Chapter 5. Disk Security with Full Disk Encryption drives 271
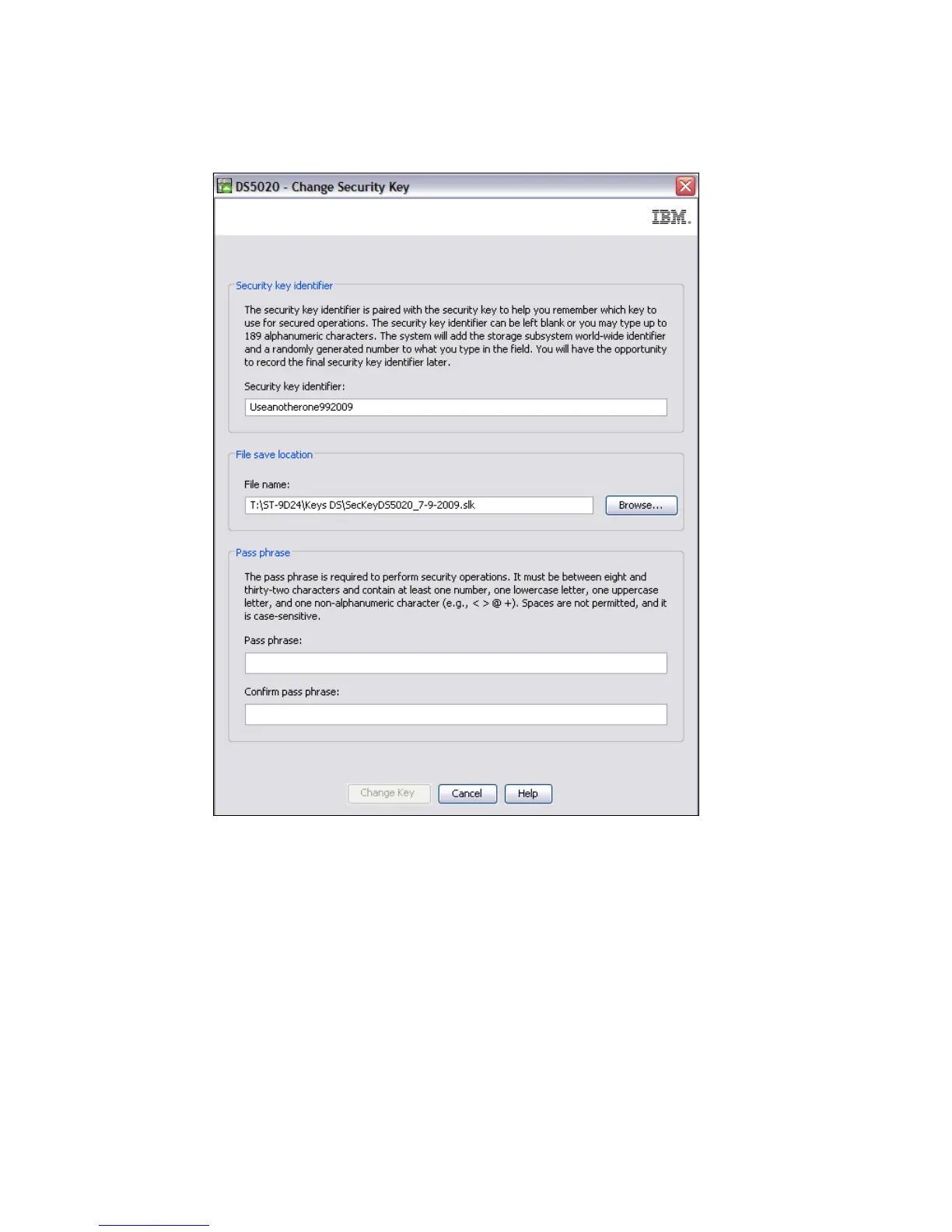
The window shown in Figure 5-12 opens and you are prompted to add a security identifier
(optional), a location to store the key file in, and a pass phrase.
Figure 5-12 Change Security Key options
The new security key is generated by the controller firmware and is hidden in the storage
subsystem. The new security key replaces the previous key that was used to unlock the
security-enabled FDE drives in the storage subsystem. The controller negotiates with all of
the security-enabled FDE drives for the new key.
The original security key is also stored in the storage subsystem for protection in case
something prevents the controllers from completing the negotiation of the new security key
with the security-enabled FDE drives (for example, loss of storage subsystem power during
the key change process). If this happens, you must change the security key so that only one
version of the security key is used to unlock all drives in a storage subsystem. The original
key is stored in the storage subsystem only. It cannot be changed directly or exported to a
security key backup file.

 Loading...
Loading...











