10-5
Cisco Aironet 1100 Series Access Point Installation and Configuration Guide
OL-2851-01
Chapter 10 Configuring Authentication Types
Understanding Authentication Types
MAC Address Authentication to the Network
The access point relays the wireless client device’s MAC address to a RADIUS server on your network,
and the server checks the address against a list of allowed MAC addresses. If you don’t have a RADIUS
server on your network, you can create the list of allowed MAC addresses on the access point’s Address
Filters page. Devices with MAC addresses not on the list are not allowed to authenticate. Intruders can
create counterfeit MAC addresses, so MAC-based authentication is less secure than EAP authentication.
However, MAC-based authentication provides an alternate authentication method for client devices that
do not have EAP capability. See the “Assigning Authentication Types to an SSID” section on page 10-6
for instructions on enabling MAC-based authentication.
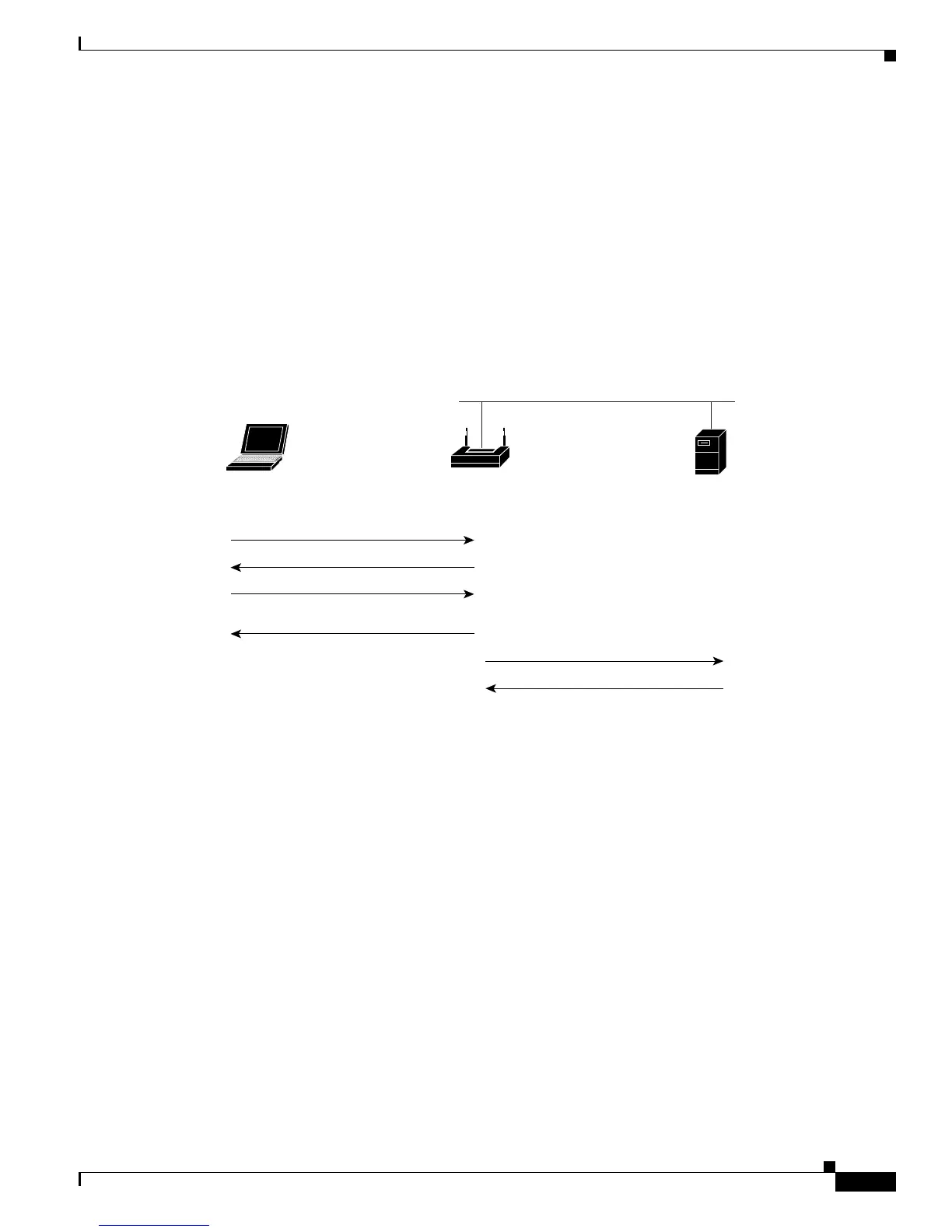
Figure 10-4 shows the authentication sequence for MAC-based authentication.
Figure 10-4 Sequence for MAC-Based Authentication
Combining MAC-Based, EAP, and Open Authentication
You can set up the access point to authenticate client devices using a combination of MAC-based and
EAP authentication. When you enable this feature, client devices that associate to the access point using
802.11 open authentication first attempt MAC authentication; if MAC authentication succeeds, the client
device joins the network. If MAC authentication fails, the access point waits for the client device to
attempt EAP authentication. See the “Assigning Authentication Types to an SSID” section on page 10-6
for instructions on setting up this combination of authentications.
Access point
or bridge
Wired LAN
Client
device
Server
1. Authentication request
2. Authentication success
3. Association request
4. Association response
(block traffic from client)
5. Authentication request
6. Success
7. Access point or bridge unblocks
traffic from client
65584

 Loading...
Loading...











