HP NonStop SSH Reference Manual SSHCOM Command Reference • 137
• Be the owner of the underlying Safeguard user ID of <user-or-alias> or be the group manager of the owner of
the underlying Safeguard user ID of <user-or-alias>
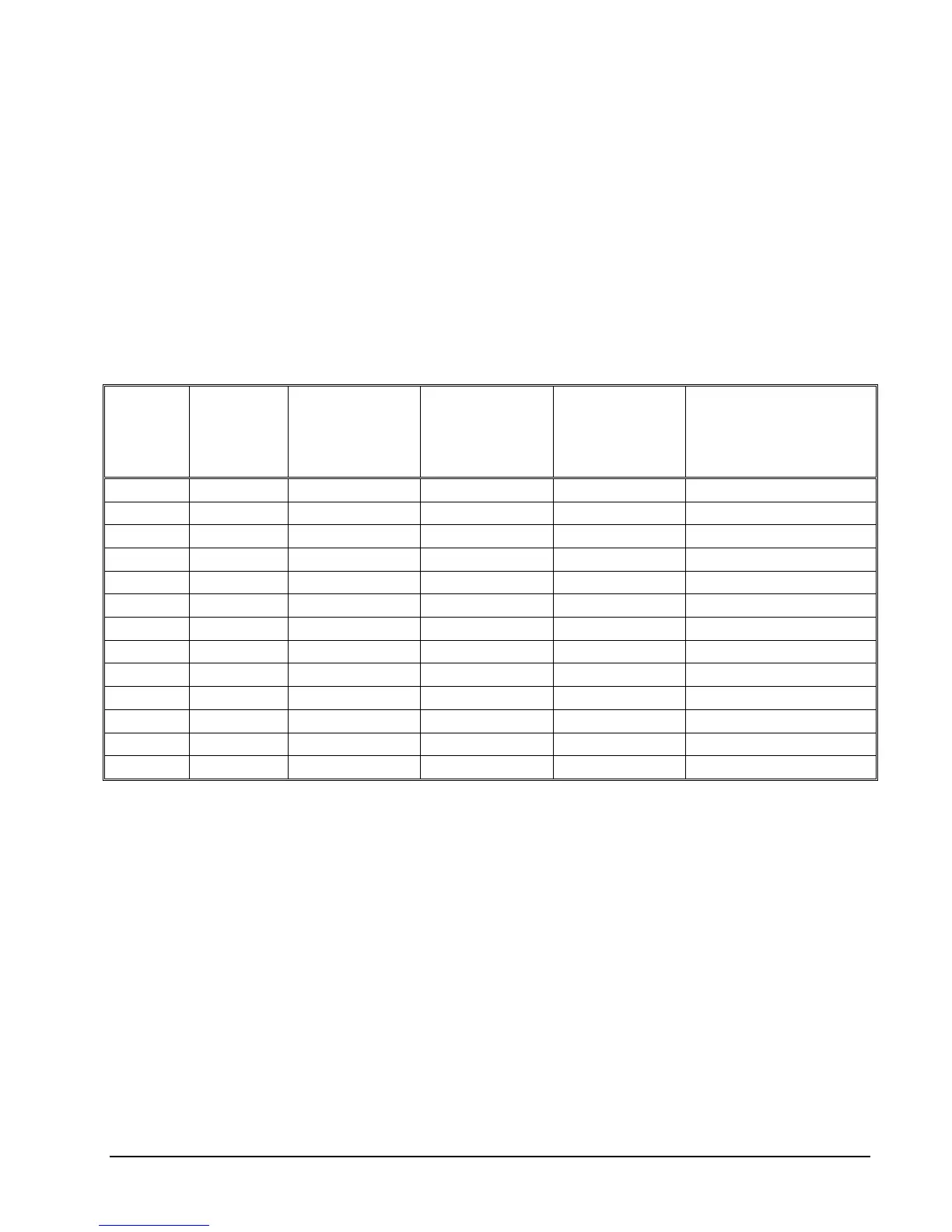
SSHCOM Access Summary
Shortcuts used in the following table:
• 'SUPER' - SUPER.SUPER
• 'OU' - OBJECTTYPE USER
• 'OUR' - OBJECTTYPE USER RECORD
• 'FullSA' - FULLSSHCOMACCESSUSERi/GROUPj
• 'PartialSA' - PARTIALSSHCOMACCESSUSERk/GROUPn
User is
'SUPER'
(Yes/No)
Thawed
'OU' exists
(Yes/No)
User configured
in 'OUR'
(No / Create /
DENY Create /
Not Applicable)
User included in
'FullSA'
configuration
(Yes / No / Not
Applicable)
User included in
'PartialSA'
configuration
(Yes/No)
Allowed USER Commands
(All / Alter&Info / None)
Yes No N/A N/A N/A All
Yes Yes No N/A N/A All
Yes Yes Create N/A N/A All
Yes Yes DENY Create N/A No None
Yes Yes DENY Create N/A Yes Alter&Info
No No N/A No No None
No No N/A No Yes Alter&Info
No No N/A Yes N/A All
No Yes No N/A No None
No Yes No N/A Yes Alter&Info
No Yes Create N/A N/A All
No Yes DENY Create N/A No None
No Yes DENY Create N/A Yes Alter&Info
Ownership and Management of Client Mode Entities
In release 89 a finer granularity for access and administration of mode client records was introduced. In previous releases
client mode records were owned by a Guardian user identifier. Even when logged on as alias the underlying Guardian
identifier was used to add and retrieve KEY, PASSWORD and KNOWNHOST records. The philosophy behind this
assumed that one person used a specific Guardian user identifier as well as the configured aliases for that Guardian user
identifier. This approach is consistent with the general security on NonStop (ACL, file security, etc.), which is based on
the Guardian user identifier.
As each alias has its own password it is possible to create a NonStop environment where different persons use different
aliases pointing to the same Guardian user identifier. In such an environment storing KEY, PASSWORD and
KNOWNHOST records under the same user id represents a security problem:
Assuming aliases a1 and a2 exist, both configured with underlying Guardian user identifier grp1.usr1. If alias a1 stored a
password for remote host h1 and remote user u1 in the client mode database (under grp1.usr1), then alias a2 can connect
to host h1 specifying remote user u1 using the stored password entry, i.e. alias a2 gets access to remote host h1 without
knowing the password of remote user u1.

 Loading...
Loading...











