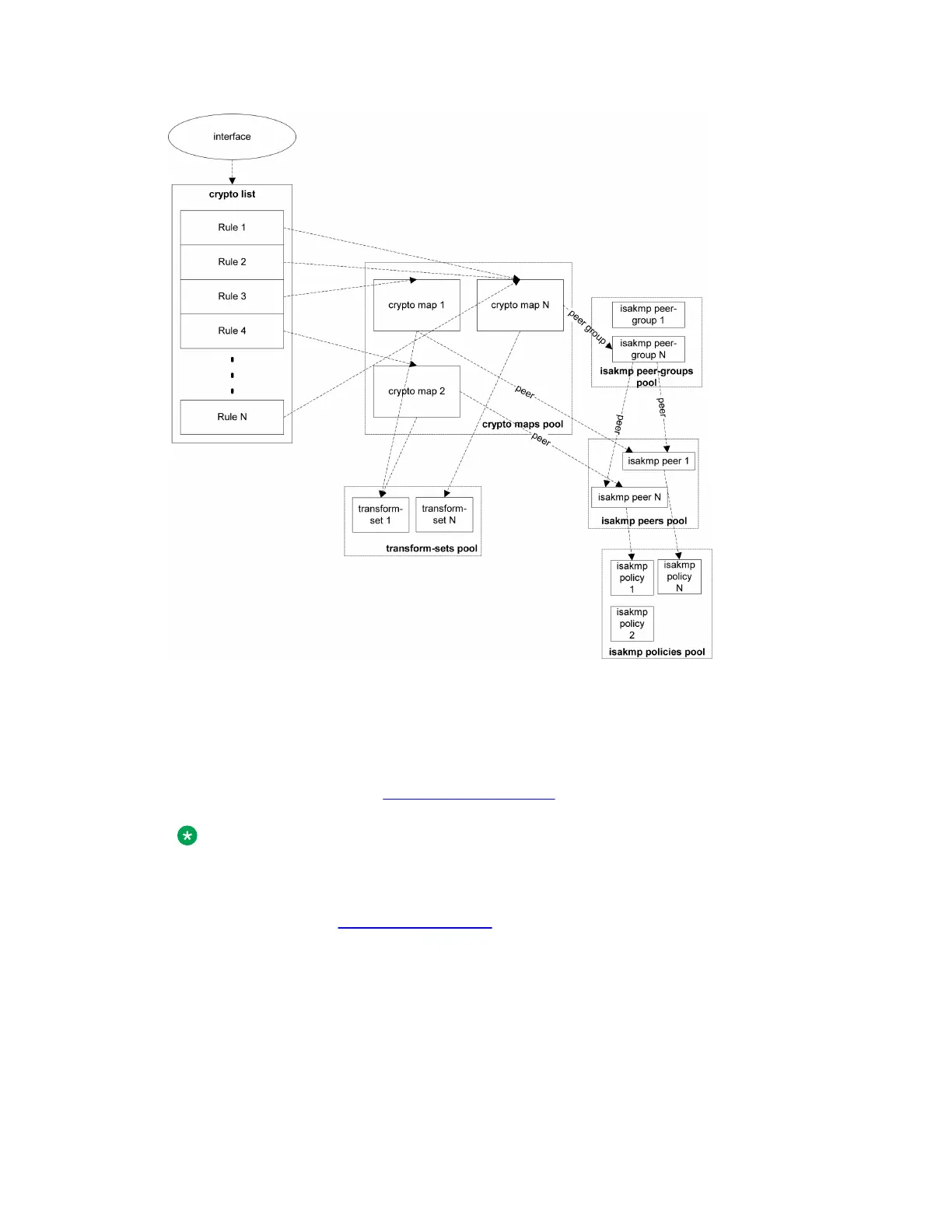
Summary of configuration commands
The commands required to configure a VPN are listed below. For a step-by-step description
of the VPN procedures, see Site-to-site IPSec VPN on page 485.
Note:
You must configure VPN in the order shown in the summary. Commands appearing in bold
are mandatory.
• ISAKMP policy –
crypto isakmp policy on page 486
- description
- authentication pre-share
- encryption
- hash
IPSec VPN
Administering Avaya G430 Branch Gateway October 2013 483
 Loading...
Loading...




