Configuration and operation
6.1 Security recommendations
CP 443-1 Advanced (GX30)
Manual, 03/2019, C79000-G8976-C256-05
65
If you want to later change parameters in a DB, for example a password, remember the
following: The contents of a DB with know-how protection are no longer visible and can only
be changed via the source or by direct assignment of parameters.
● Define rules for the use of devices and assignment of passwords.
● Regularly update the passwords to increase security.
● Only use passwords with a high password strength. Avoid weak passwords for example
"password1", "123456789" or similar.
● Make sure that all passwords are protected and inaccessible to unauthorized personnel.
See also the preceding section for information on this.
● Do not use one password for different users and systems.
● Use a certification authority including key revocation and management to sign certificates.
● Make sure that user-defined private keys are protected and inaccessible to unauthorized
persons.
● It is recommended that you use password-protected certificates in the PKCS #12 format
● Verify certificates and fingerprints on the server and client to prevent "man in the middle"
attacks.
● It is recommended that you use certificates with a key length of at least 2048 bits.
● Change certificates and keys immediately if there is a suspicion of compromise.
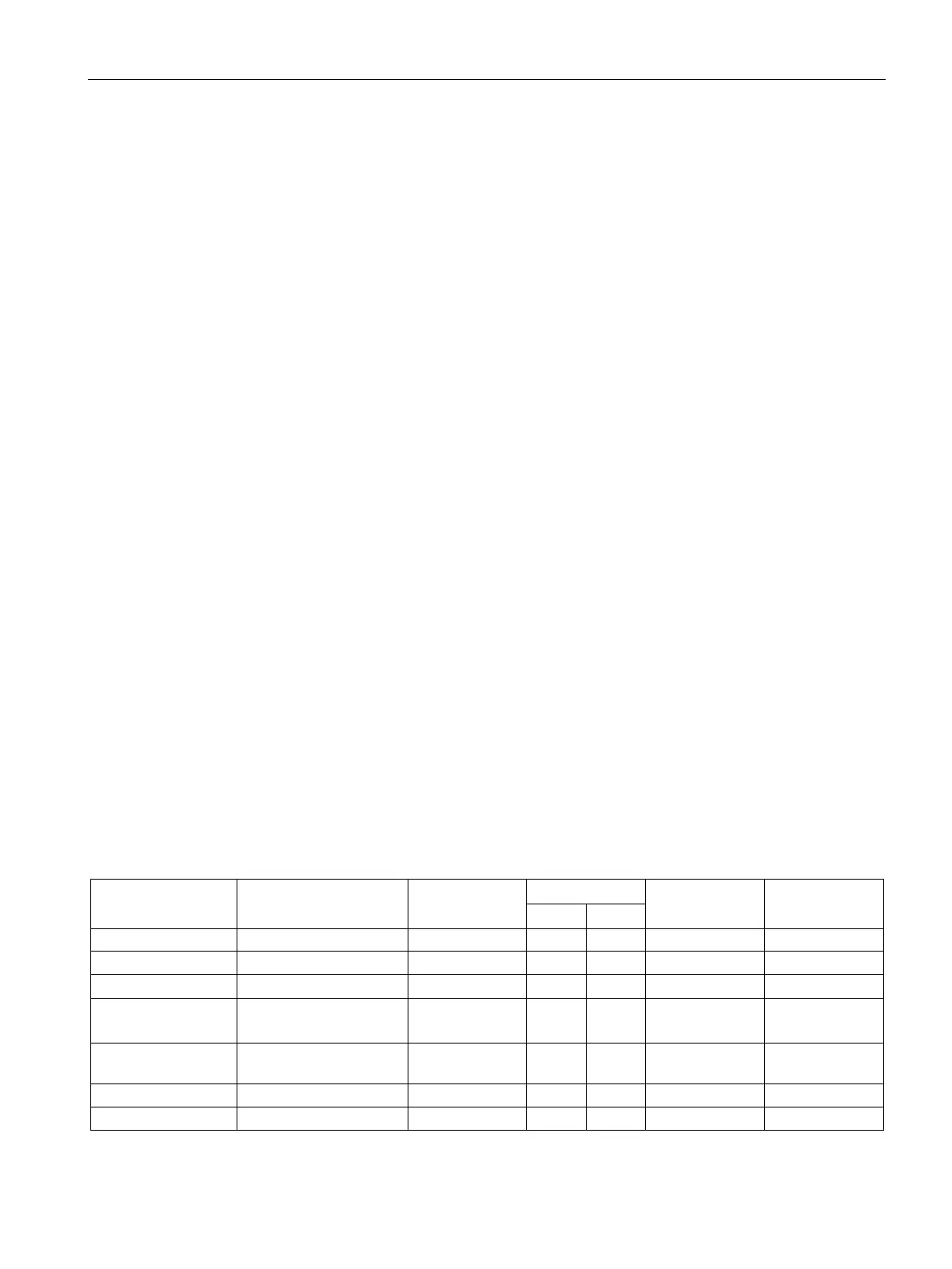
Protocols
List of available protocols
The following is a list of all available protocols and their ports through which the device can
be accessed.
TCP/443 Closed ✓ -- Yes Yes
TCP/20
Closed ✓ ✓ Yes No
UDP/161 Open ✓ -- Yes (with
Yes (with

 Loading...
Loading...











