7-17
Using Passwords, Port Security, and Authorized IP Managers To Protect Against Unauthorized Access
Configuring and Monitoring Port Security
Using Passwords, Port
Security, and Authorized IP
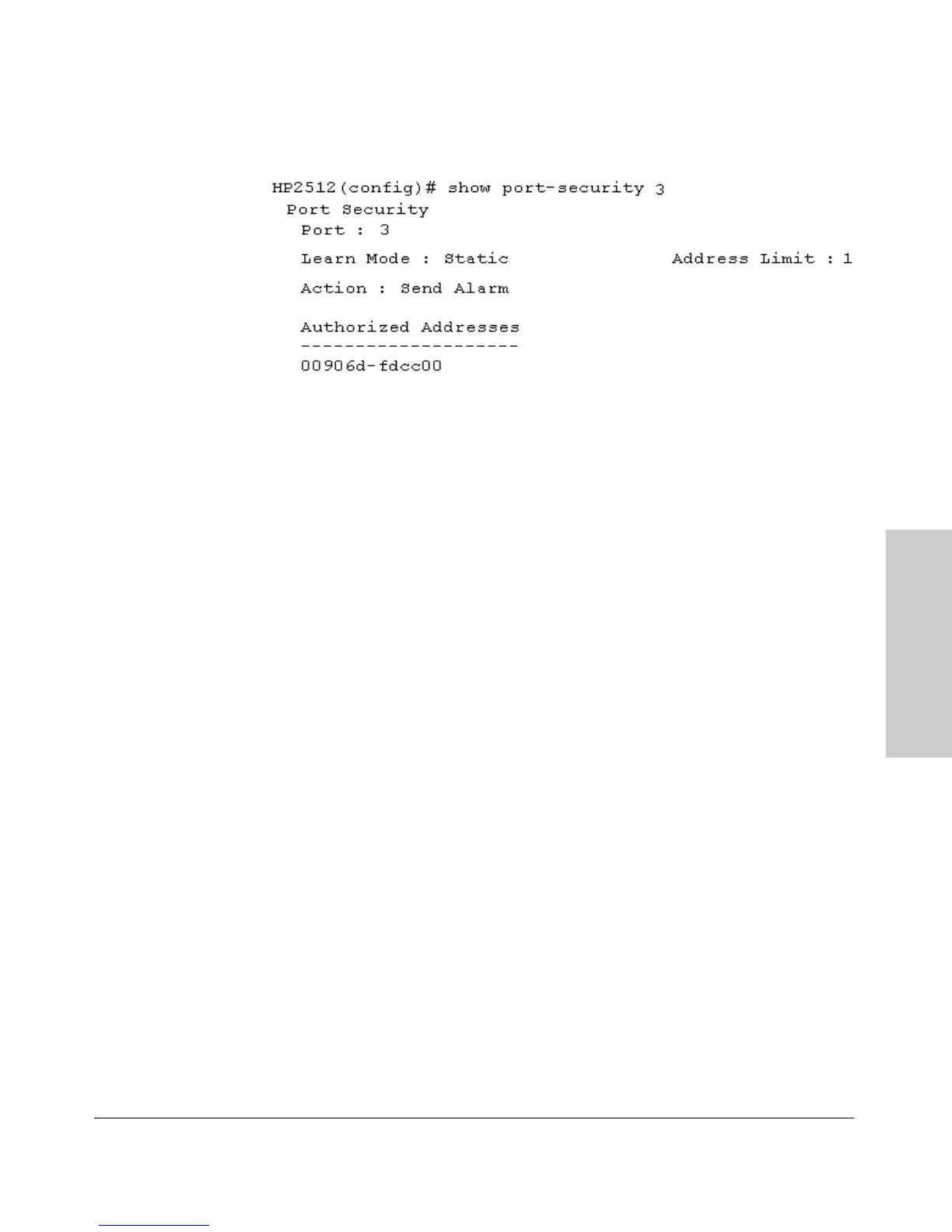
Figure 7-5. Example of the Port Security Configuration Display for a Single Port
The following command example shows the option for entering a range of
ports, including a series of non-contiguous ports. Note that no spaces are
allowed in the port number portion of the command string:
HP2512(config)# show port-security 1-3,6,8
CLI: Configuring Port Security
Using the CLI, you can:
■ Configure port security and edit security settings.
■ Add or delete devices from the list of authorized addresses for one or
more ports.
■ Clear the Intrusion flag on specific ports
Syntax:
port-security <port-list>
[learn-mode continuous]
[learn-mode static]
[address-limit <integer>]
[mac-address <mac-addr>] [<mac-addr> . . . <mac-addr>]
[action <none | send-alarm | send-disable>]
[clear-intrusion-flag]
no port-security <port-list> mac-address <mac-addr> [<mac-addr> . . .
<mac-addr>]
For information on the individual control parameters, see the Port Security
Parameter tables on pages 7-14 and 7-15.

 Loading...
Loading...











