14 Prime users
Anti-intrusion control panels
3-2
Methods of accessing the user
menu
In order for code users to access their user menus, they must first validate their codes.
This can be done by typing-in the code PIN and pressing the OK button.
FIXED LENGTH
If the installer has enabled the “Fixed length” option on a user code, the user must first press
the OK button and then type-in their PIN.
At this point, there are 3 different methods that allow first access to the user menu,
depending on how the system has been programmed, as follows:
METHOD A
The user accesses the user menu directly:
- Manage alarms
- Arm/Disarm operations
- Voice functions
- Activations
-View
-Outputs ON/OFF
- Keypad date/time
- Keypad settings
-Change PIN
- TelephoneNumbers
- Teleservice req.
- Overtime request
- Thermostat
-Nexus Nexus
-Codes
-Timers
The user can select the desired option from the menu by means of buttons
and and by pressing the OK button.
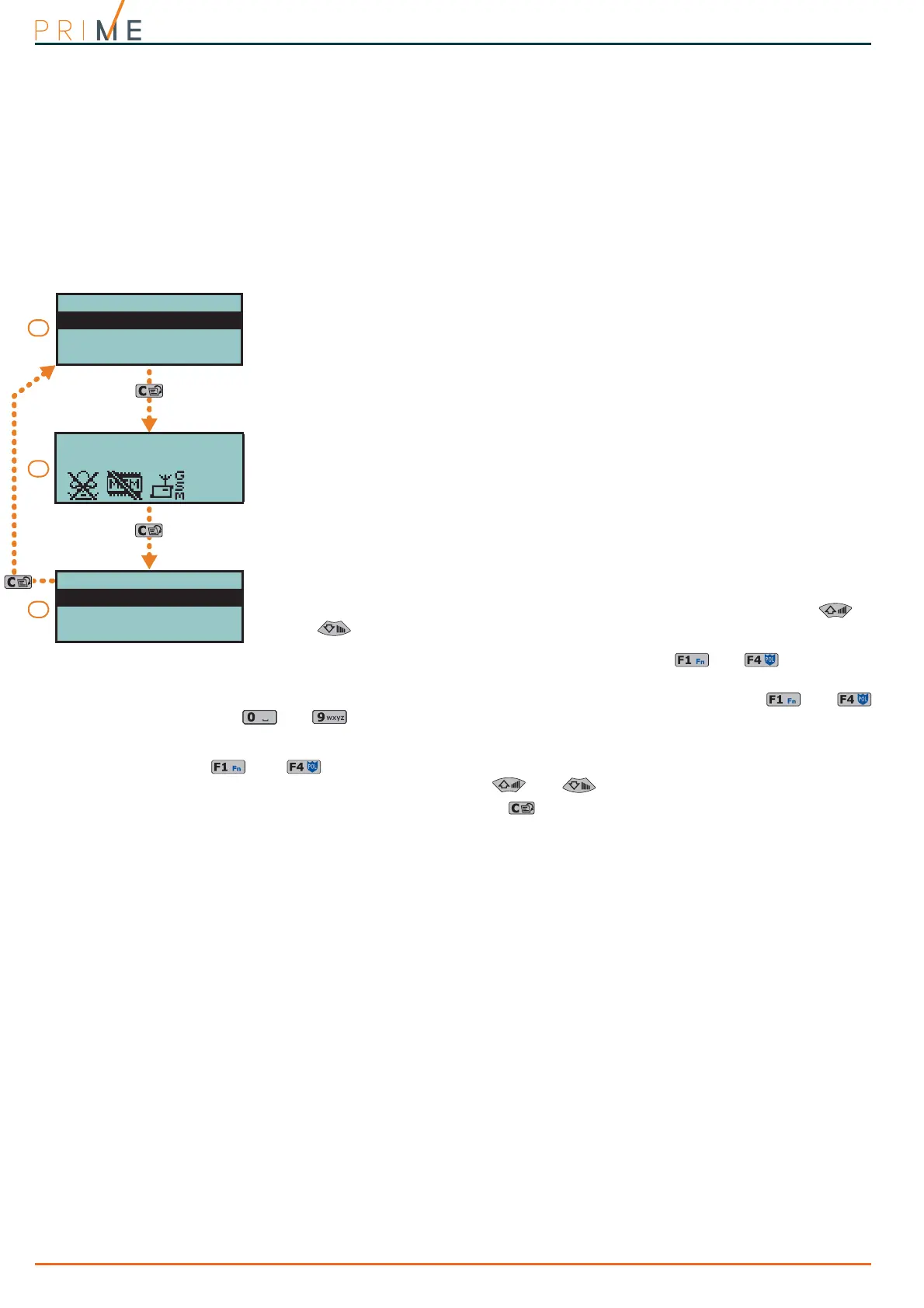
METHOD B
The keypad deletes the icons of the shortcuts assigned to buttons , ..., and replaces
them with the icons that relate to the personal shortcuts of the code.
The user can activate the desired shortcut selected from those set on buttons , ...,
and , ..., .
METHOD C
The user can access a descriptive menu of the customized shortcuts assigned to buttons
, ..., . To activate the shortcut, the user must first select the description of the
required shortcut, by means of buttons and , then press OK.
In all methods of access (A, B and C), the button allows the user to access/view the other
cases in succession, see figure.
3-3
Multi-system access
Users can access several systems using the same code/key/remote-control device. The user
code, key or remote-control device must be enrolled separately on the control panels
concerned, and can be programmed with different attributes and functions in accordance with
the requirements of each specific system.
The keys and codes provide the systems with random codes (for keys) or PINs (for codes)
which the system associates with the respective attributes and functions programmed by the
installer. For example, a user key/code may be enabled on partitions 1 and 2 on system A, on
partitions 7, 8 and 9 on system B and on partitions 4 and 5 on system C.
This operating method is possible for all keys and codes.
User Code
User Code
Manage alarms
Arm/Disarm op.
Voice functions
User Code
Stop alarms
Delete memory
Nexus status
A
B
C

 Loading...
Loading...








