The routes you define on this page are for the data interfaces only. They do not impact the
management interface. Set the management gateway on Management > Settings > Management
Access.
Note
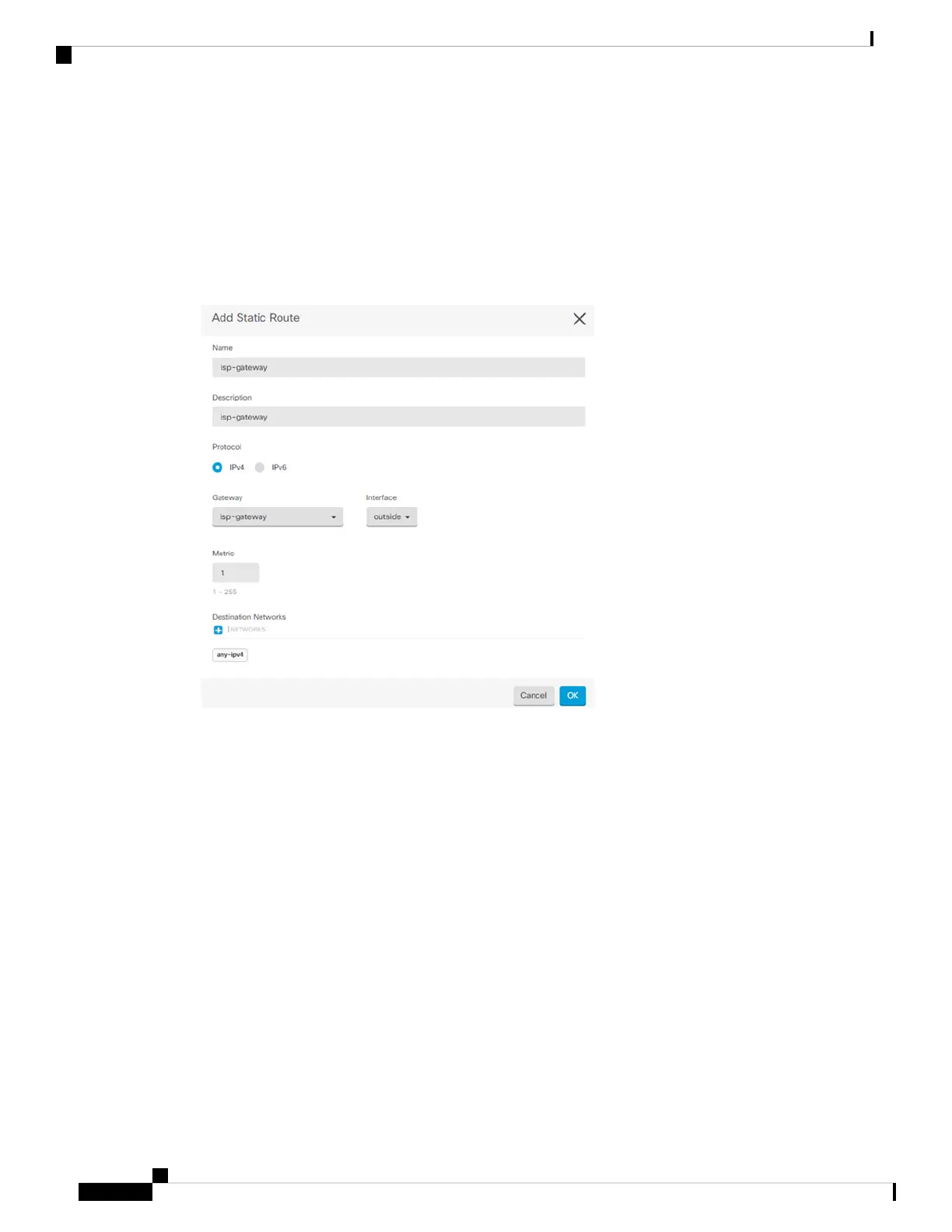
The following example shows a default route for IPv4. In this example, isp-gateway is a network object that
identifies the IP address of the ISP gateway (you must obtain the address from your ISP). You can create this
object by clicking Create New Object at the bottom of the Gateway drop-down list.
Figure 24: Default Route
Step 8 Choose Management > Policy and configure the security policies for the network.
The initial setup enables traffic flow between the inside-zone and outside-zone, and interface NAT for all
interfaces when going to the outside interface. Even if you configure new interfaces, if you add them to the
inside-zone object, the access control rule automatically applies to them.
However, if you have multiple inside interfaces, you need an access control rule to allow traffic flow from
inside-zone to inside-zone. If you add other security zones, you need rules to allow traffic to and from those
zones. These would be your minimum changes.
In addition, you can configure other policies to provide additional services, and fine-tune NAT and access
rules to get the results that your organization requires. You can configure the following policies:
• SSL Decryption—If you want to inspect encrypted connections (such as HTTPS) for intrusions, malware,
and so forth, you must decrypt the connections. Use the SSL decryption policy to determine which
connections need to be decrypted. The system re-encrypts the connection after inspecting it.
• Identity—If you want to correlate network activity to individual users, or control network access based
on user or user group membership, use the identity policy to determine the user associated with a given
source IP address.
Cisco Firepower 1100 Getting Started Guide
56
Firepower Threat Defense Deployment with CDO
Configure the Device in CDO

 Loading...
Loading...











