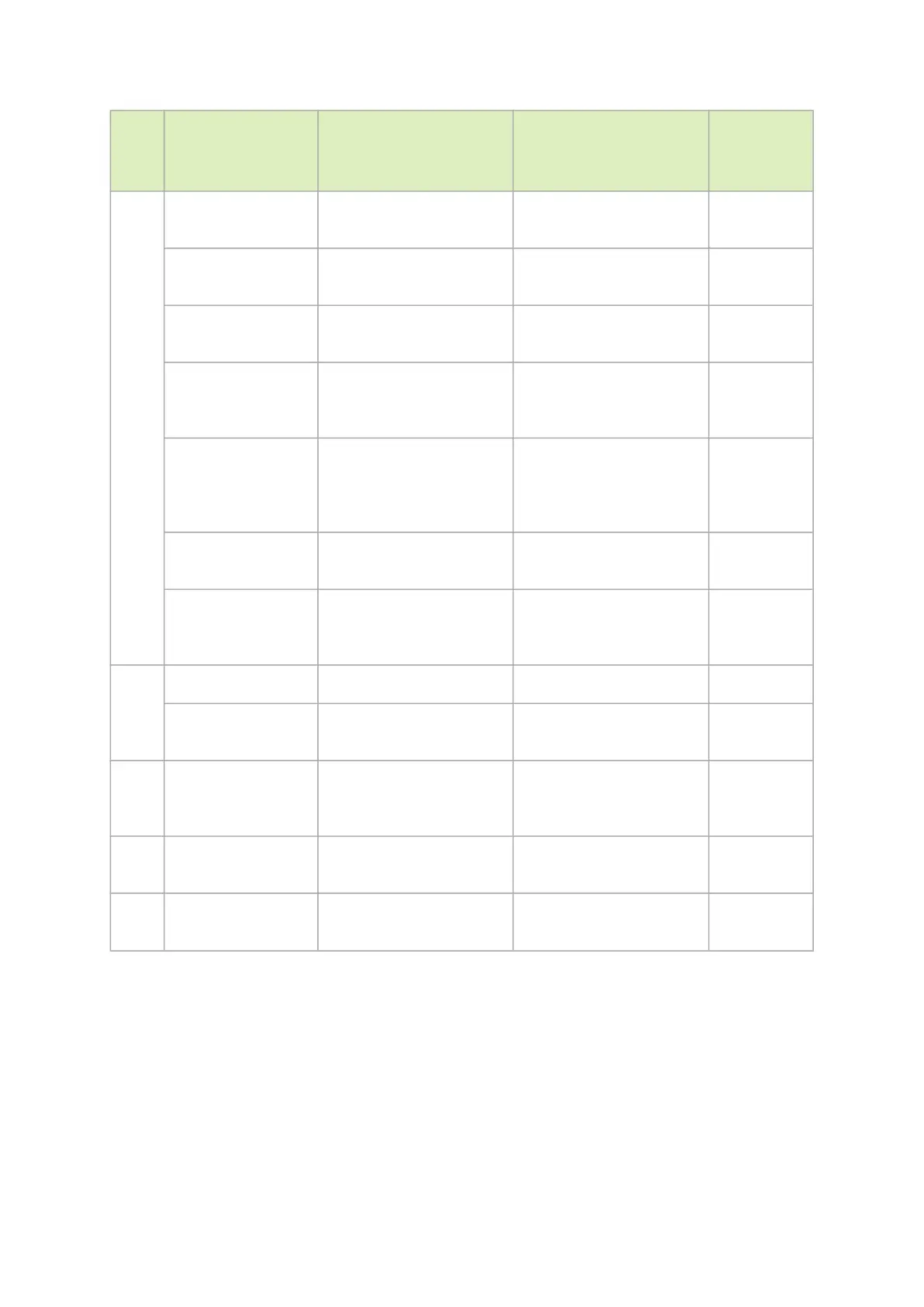
•
Tool Flow Secure FW With CS Token Blocked
Command
s
Set GUIDs Working with controlled fw
update
Working with controlled fw
update
Verify Working partially (BOOT
image)
Working partially (BOOT
image)
Set DV INFO: SET
MFG, SET VSD, VPD
Not supported in Secure
FW
Not supported in Secure
FW
MFBA
ROM OPS: BROM,
DROM
Not supported, BOOT
image modification is not
supported (MFBA)
Not supported, BOOT
image modification is not
supported (MFBA)
MFBA
"-ocr" override
cache replacement
(Direct flash GW
access)
Not supported in Secure
FW
Not supported in Secure
FW
Flash GW is
blocked
HW SET (Set flash
parameters)
Flash GW is blocked Flash GW is blocked Flash GW is
blocked
"--
no_fw_ctrl" (Legacy
Flow)
Not supported in Secure
FW
Not supported in Secure
FW
MFBA
mstm
cra
Read working working working
Write Read Only CR- Space working Read Only
CR- Space
mstre
gdum
p
Read working working working
mstco
nfig
working working working working
mstfw
reset
working working working working
The following sections describe how Secure FW updates are performed.
Signing Binary Image Files
For firmware Secure purposes, you may sign the image file using the sign command. If you donot
provide the sign command with a private key and UUID, the command will only computeSHA256 digest
and add it to the image signature section. The sign command supports RSA keyswith lengths of 2048
and 4096 bits.
If you provide a private key with the length of 2048 bits, the command will compute
SHA256 digest and encrypt it with the private key and add the result with the provided
UUID to the appropriate image signature section.
 Loading...
Loading...