Threat Protection System Hardware Specification and Installation Guide 1
About this guide
Welcome to the installation and specification guidelines for your Threat Protection System (TPS) device.
This section covers the following topics:
• Target audience on page 1
• Related documentation on page 1
• Conventions on page 1
• Product support on page 2
Target audience
The intended audience includes technicians and maintenance personnel responsible for installing,
configuring, and maintaining TippingPoint security systems and associated devices. Users should be familiar
with the following concepts or environments:
• Basic networking
• Network security
• Routing
Related documentation
A complete set of documentation for your product is available on the TippingPoint Threat Management
Center (TMC) at https://tmc.tippingpoint.com. The documentation generally includes installation and user
guides, command line interface (CLI) references, safety and compliance information, and release notes.
Conventions
This information uses the following conventions.
Typefaces
The following typographic conventions for structuring information are used.
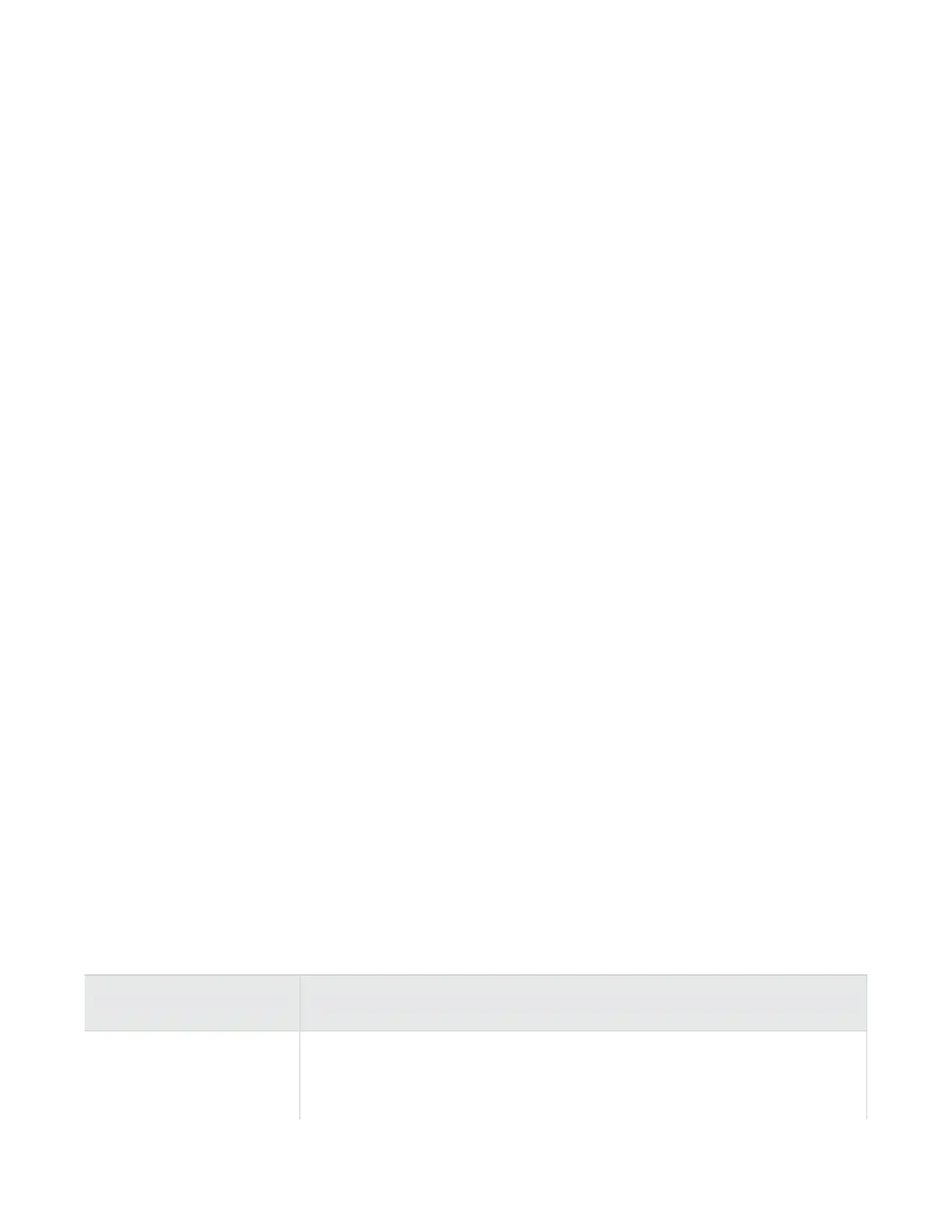
Convention Element
Bold font
• Key names
• Text typed into a GUI element, such as into a box

 Loading...
Loading...