RADIUS Authentication, Authorization, and Accounting
Configuring the Switch for RADIUS Authentication
Using Multiple RADIUS Server Groups
The authentication and accounting features on the switch can use up to fifteen
RADIUS servers. This option allows the RADIUS servers to be put into groups.
Up to 5 groups of 3 RADIUS servers each can be configured. The authentica-
tion and accounting features can choose which RADIUS server group to
communicate with. End-user authentication methods (802.1X, MAC-based
and web-based) can authenticate with different RADIUS servers from the
management interface authentication methods (console, telnet, ssh, web).
Commands
Several commands are used to support the RADIUS server group option. The
RADIUS server must be configured before it can be added to a group. See
“Configuring the Switch for RADIUS Authentication” on page 5-8 for more
information about configuring RADIUS servers.
.i
ProCurve(config)# radius-server host 10.33.18.151 acct-port 1750 key source0151
ProCurve(config)# write mem
ProCurve(config)# show radius
Status and Counters - General RADIUS Information
Deadtime(min) : 0
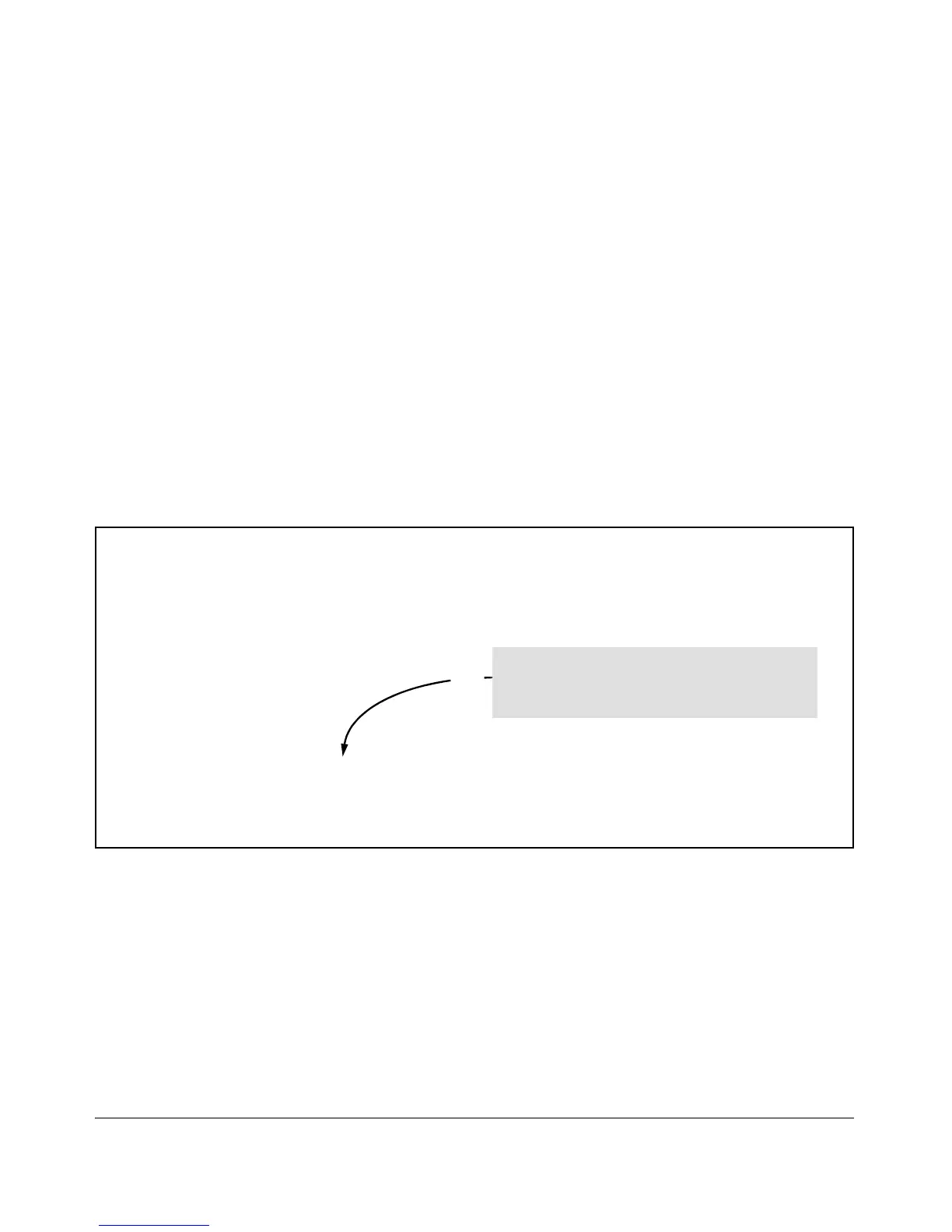
Because the radius-server command includes an
Timeout(secs) : 5
acct-port keyword with a non-default UDP port
number of 1750, the switch assigns this value as the
Retransmit Attempts : 3
UDP accounting port.
Global Encryption Key :
Dynamic Authorization UDP Port : 3799
Auth Acct DM/ Time
Server IP Addr Port Port CoA Window Encryption Key OOBM
--------------- ---- ---- --- ------ -------------------------------- ----
-
10.33.18.151 1812 1750 No 10 source0151 No
Figure 5-8. Example of RADIUS Server Group Command Output
Syntax: [no] radius-server host < ip-address >
Adds a server to the RADIUS configuration or (with no) deletes
a server from the configuration. You can configure up to
fifteen RADIUS server addresses. The switch uses the first
server it successfully accesses.
5-21

 Loading...
Loading...














