User authentication Terminal Access Controller Access-Control System Plus (TACACS+)
IX10 User Guide
710
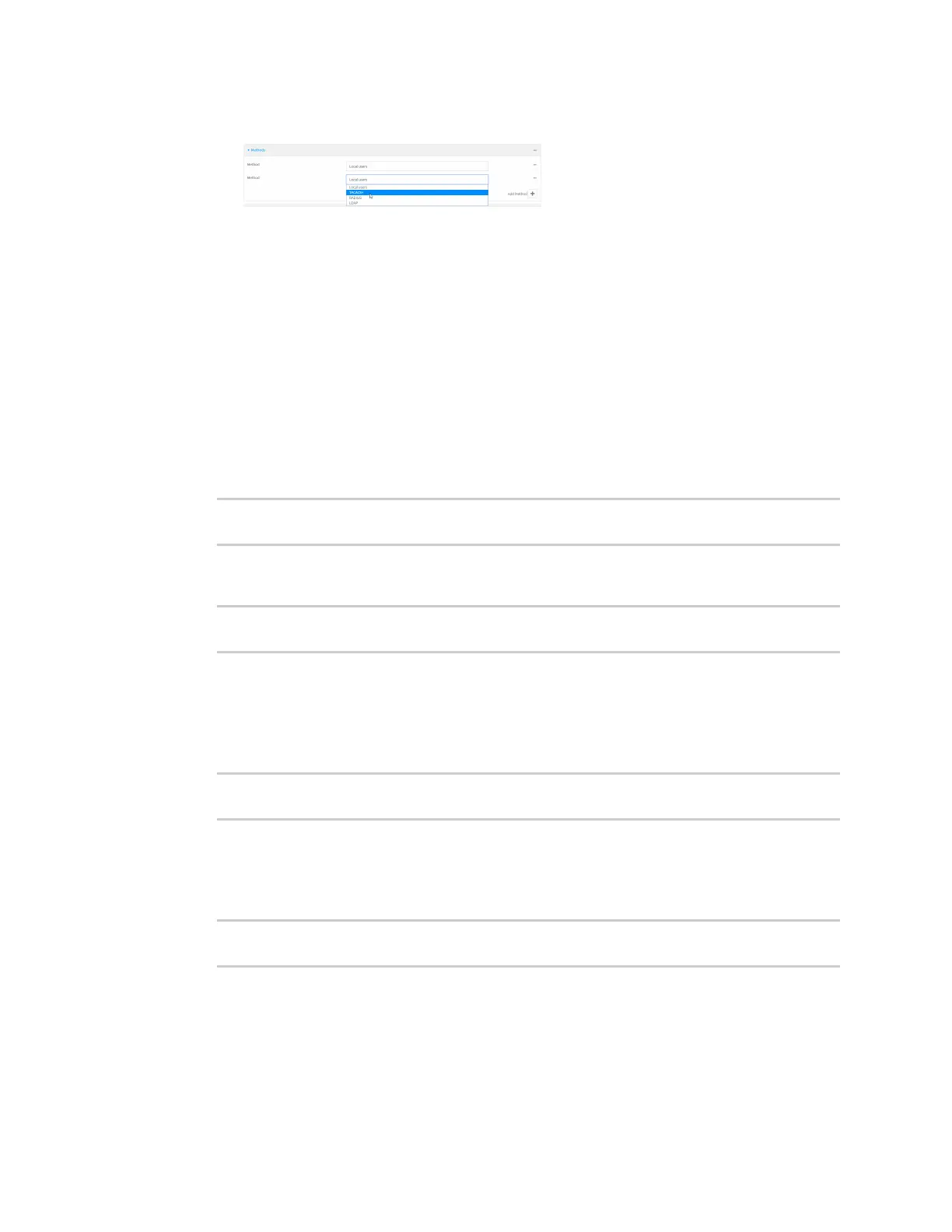
c. Select TACACS+ for the new method from the Method drop-down.
Authentication methods are attempted in the order they are listed until an authentication
response, either pass or fail, is received. If Authoritative is enabled (see above), non-
authoritative methods are not attempted. See Rearrange the position of authentication
methods for information about rearranging the position of the methods in the list.
11. Click Apply to save the configuration and apply the change.
Command line
1. Select the device in Remote Manager and click Actions > Open Console, or log into the IX10
local command line as a user with full Admin access rights.
Depending on your device configuration, you may be presented with an Access selection
menu. Type admin to access the Admin CLI.
2. At the command line, type config to enter configuration mode:
> config
(config)>
3. (Optional) Prevent other authentication methods from being used if TACACS+ authentication
fails. Other authentication methods will only be used if the TACACS+ server is unavailable.
(config)> auth tacacs+ authoritative true
(config)>
4. (Optional) Configure the group_attribute. This is the name of the attribute used in the TACACS+
server's configuration to identify the IX10 authentication group or groups that the user is a
member of. For example, in TACACS+ user configuration, the group attribute in the sample
tac_plus.conf file is groupname, which is also the default setting for the group_attribute in the
IX10 configuration.
(config)> auth tacacs+ group_attribute attribute-name
(config)>
5. (Optional) Configure the type of service. This is the value of the service attribute in the the
TACACS+ server's configuration. For example, in TACACS+ user configuration, the value of the
service attribute in the sample tac_plus.conf file is system, which is also the default setting in
the IX10 configuration.
(config)> auth tacacs+ service service-name
(config)>
6. (Optional) Enable command authorization, which instructs the device to communicate with the
TACACS+ server to determine if the user is authorized to execute a specific command. Only the
first configured TACACS+ server will be used for command authorization.
 Loading...
Loading...