Chapter 5. Disk Security with Full Disk Encryption drives 267
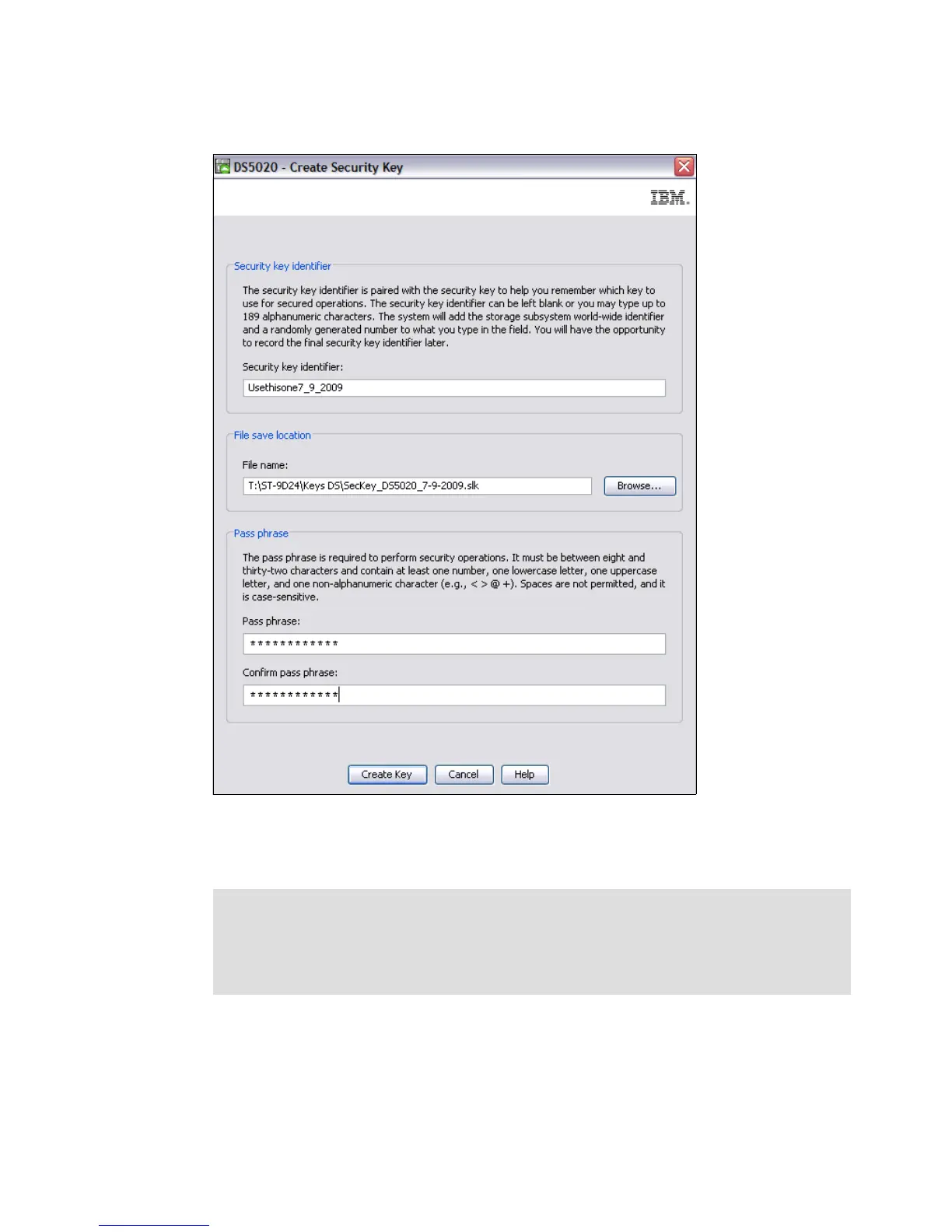
The window shown in Figure 5-7 opens, where you need to complete the fields.
Figure 5-7 Requirements displayed for the security key creation
The key location default is in the user’s local PC directory. We strongly advise that the key be
copied and kept in a safe location.
Tip: The best practice is to store the security key file with your key management policies
along with the pass phrase. It is important to record and remember where this file is stored
because the security key file is required along with pass phrase when a drive is moved
from one storage subsystem to another or when both controllers in a storage subsystem
are replaced at the same time.

 Loading...
Loading...











