Chapter 15 - Configuring IPsec VPN
Showing IPsec Status
1 interface lo/lo 127.0.0.1
2 interface eth1/eth1 10.0.0.253
3 interface eth2/eth2 204.50.190.89
4 interface w1ppp/w1ppp 206.186.238.138
5 %myid = (none)
6 debug none
7 algorithm ESP encrypt: id=2, name=ESP_DES, ivlen=8, keysizemin=64, keysizemax=64
8 algorithm ESP encrypt: id=3, name=ESP_3DES, ivlen=8, keysizemin=192, keysizemax=192
9 algorithm ESP encrypt: id=7, name=ESP_BLOWFISH, ivlen=8, keysizemin=40, keysizemax=448
10 algorithm ESP encrypt: id=11, name=ESP_NULL, ivlen=0, keysizemin=0, keysizemax=0
11 algorithm ESP encrypt: id=12, name=ESP_AES, ivlen=8, keysizemin=128, keysizemax=256
12 algorithm ESP encrypt: id=252, name=ESP_SERPENT, ivlen=8, keysizemin=128, keysizemax=256
13 algorithm ESP encrypt: id=253, name=ESP_TWOFISH, ivlen=8, keysizemin=128, keysizemax=256
14 algorithm ESP auth attr: id=1, name=AUTH_ALGORITHM_HMAC_MD5, keysizemin=128, keysizemax=128
15 algorithm ESP auth attr: id=2, name=AUTH_ALGORITHM_HMAC_SHA1, keysizemin=160, keysizemax=160
16 algorithm ESP auth attr: id=5, name=AUTH_ALGORITHM_HMAC_SHA2_256, keysizemin=256, keysizemax=256
17 algorithm ESP auth attr: id=251, name=(null), keysizemin=0, keysizemax=0
18 algorithm IKE encrypt: id=7, name=OAKLEY_AES_CBC, blocksize=16, keydeflen=128
19 algorithm IKE encrypt: id=5, name=OAKLEY_3DES_CBC, blocksize=8, keydeflen=192
20 algorithm IKE hash: id=2, name=OAKLEY_SHA, hashsize=20
21 algorithm IKE hash: id=1, name=OAKLEY_MD5, hashsize=16
22 algorithm IKE dh group: id=2, name=OAKLEY_GROUP_MODP1024, bits=1024
23 algorithm IKE dh group: id=5, name=OAKLEY_GROUP_MODP1536, bits=1536
24 algorithm IKE dh group: id=14, name=OAKLEY_GROUP_MODP2048, bits=2048
25 algorithm IKE dh group: id=15, name=OAKLEY_GROUP_MODP3072, bits=3072
26 algorithm IKE dh group: id=16, name=OAKLEY_GROUP_MODP4096, bits=4096
27 algorithm IKE dh group: id=17, name=OAKLEY_GROUP_MODP6144, bits=6144
28 algorithm IKE dh group: id=18, name=OAKLEY_GROUP_MODP8192, bits=8192
29 stats db_ops.c: {curr_cnt, total_cnt, maxsz} :context={0,6144,36} trans={0,6144,336} attrs={0,6144,224}
30 "openswantest": 10.0.0.0/8===204.50.190.89...204.50.190.91===192.168.1.0/24; erouted; eroute owner: #2997
31 "openswantest": ike_life: 3600s; ipsec_life: 28800s; rekey_margin: 540s; rekey_fuzz: 100%; keyingtries: 0
32 "openswantest": policy: PSK+ENCRYPT+TUNNEL+PFS+UP; prio: 24,8; interface: eth2;
33 "openswantest": newest ISAKMP SA: #3093; newest IPsec SA: #2997;
34 "openswantest": IKE algorithms wanted: 5_000-1-5, 5_000-1-2, 5_000-2-5, 5_000-2-2, flags=-strict
35 "openswantest": IKE algorithms found: 5_192-1_128-5, 5_192-1_128-2, 5_192-2_160-5, 5_192-2_160-2,
36 "openswantest": IKE algorithm newest: 3DES_CBC_192-MD5-MODP1536
37 "openswantest": ESP algorithms wanted: 3_000-1, 3_000-2, flags=-strict
38 "openswantest": ESP algorithms loaded: 3_000-1, 3_000-2, flags=-strict
39 "openswantest": ESP algorithm newest: AES_256-HMAC_SHA1; pfsgroup=<Phase1>
40 #3126: "openswantest" STATE_QUICK_I1 (sent QI1, expecting QR1); EVENT_RETRANSMIT in 9s
41 #3093: "openswantest" STATE_MAIN_R3 (sent MR3, ISAKMP SA established); EVENT_SA_REPLACE in 1050s; newest ISAKMP
42 #2997: "openswantest" STATE_QUICK_R2 (IPsec SA established); EVENT_SA_REPLACE in 19773s; newest IPSEC; eroute owner
43 #2997: "openswantest" esp.df9839e9@204.50.190.91 esp.8e2d7255@204.50.190.89 tun.0@204.50.190.91 tun.0@204.50.190.
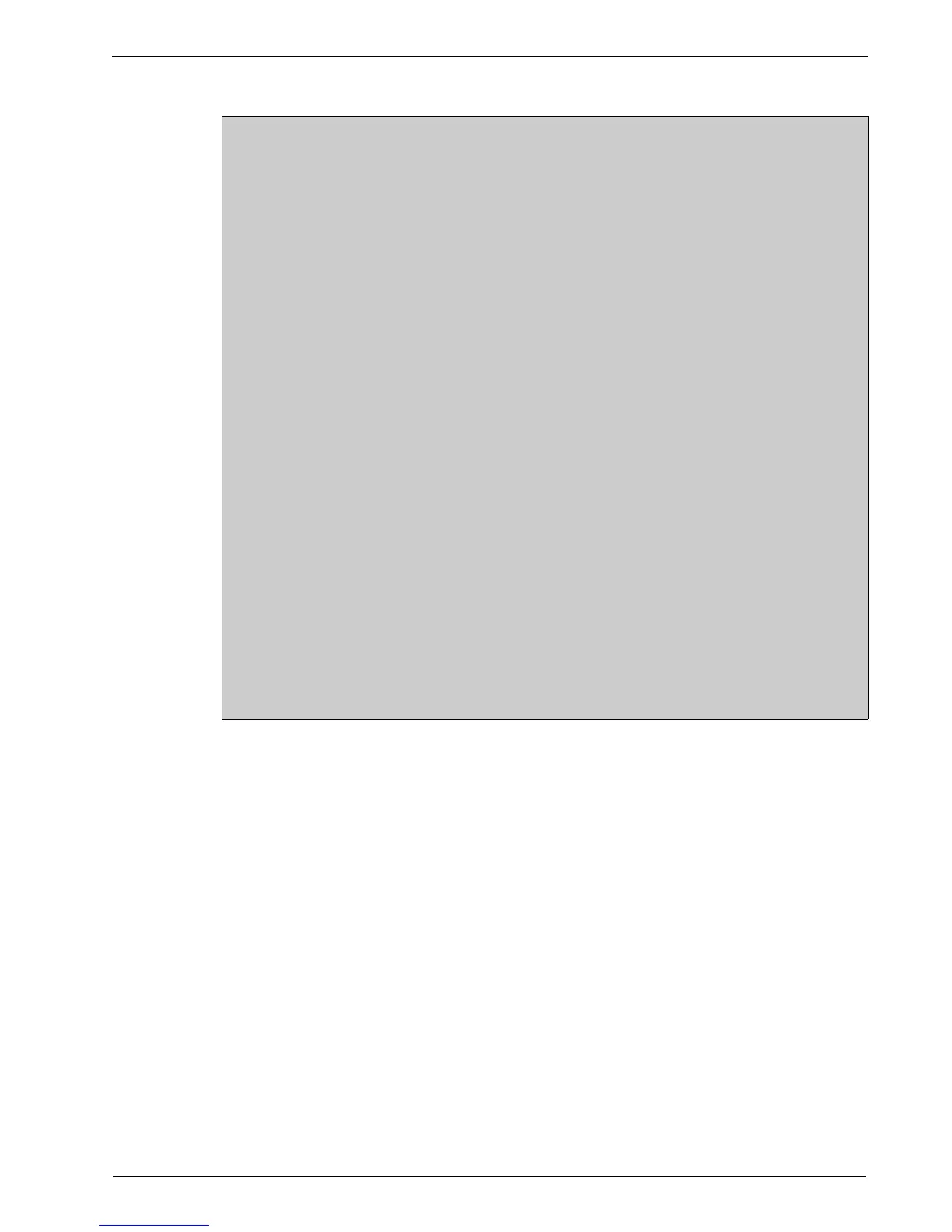
Figure 128: IPsec Status
The “IPsec Status” button produces a window of text similar to that of the above
figure (except that line numbers have been inserted for purposes of illustration).
The first group (lines 1-5) describes configured interfaces.
The second group (lines 7-17) describes ESP capabilities. In this group we can see
encryption capabilities (lines 7-13) and authentication capabilities (lines 14-17). At
least one set of values must match between the left- and right-hand side VPN devices.
This is also frequently referred to as the Phase 2 parameters, because the data
encryption process is the second and final thing to occur in establishing a VPN.
The third group (lines 18-28) describes IKE capabilities and defines the various
encrypted key exchange algorithms and their parameters. At least one set of values
must match between the left- and right-hand side VPN devices. This is also frequently
referred to as the Phase 1 parameters, because the key exchange process is the first
thing to occur in establishing a VPN.
RuggedCom 149

 Loading...
Loading...