FAULT/SAFETY
In the navigation bar, select “Fault/Safety” to set options for Anti Attack, Channel Detection, ACL
and 802.1x.
ANTI ATTACK
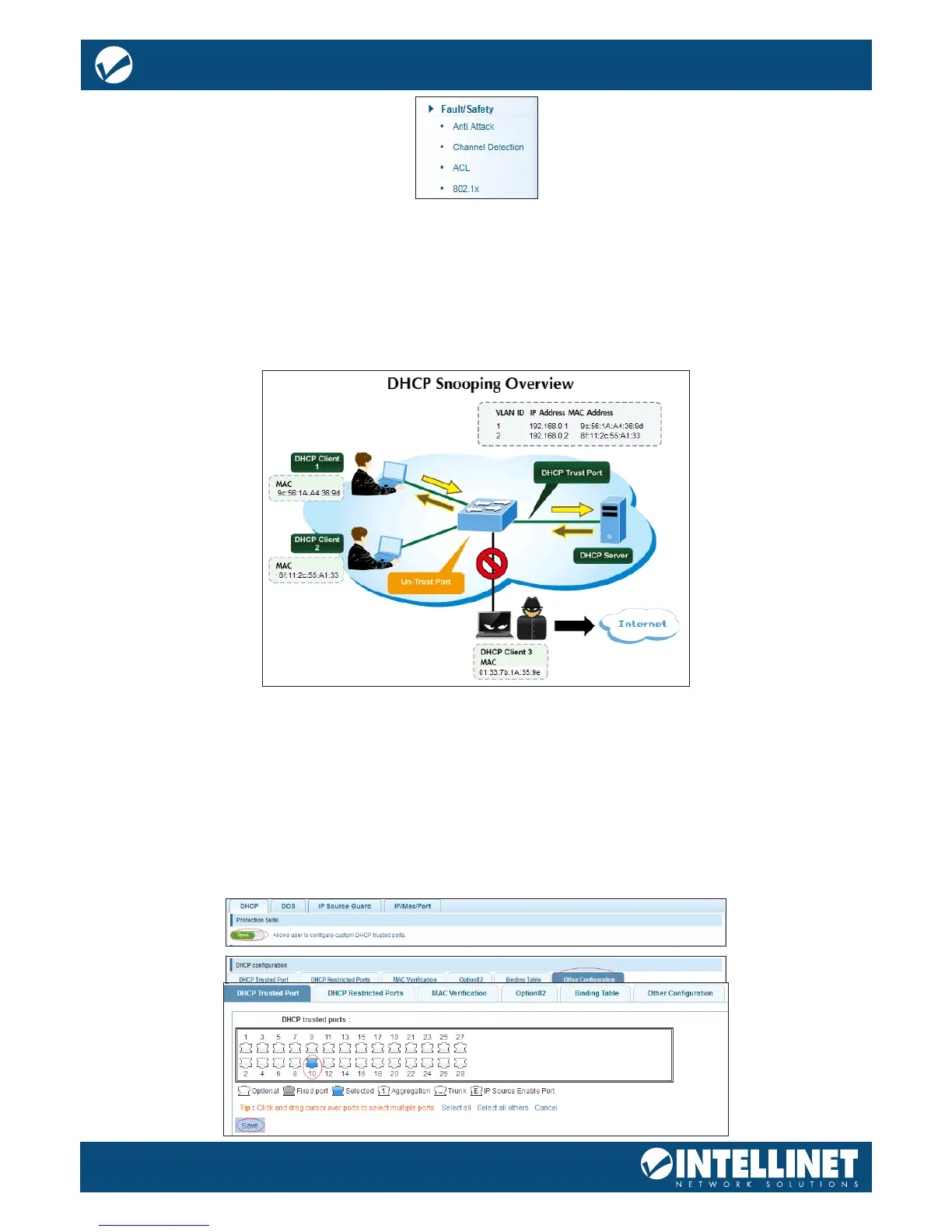
DHCP SNOOPING
DHCP snooping is a security technology built into the operating system of a capable network switch that
drops DHCP trac determined to be unacceptable. The fundamental use for DHCP snooping is to prevent
unauthorized (rogue) DHCP servers oering IP addresses to DHCP clients.
COMMAND USAGE
Network trac may be disrupted when malicious DHCP messages are received from an outside source.
DHCP snooping is used to lter DHCP messages received on a non-secure interface from outside the
network or rewall. When DHCP snooping is enabled globally and enabled on a VLAN interface, DHCP
messages received on an untrusted interface from a device not listed in the DHCP snooping table will
be dropped.
Table entries are only learned for trusted interfaces. An entry is added or removed dynamically to the DHCP
snooping table when a client receives or releases an IP address from a DHCP server. Each entry includes a
MAC address, IP address, lease time, VLAN identier and port identier. When DHCP snooping is enabled,
DHCP messages entering an untrusted interface are ltered based upon dynamic entries learned via DHCP
snooping.
 Loading...
Loading...