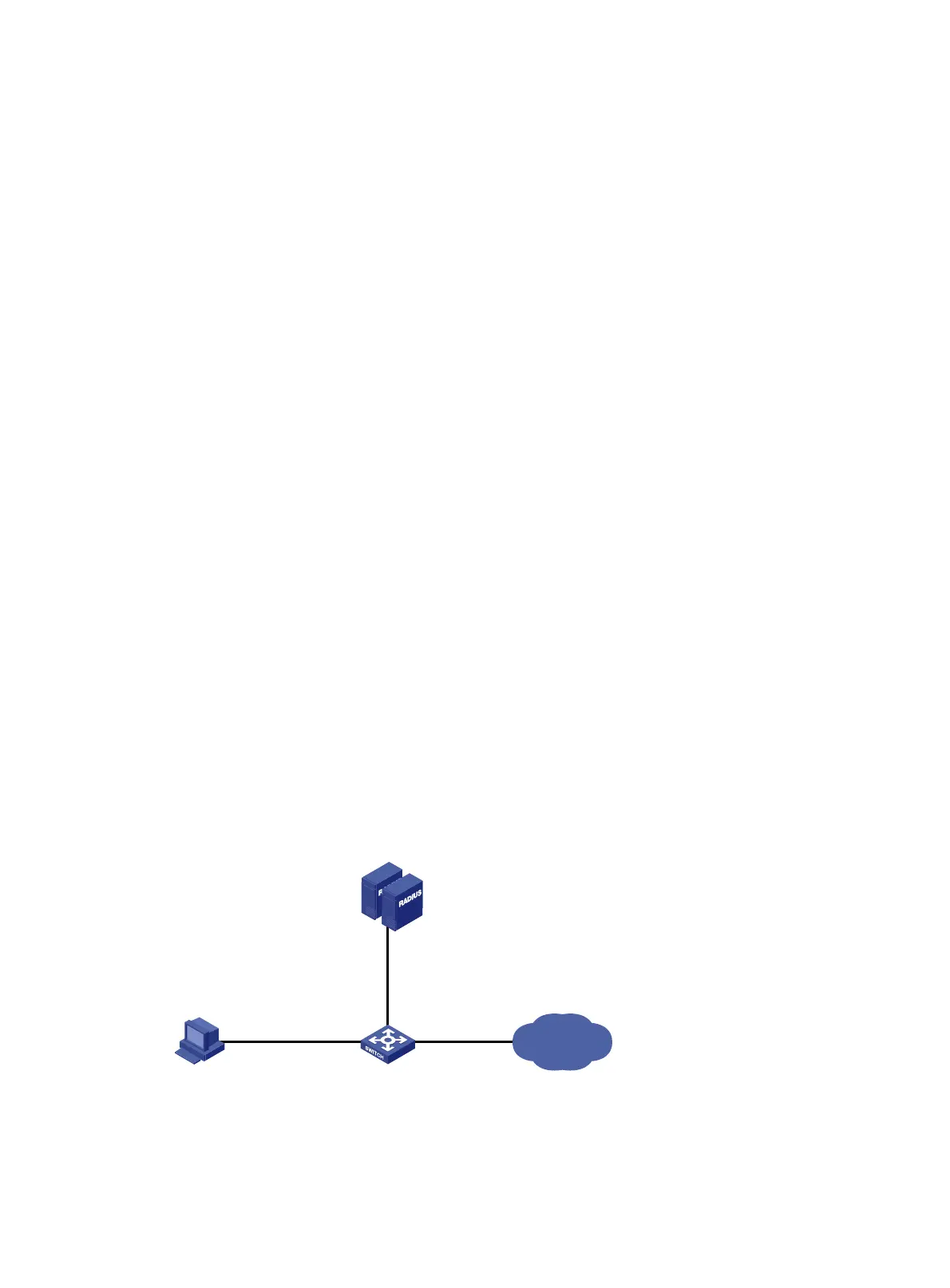
Network requirements
As shown in Figure 44, GigabitEthernet 1/0/1 operates in userLoginWithOUI mode to control Internet
access of users.
Configure the switch to meet the following requirements:
• Use the RADIUS server to perform authentication, authorization, and accounting for users.
• Use name as the authentication and accounting shared keys for secure RADIUS
communication between the switch and the RADIUS server.
• Use ports 1812 and 1813 for authentication and accounting, respectively.
• Authenticate all 802.1X users in ISP domain portsec, and exclude domain names from the
usernames sent to the RADIUS server.
• Allow only one 802.1X user and one user whose OUI matches one of the following OUIs to
come online on GigabitEthernet 1/0/1:
{ 1234-0100-1111
{ 1234-0200-1111
{ 1234-0300-1111
{ 1234-0400-1111
{ 1234-0500-1111
Figure 44 Network diagram
Configuration procedure
1. Configure IP addresses for the interfaces, as shown in Figure 44. (Details not shown.)
Internet
Switch
Host
192.168.1.2/24
GE1/0/1
Vlan-int2
192.168.1.1/24
RADIUS server
10.1.1.1/24
GE1/0/2
Vlan-int3
10.1.1.10/24

 Loading...
Loading...











