5-3
Configuring Port-Based Access Control (802.1x)
Overview
Temporary on-demand change of a port’s VLAN membership status
to support a current client’s session. (This does not include ports that
are members of a trunk.)
Session accounting with a RADIUS server, including the accounting
update interval.
Use Show commands to display session counters.
With port-security enabled for port-access control, limit a port to one
802.1x client session at a given time.
Authenticating Users. Port-Based Access Control (802.1x) provides
switch-level security that allows LAN access only to users who enter the
authorized RADIUS username and password on 802.1x-capable clients (sup-
plicants). This simplifies security management by allowing you to control
access from a master database in a single server (although you can use up to
three RADIUS servers to provide backups in case access to the primary server
fails). It also means a user can enter the same username and password pair
for authentication, regardless of which switch is the access point into the LAN.
Note that you can also configure 802.1x for authentication through the
switch’s local username and password instead of a RADIUS server, but doing
so increases the administrative burden, decentralizes username/password
administration, and reduces security by limiting the available authentication
methods to only one: MD5.
Authenticating One Switch to Another. 802.1x authentication also
enables the switch to operate as a supplicant when connected to a port on
another switch running 802.1x authentication.
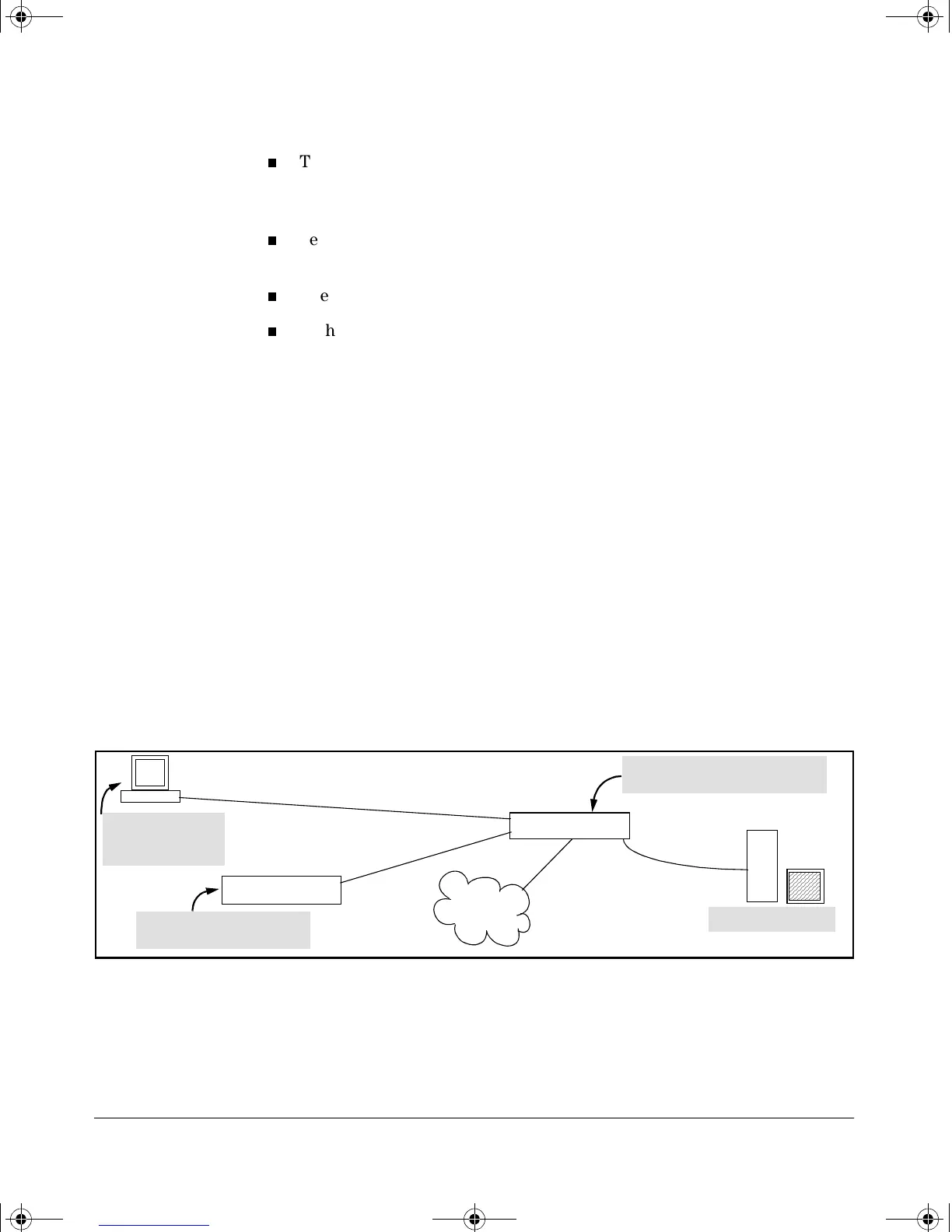
Figure 5-1. Example of an 802.1x Application
Accounting . The Swtich 2650 and 6108 also provide RADIUS Network
accounting for 802.1x access. Refer to “Configuring RADIUS Accounting” on
page 3-16.
RADIUS Server
LAN Core
802.1x-Aware
Client
(Supplicant)
Switch Running 802.1x and
Connected as a Supplicant
Switch Running 802.1x and
Operating as an Authenticator
!FishSecurity.book Page 3 Thursday, October 10, 2002 9:19 PM

 Loading...
Loading...











