Protection
6.2 Configuring access protection for the CPU
CPU 1516pro-2 PN (6ES7516-2PN00-0AB0)
60 Operating Instructions, 09/2016, A5E35873416-AA
Configuring access protection for the CPU
Introduction
The CPU offers four access levels to limit access to specific functions.
By setting up the access levels and the passwords for a CPU, you limit the functions and
memory areas that are accessible without entering a password. The individual access levels
as well as their associated passwords are specified in the object properties of the CPU.
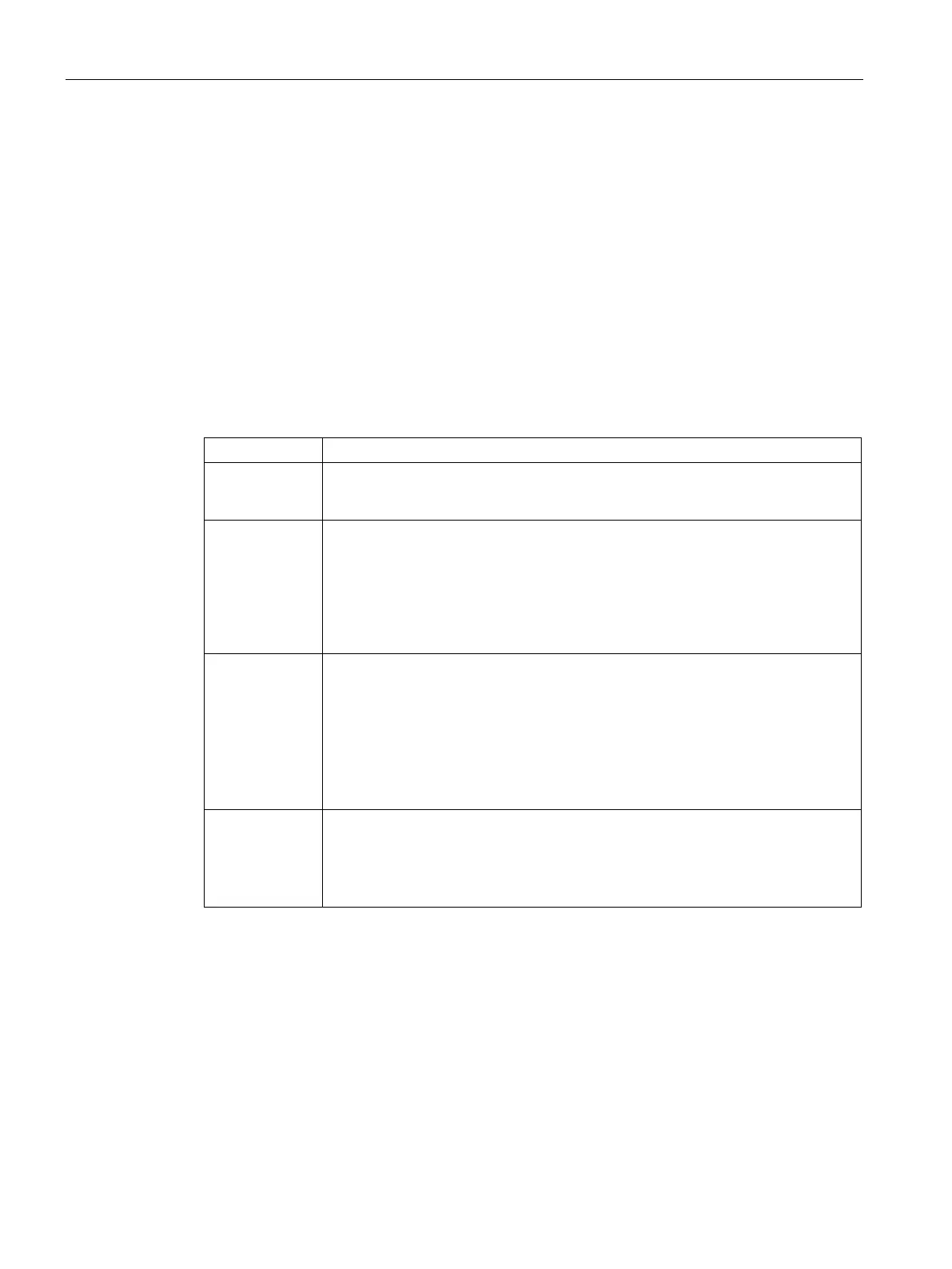
Table 6- 1 Access levels and access restrictions
Complete ac-
cess (no protec-
The hardware configuration and the blocks can be read and changed by all users.
Read access With this access level, read-only access to the hardware configuration and the
blocks is possible without entering a password, which means you can download
hardware configuration and blocks to the programming device. In addition, HMI
access and access to diagnostics data is possible.
Without entering the password, you cannot load any blocks or hardware configura-
tion into the CPU. Additionally, the following are
possible without the pass-
word: Writing test functions and firmware update (online).
HMI access With this access level only HMI access and access to diagnostics data is possible
without entering the password.
Without entering the password, you can neither load blocks and hardware configu-
ration into the CPU, nor load blocks and hardware configuration from the CPU into
the programming device.
Additionally, the following are
possible without the password: Test functions,
changing the operating mode (RUN/STOP), firmware update and display of
online/offline comparison status.
No access
(complete pro-
tection)
When the CPU has complete protection, no read or write access to the hardware
configuration and the blocks is possible (without access authorization in the form
of a password). HMI access is also not possible. The server function for PUT/GET
communication is disabled in this access level (cannot be changed).
Authentication with the password will again provide you full access to the CPU.
You can find a list of which functions are possible in the various protection levels in the
STEP 7 online help under the entry "Setting options for the protection".
 Loading...
Loading...











