IPv4 Access Control Lists (ACLs)
ACL Operation
Note on Implicit
Deny
For ACLs configured to filter inbound packets, note that Implicit Deny filters
any packets, including those with a DA specifying the switch itself. This
operation helps to prevent management access from unauthorized IP sources.
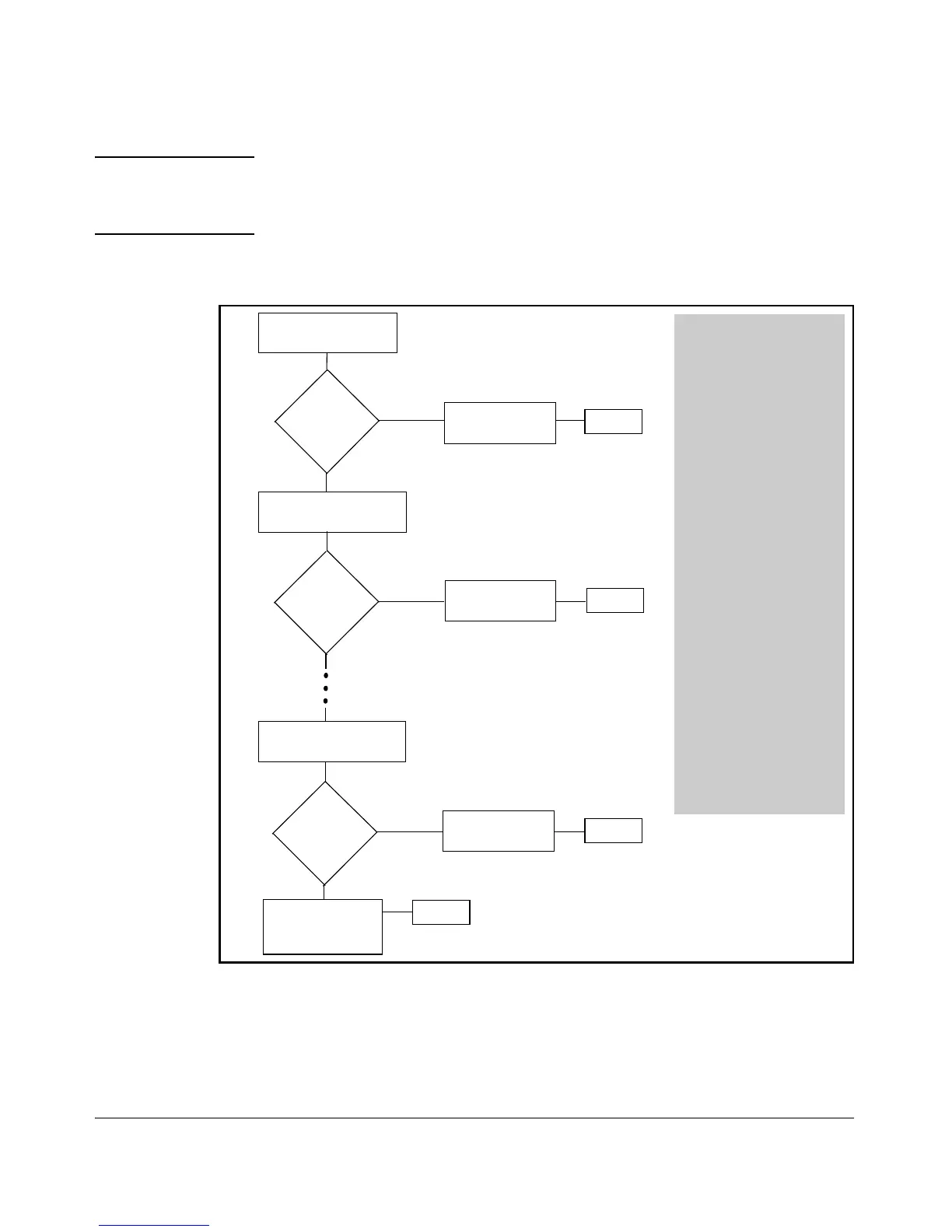
Figure 9-3. The Packet-Filtering Process in an ACL with N Entries (ACEs)
For example, suppose you want to configure an ACL on the switch (with an
ID of “100”) to invoke these policies:
1. Permit all inbound traffic on port 12 sent from IP address 11.11.11.42.
Is there a
match?
Perform action
(permit or deny).
No
Test a packet against
criteria in first ACE.
Yes
No
Yes
Deny the packet
(invoke implicit
deny any).
End
Perform action
(permit or deny).
End
End
Test the packet against
criteria in second ACE.
Is there a
match?
Test packet against
criteria in
Nth ACE.
Is there a
match?
No
Yes
End
Perform action
(permit or deny).
1. If a match is not found with
the first ACE in an ACL, the
switch proceeds to the next
ACE and so on.
2. If a match with an explicit
ACE is subsequently found,
the packet is either permit-
ted (forwarded) or denied
(dropped), depending on
the action specified in the
matching ACE. In this case
the switch ignores all sub-
sequent ACEs in the ACL.
3. If a match is not found with
any explicit ACE in the ACL,
the switch invokes the
implicit deny any at the end
of every ACL, and drops the
packet.
Note: If the list includes a
permit any entry, no
packets can reach the
implicit deny any at the end
of the list.

 Loading...
Loading...














