Setting up the Configuration
Environment
290
A.4
Preparing access via SSH
UM Basic Configuration L3P
Release
7.1
12/2011
A.4.3 Access through an SSH
One way of accessing your device through an SSH is by using the PuTTY
program. This program is provided on the product-CD.
Start the program by double-clicking on it.
Enter the IP address of your device.
Select "SSH".
Click on Open to establish the connection to your device.
Depending on the device, and the time at which the SSH was configured,
it may take up to a minute to establish the connection.
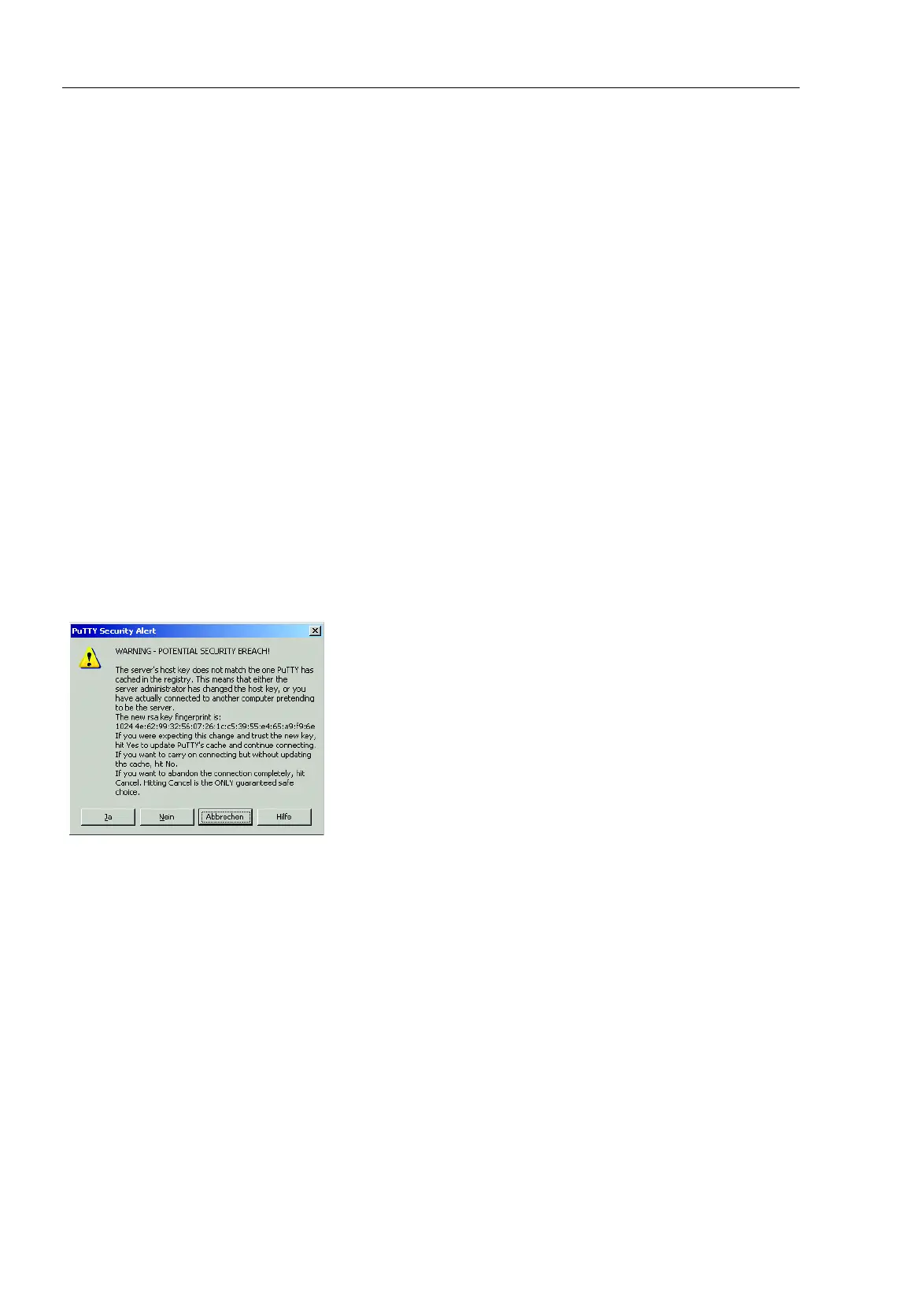
When connection is almost completed, the PuTTY program displays a
security alarm message and gives you the option of checking the key
fingerprint.
Figure 82: Security alert prompt for the fingerprint
Check the fingerprint in order to ensure that you have actually connected
to the correct device. You will find the fingerprint of your key in the "Key
fingerprint" box in the PuTTY key generator (see fig. 81).
If the fingerprint matches that of your key, click on "Yes".
PuTTY also displays another security alarm message at the defined warning
threshold.
 Loading...
Loading...











