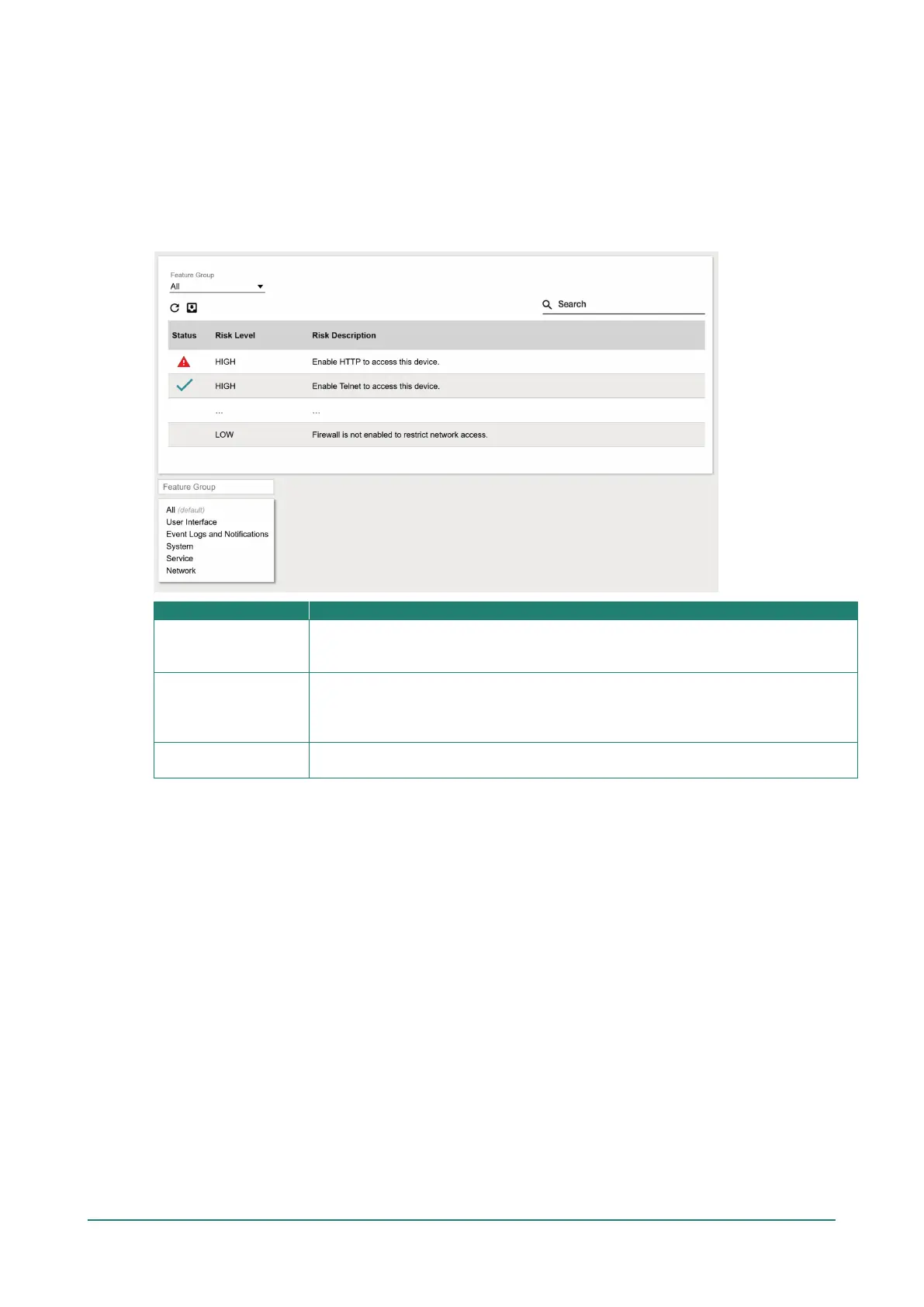
Security Status
The Security Status screen consolidates the security status of all active interfaces of the device. This table
serves as a review tool to ensure that the device’s configuration meets the desired IEC-62443 Security Level
(SL) profile. If any of the configuration risks do not meet your organization's security policy, check the
description, and navigate to the corresponding configuration page to address the issue. If the identified risk
cannot be directly mitigated through the AWK Series' configuration, such as an active unsecure protocol to
support legacy devices, consider consulting a qualified security expert to implement additional measures to
mitigate the risk.
Status
The representative icons indicate if there are any risks that require mitigating action,
and the corresponding severity of the risk. Risks that have been addressed will be
marked with a checkmark.
Risk Level
The device categorizes risks into three tiers:
Low: Risks vulnerable to exploitation per circumstances defined in SL3 and above.
Medium: Risks vulnerable to exploitation per circumstances defined in SL2.
High: Risks vulnerable to exploitation per circumstances defined in SL1.
Risk Description
Additional details describing the risk to provide administrators with context for taking
the appropriate hardening action.
Trusted Access
In order to prevent DoS attacks, the Trusted Access feature allows authorized users to designate the IP or
MAC addresses that are allowed to access this device. When configured and enabled, the Trusted Access list
will only allow the specified IP or MAC addresses access to the corresponding interfaces, databases, or
services.
Trusted Access applies to the following interfaces, databases, and services:
• User interfaces: HTTP/HTTPS, SSH/Telnet, SNMP, New Moxa Command.
• Event logs and notifications: Syslog, Email notifications, SNMP Trap/Inform.
• Services: DHCP Server, Wi-Fi Sniffer, Mirroring with Remote Type.
 Loading...
Loading...