SFC6400A/SFC1450A Synthesized Frequency Upconverter User Interfaces
TM106 – Rev. 1.1 4-45
4.6.2.21 Context Engine ID
“contextEngineID” is the unique identifier of the Upconverter SNMP Engine that provides services for
sending and receiving messages, authenticating and encrypting messages, and controlling access
to managed objects.
1. The Context Engine ID, 80000A1F01AC1264B0, is formatted as follows:
a. The first 4 bytes are the Radyne ComStream Private Enterprise Number (2591).
b. The very first bit is set to 1, for example: 80000A1F (H).
c. The fifth byte indicates how the 6
th
and remaining bytes are formatted. A ‘1’ means
it’s an IPv4 Address.
d. The last 4 bytes are the IP Address 172.18.100.176 (AC1264B0).
4.6.2.22 View-Based Access Control
SNMPv3 defines a method of access control known as the View-based Access Control Model
(VACM). It is defined as a means to restrict access to particular subsets of variables based on the
identity of the manager and the security level used in the request.
A view is a group of MIB variables on the agent. The agent defines a view for each user based on
the user identity (securityName) and security level. Following are the major views:
System view: Access to system description
MIB-II view: Access to the standard MIB-II information
Device view: Access to the device private information
World view: Access to every managed object in the MIB
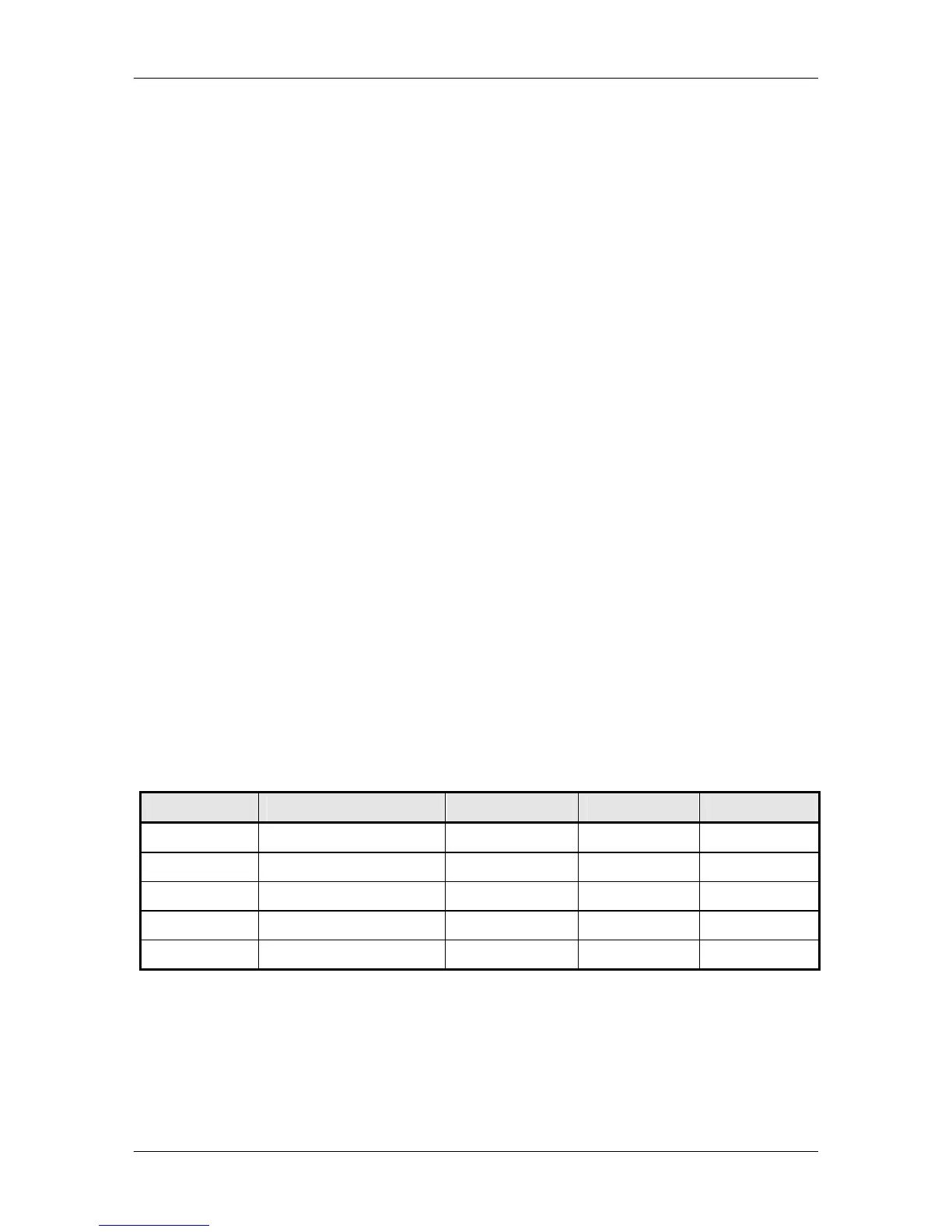
Following are the available access groups:
Group Context/Community Security Level Read Access Write Access
NULL mib2 NoAuth/noPriv System view NONE
Viewer mib2 Auth/noPriv MIB-II view NONE
Viewer Dev Auth/Priv Device view NONE
Oper mib2 Auth/noPriv MIB-II view MIB-II view
Oper Dev Auth/Priv Device view Device view
The NULL Security Name is for backward compatibility with SNMP Version 1 and 2 management
stations (security names are not defined for earlier protocols). In this case, the contextName in
each view may refer to either a contextName or a communityName. The securityLevel would then
be noAuth/noPriv.
 Loading...
Loading...