Robustel GoRugged R3000 User Guide
RT_UG_R3000_v.4.0.0 27 March, 2017 75/136
Confidential
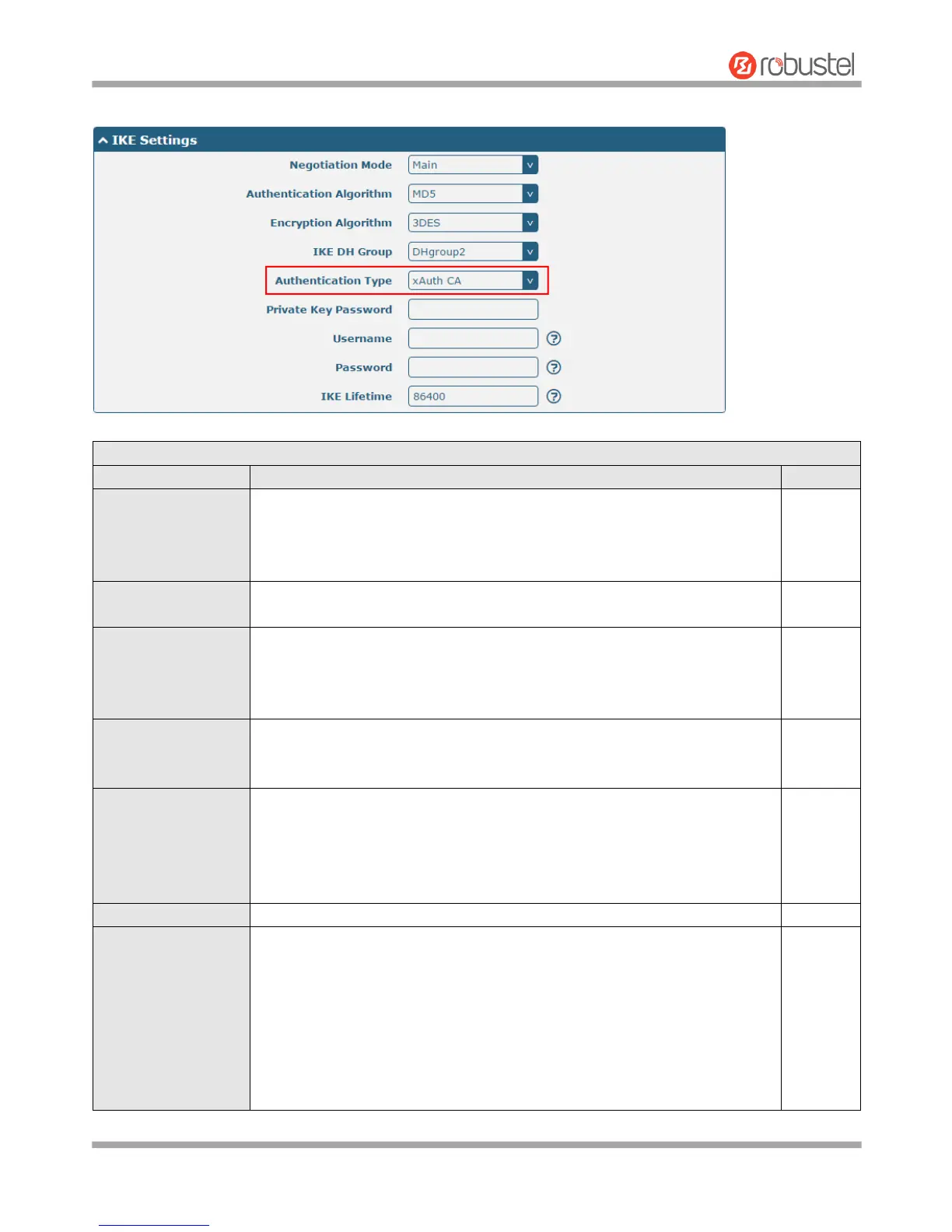
The window is displayed as below when choosing “xAuth CA” as the authentication type.
Select from “Main” and “Aggressive” for the IKE negotiation mode in phase 1.
If the IP address of one end of an IPsec tunnel is obtained dynamically, the IKE
negotiation mode must be aggressive. In this case, SAs can be established as
long as the username and password are correct.
Select from “MD5”, “SHA1”, “SHA2 256” or “SHA2 512” to be used in IKE
negotiation.
Select from “3DES”, “AES128” and “AES256”to be used in IKE negotiation.
3DES: Use 168-bit 3DES encryption algorithm in CBC mode
AES128: Use 128-bit AES encryption algorithm in CBC mode
AES256: Use 256-bit AES encryption algorithm in CBC mode
Select from “DHgroup2”, “DHgroup5”, “DHgroup14”, “DHgroup15”,
“DHgroup16”, “DHgroup17” or “DHgroup18” to be used in key negotiation
phase 1.
Select from “PSK”, “CA”, “xAuth PSK” and “xAuth CA” to be used in IKE
negotiation.
PSK: Pre-shared Key
CA: Certification Authority
xAuth: Extended Authentication to AAA server
Enter the pre-shared key.
Select from “Default”, “FQDN” and “User FQDN” for IKE negotiation.
Default: Uses an IP address as the ID in IKE negotiation
FQDN: Uses an FQDN type as the ID in IKE negotiation. If this option is
selected, type a name without any at sign (@) for the local security
gateway, e.g., test.robustel.com.
User FQDN: Uses a user FQDN type as the ID in IKE negotiation. If this
option is selected, type a name string with a sign “@” for the local
security gateway, e.g., test@robustel.com.
 Loading...
Loading...











