User Guide DDOC0099-000-AH
DTS1 CSfC 5 - 15 Encryption
© 2020 Curtiss-Wright Defense Solutions Revision 6.0
5.4.2.10 Delete SWE Containers (All Partitions)
To delete all software encryption layer containers:
Command:
rmcctl -p all -D
Example of RMC Module Status
5.5 Zeroize HWE Key / Delete SWE Container / RMC Purge
• The destruction of the HWE key(s) is accomplished via zeroization.
• The SWE passphrase(s) is /are destroyed via deleting the SWE container(s).
• The RMC module data is destroyed via the rmcpurge command.
5.5.1 Zeroize HWE Key
CAUTION
DATA LOSS. Pushing the Key Clear button will zeroize the hardware encryption layer key. It will
not affect SWE passphrase(s) / data.
The goal of zeroization is to destroy the HWE key loaded in the crypto module beyond recovery by
any means.
The zeroization process is accomplished by one of the following:
• Pushing the front panel KEY CLEAR button for a minimum of 5 seconds.
• Issuing a cmkey -zero command via the CLI.
• Connecting utility connector (J2) pin 1 to ground for a minimum of 5 seconds.
• Incorrectly entering the hardware layer password three times consecutively.
Zeroization affects only the crypto module HWE key. It does not affect the RMC module. The data
on the RMC module is still accessible:
• If the RMC module can be placed in another DTS1 with the same DEK / EDEK loaded in its
crypto module.
• If the DEK can be restored / reloaded.
5.5.2 Delete SWE Container
Refer to paragraph 5.4.1.5 Delete SWE Container (Unpartitioned Disk), paragraph 5.4.2.9
Delete SWE Container (Individual Partitions), and / or paragraph 5.4.2.10 Delete SWE
Containers (All Partitions) for detailed instructions on how to use the SWE passphrase delete
(rmcctl -D) commands.
5.5.3 RMC Purge
CAUTION
DATA SECURITY. The rmcpurge command does not affect the HWE key(s).
CAUTION
DATA SECURITY. Depending on the solid-state drive manufacturer, the rmcpurge may or may not
delete the SWE passphrase(s). To be sure the passphrase has been removed, use the SWE
passphrase delete (rmcctl -D) command.
To destroy the passphrase(s) and data on the RMC module, the rmcpurge command is used.
There are two types of overwrite, Normal (-N) and Enhanced (-E). Refer to paragraph 12.3.24
rmcpurge for additional information
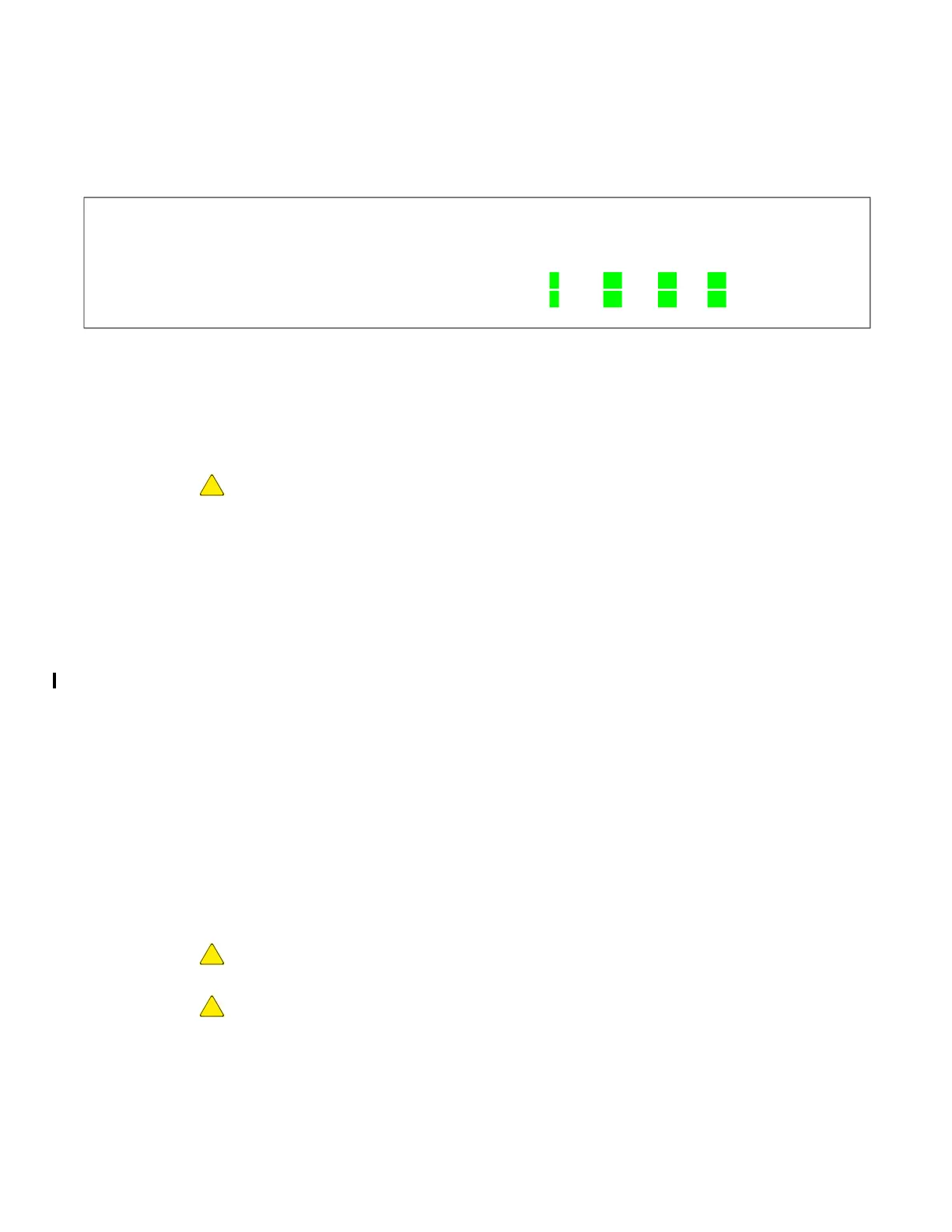
cw_dts> rmcctl
[rmcctl]
RMC_S#: ins hcryp osdr p# size serv scryp osdm fmt mnt rem mntpoint
*********************************************************************************
RMC_S0: 1 1 1 1 100GB NAS
0 na 0a na 0 rmc0p1
RMC_S0: 1 1 1 2 25 GB NAS
0 na 0a na 0 rmc0p2
[!rmcctl] OK
 Loading...
Loading...