Chapter 2: System Configuration
18
You can allow serial port devices to be accessed from nominated network interfaces using Raw
TCP, direct Telnet/SSH, unauthenticated Telnet/SSH services, etc.
4. Click Apply
Web Management Settings
The Enable HSTS checkbox enables strict HTTP strict transport security. HSTS mode means that a Strict-
Transport-Security header should be sent over HTTPS transport. A compliant web browser remembers
this header, and when asked to contact the same host over HTTP (plain) it will automatically switch to
HTTPS before attempting HTTP, as long as the browser has accessed the secure site once and seen the
S-T-S header.
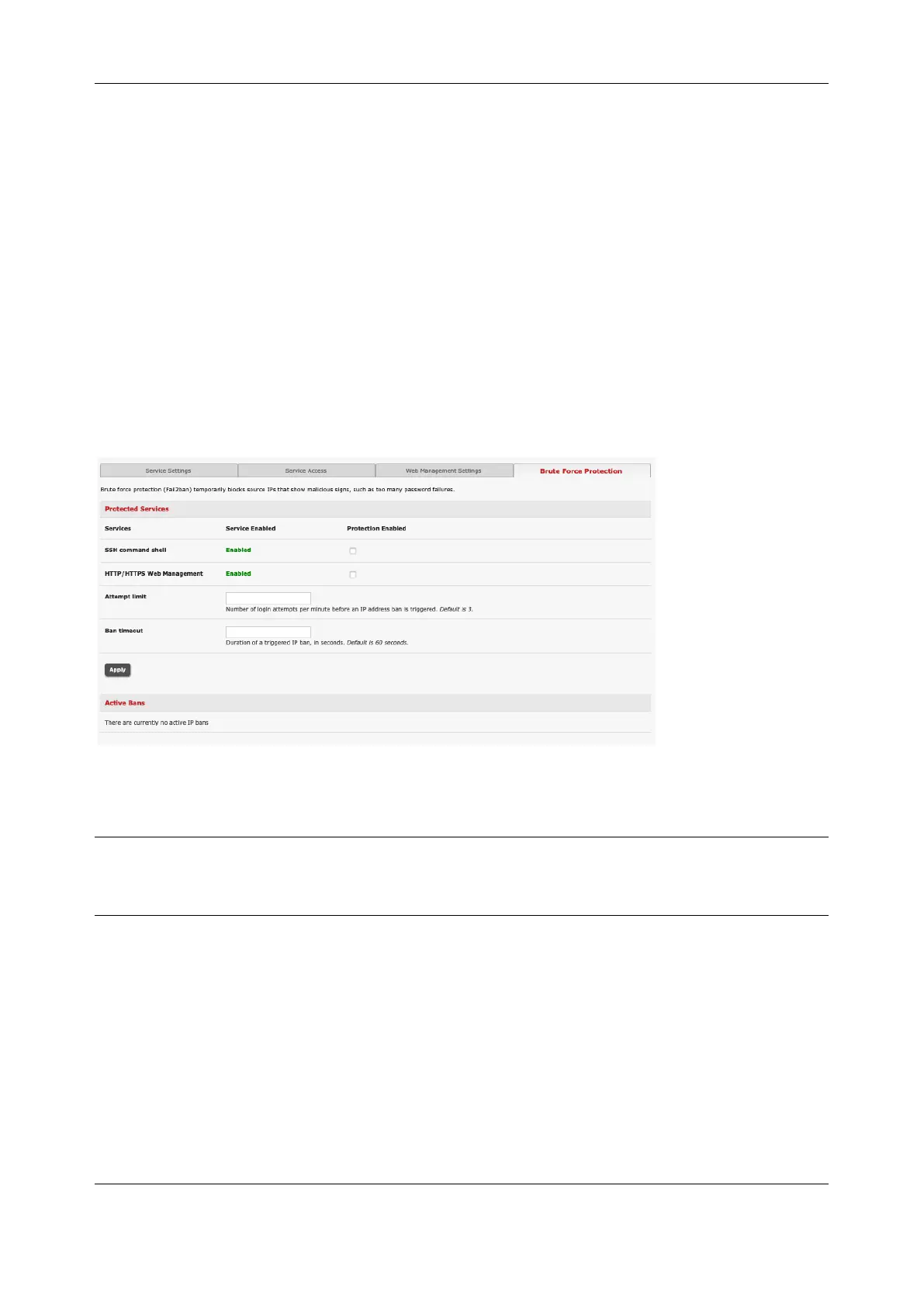
Brute Force Protection
Brute force protection (Micro Fail2ban) temporarily blocks source IPs that show malicious signs, such as
too many password failures. This may help when the device’s network services are exposed to an
untrusted network such as the public WAN and scripted attacks or software worms are attempting to
guess (brute force) user credentials and gain unauthorized access.
Brute Force Protection may be enabled for the listed services. By default, once protection is enabled 3 or
more failed connection attempts within 60 seconds from a specific source IP trigger it to be banned from
connecting for a configurable time period. Attempt limit and Ban timeout may be customized. Active Bans
are also listed and may be refreshed by reloading the page.
NOTE When running on an untrusted network, consider using a variety of strategies are used to lock
down remote access. This includes SSH public key authentication, VPN, and Firewall Rules to
whitelist remote access from trusted source networks only. See the Opengear Knowledge Base
for details.
2.5 Communications Software
You have configured access protocols for the administrator client to use when connecting to the console
server. User clients also use these protocols when accessing console server serial attached devices and
network attached hosts. You need communications software tools set up on the administrator and user
client’s computer. Opengear provides the SDT Connector as the recommended client software tool. You
may use other tools such as PuTTY and SSHTerm.
SDT Connector is a lightweight tool that enables users to securely access the Console server and various
computers, network devices, and appliances that are serially or network connected to the console server.

 Loading...
Loading...