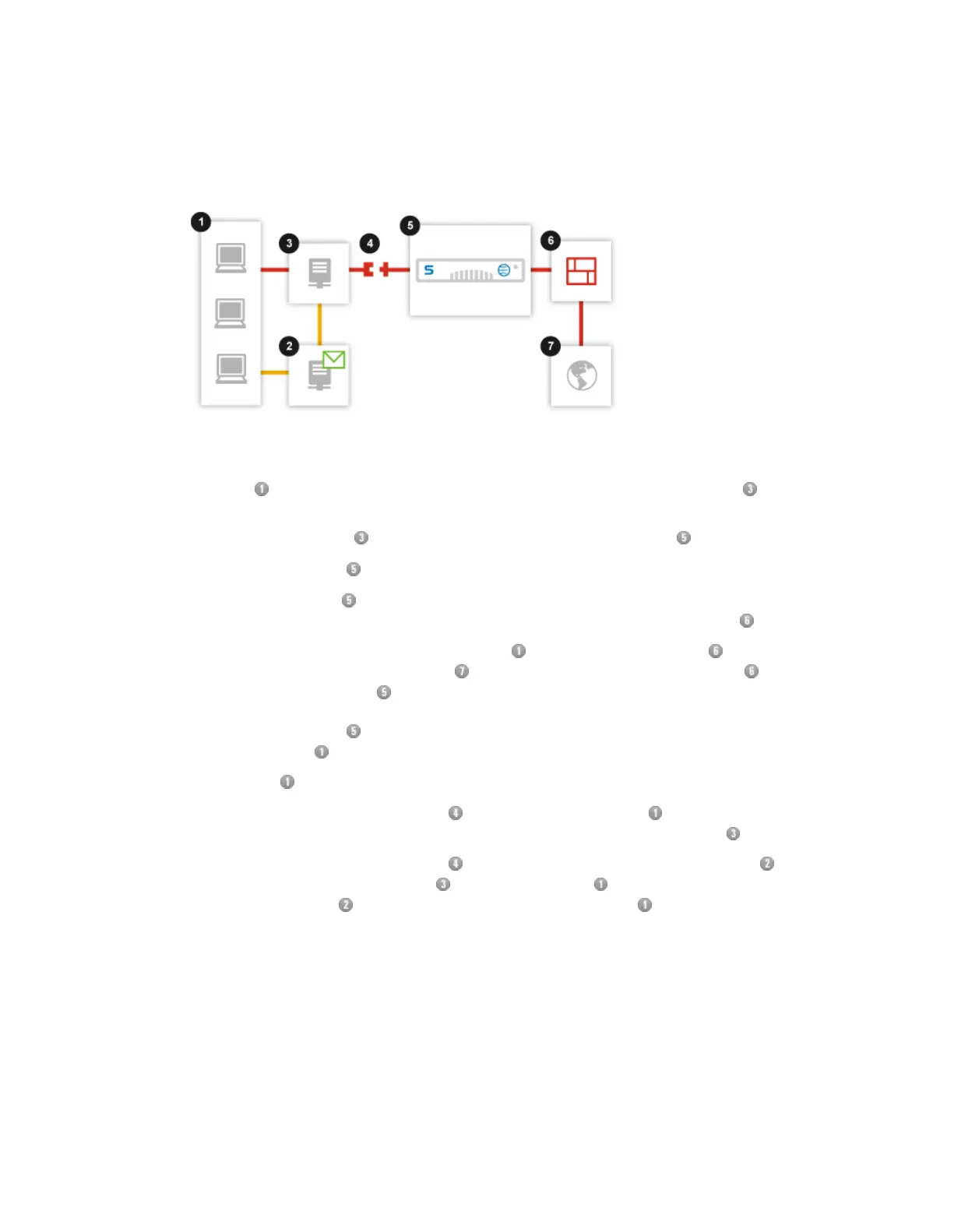
■
Users’ HTTP and HTTPS requests are passed through an ISA/TMG server that uses
NTLM or IWA Authentication.
■
The ISA/TMG server passes URL requests to the Web Appliance .
■
The Web Appliance assesses the URL.
■
The Web Appliance blocks disallowed requests, checks if allowed URL requests are currently
cached, and passes URL requests that are not cached through to the firewall .
Note: Port 80 and 443 requests from users are blocked at the firewall , which retrieves
the URL’s material from the internet ; URLs are only accepted by the firewall if they are
from the Web Appliance .
■
The Web Appliance receives new pages or files, caches them, and passes the page or file
on to the users .
■
The users receive only safe and allowed pages and files or a notification page.
Note: If the Sophos ISA/TMG plug-in is installed, clients (users) are identified individually;
otherwise, all traffic is identified as coming from one user: the ISA/TMG server .
Note: If the Sophos ISA/TMG plug-in is installed, and an Active Directory server is on the
network side of the ISA/TMG server , then clients (users) can be seen as usernames; if the
Active Directory server is not appropriately located, clients (users) appear only as IP addresses
in reports and user activity logs.
The ISA/TMG plug-in can be downloaded from the Configuration > Network > Hostname page.
The ISA/TMG plug-in is compatible with Microsoft ISA Server 2004 and 2006, and Microsoft
Forefront TMG 2010.
Configuration
Important: The Web Appliance may not catch malware stored in the ISA/TMG server’s cache.
To avoid this risk, be sure to clear the ISA/TMG cache prior to enabling this network deployment.
28 | Getting Started | Sophos Web Appliance
 Loading...
Loading...