Tsunami QB-8100 Series (100 Mbps/5 Mbps Models) Installation and Management Guide 68
4.5.1.2 Modifying a Security Profile
To edit the parameters of the existing security profiles
1. Click ADVANCED CONFIGURATION > Security > Wireless Security.
2. Click Edit. The Wireless Security Edit Row page appears.
3. Edit the parameters and click OK.
4. To apply the configured properties to the device, click COMMIT.
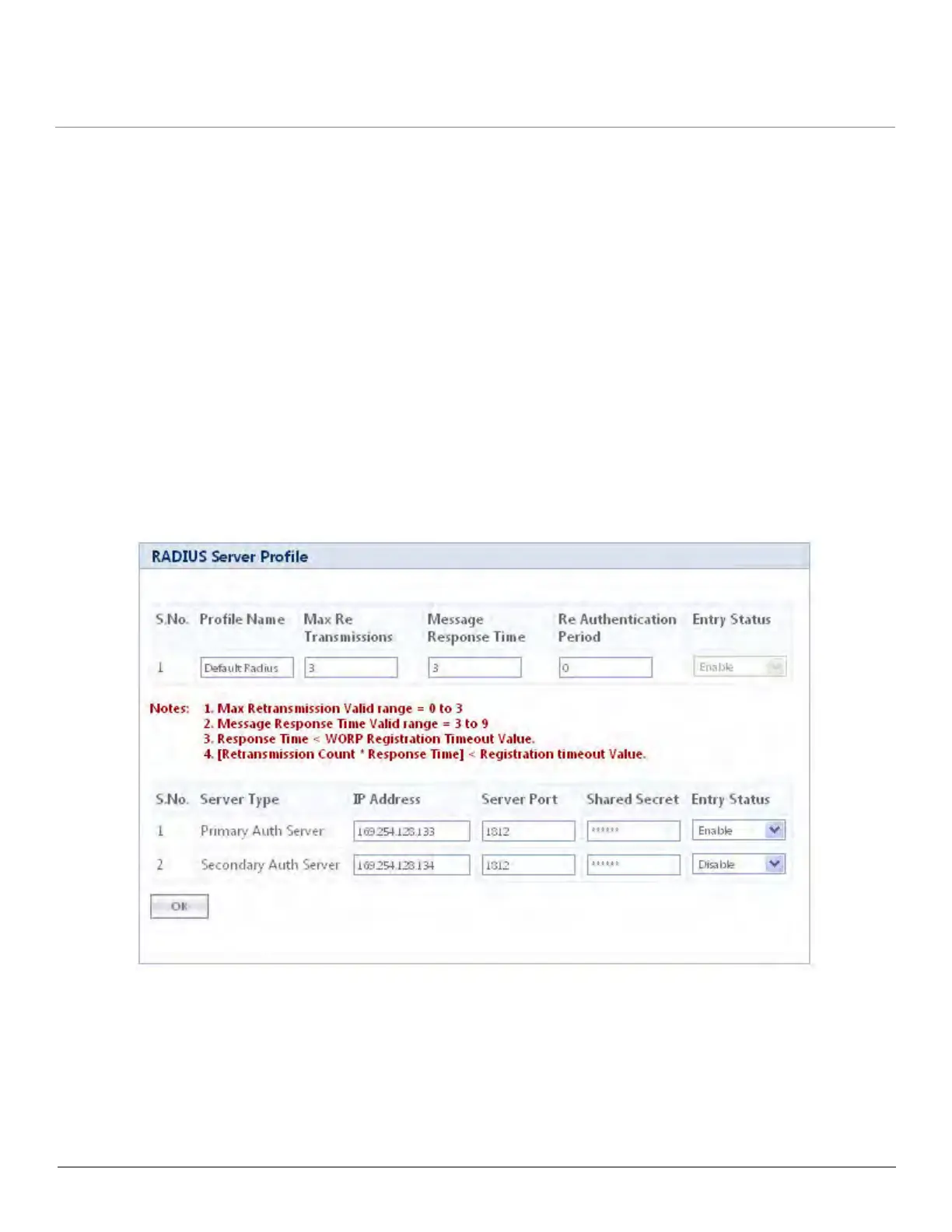
4.5.2 Configuring the Radius Server Profile (End Point A Only)
In large networks, you can maintain a list of MAC addresses on a centralized location using a RADIUS authentication server
that grants or denies access.
A RADIUS server profile consists of a Primary and a Secondary RADIUS server that can be assigned to act as MAC
Authentication servers. Configuration of Secondary Authentication Server is optional. The Radius server is referred to only
when it is enabled on the WORP Configuration page.
To configure the Radius Server profile
1. Click ADVANCED CONFIGURATION > Security > RADIUS. The Radius Server Profile screen is displayed as shown
below.
Figure 4-14 RADIUS Server Profile
2. Enter the appropriate parameters on the Radius Server Profile screen. See the following table that lists the parameters
and their descriptions.
3. Click OK.

 Loading...
Loading...