522 IBM Midrange System Storage Hardware Guide
Security
Several security mechanisms are provided by the DS5000 storage subsystem when an iSCSI
Host Interface Card (HIC) is present that is not applicable to standard FC communications.
Because the storage subsystems can now be employed on a relatively unsecure Ethernet
network topology, additional security might be required to comply with organizational or
corporate network security guidelines. You can configure both iSNS and CHAP authentication
on the DS5000 storage subsystems.
Internet Storage Name Service
The Internet Storage Name Service (iSNS) protocol allows for automated discovery,
management, and configuration of iSCSI devices on TCP/IP network. In a typical
iSCSI-based storage subsystem without iSNS configured, any and all iSCSI session requests
to the target may be allowed from devices on the iSCSI SAN subject to restrictions in place
using the partitioning element of the DS5000 series of storage subsystems. The iSNS servers
offer additional security services through explicitly defined initiator-to-target mappings and
simplified asset locators, similar to that provided by DNS and WINS for IP address lookup
facilities. Most modern operating systems allow iSNS services to be established. The DS5000
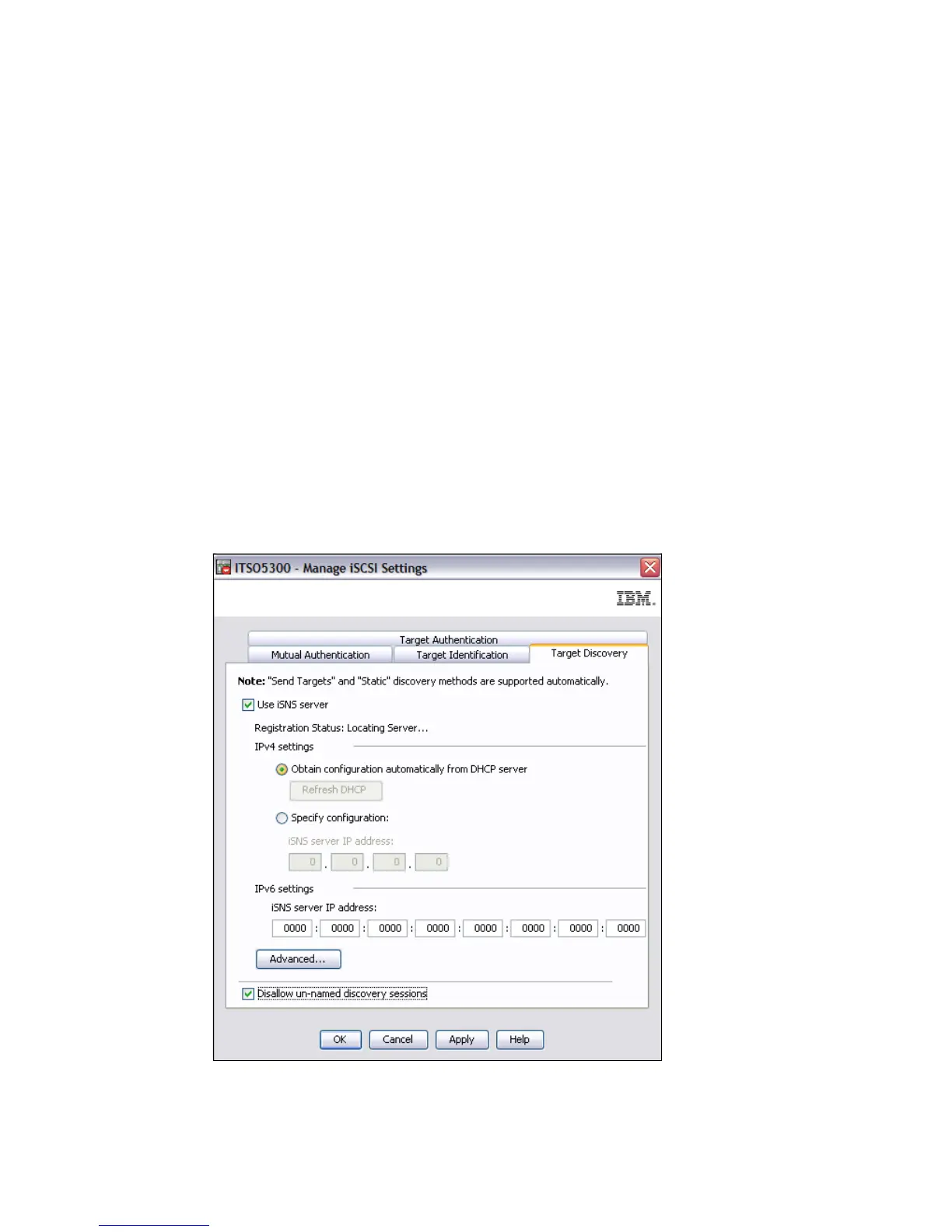
series of storage subsystems support this capability as well. Figure B-5 shows the
configurations settings where the iSNS box has been checked, allowing the iSNS server to be
defined.
Figure B-5 iSNS settings

 Loading...
Loading...











