Chapter 3: Serial Port, Device and User Configuration
56
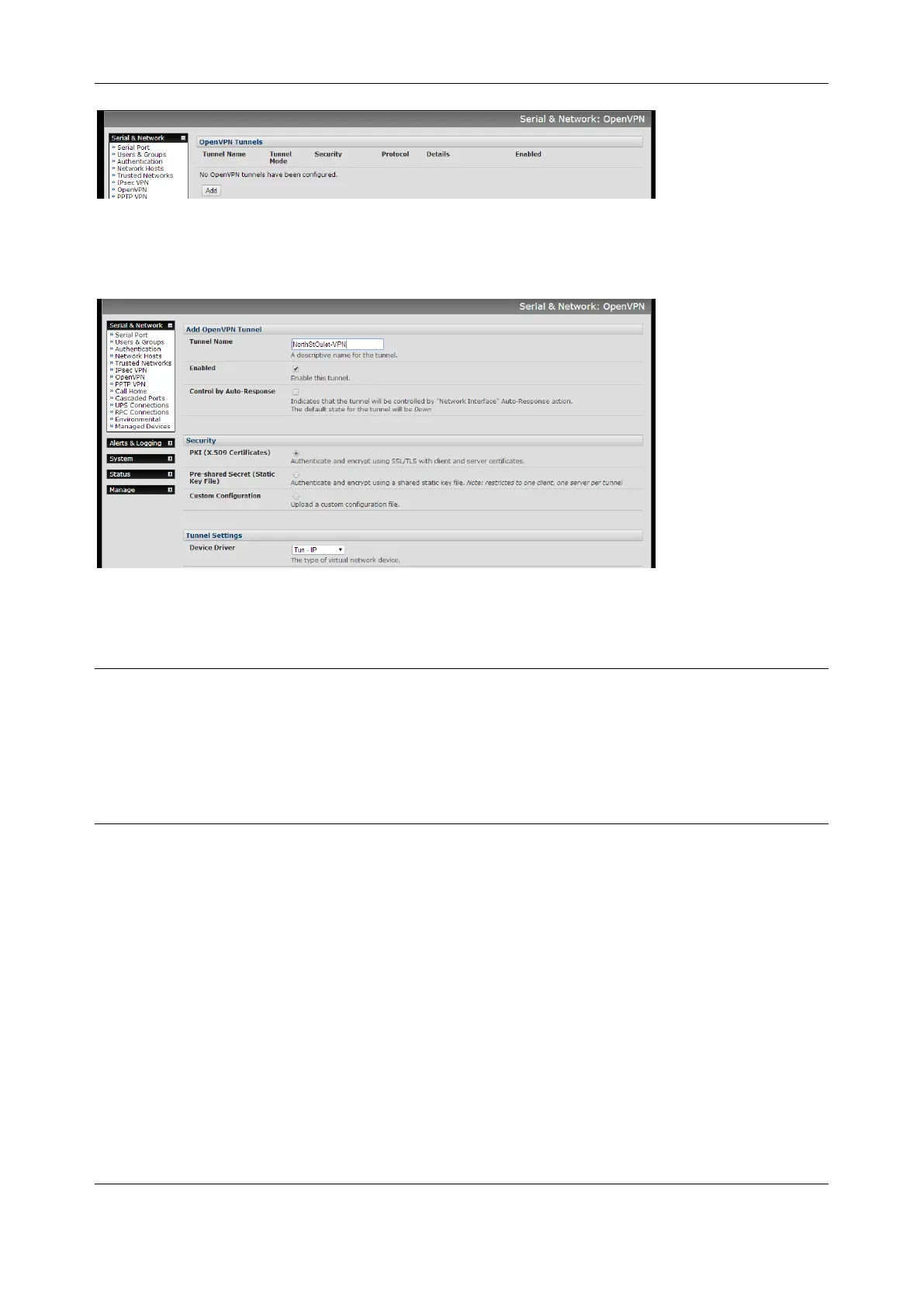
2. Click Add and complete the Add OpenVPN Tunnel screen
3. Enter any descriptive name you wish to identify the OpenVPN Tunnel you are adding, for example
NorthStOutlet-VPN
4. Select the authentication method to be used. To authenticate using certificates select PKI (X.509
Certificates) or select Custom Configuration to upload custom configuration files. Custom
configurations must be stored in /etc/config.
NOTE If you select PKI, establish:
§ Separate certificate (also known as a public key). This Certificate File is a *.crt file type
§ Private Key for the server and each client. This Private Key File is a *.key file type
§ Master Certificate Authority (CA) certificate and key which is used to sign each of the server and
client certificates. This Root CA Certificate is a *.crt file type
For a server, you may also need dh1024.pem (Diffie Hellman parameters). See
http://openvpn.net/easyrsa.html for a guide to basic RSA key management. For alternative authentication
methods see http://openvpn.net/index.php/documentation/howto.html#auth.
5. Select the Device Driver to be used, either Tun-IP or Tap-Ethernet. The TUN (network tunnel) and
TAP (network tap) drivers are virtual network drivers that support IP tunneling and Ethernet
tunneling, respectively. TUN and TAP are part of the Linux kernel.
6. Select either UDP or TCP as the Protocol. UDP is the default and preferred protocol for OpenVPN.
7. Check or uncheck the Compression button to enable or disable compression.
8. In Tunnel Mode, nominate whether this is the Client or Server end of the tunnel. When running as
a server, the console server supports multiple clients connecting to the VPN server over the same
port.

 Loading...
Loading...