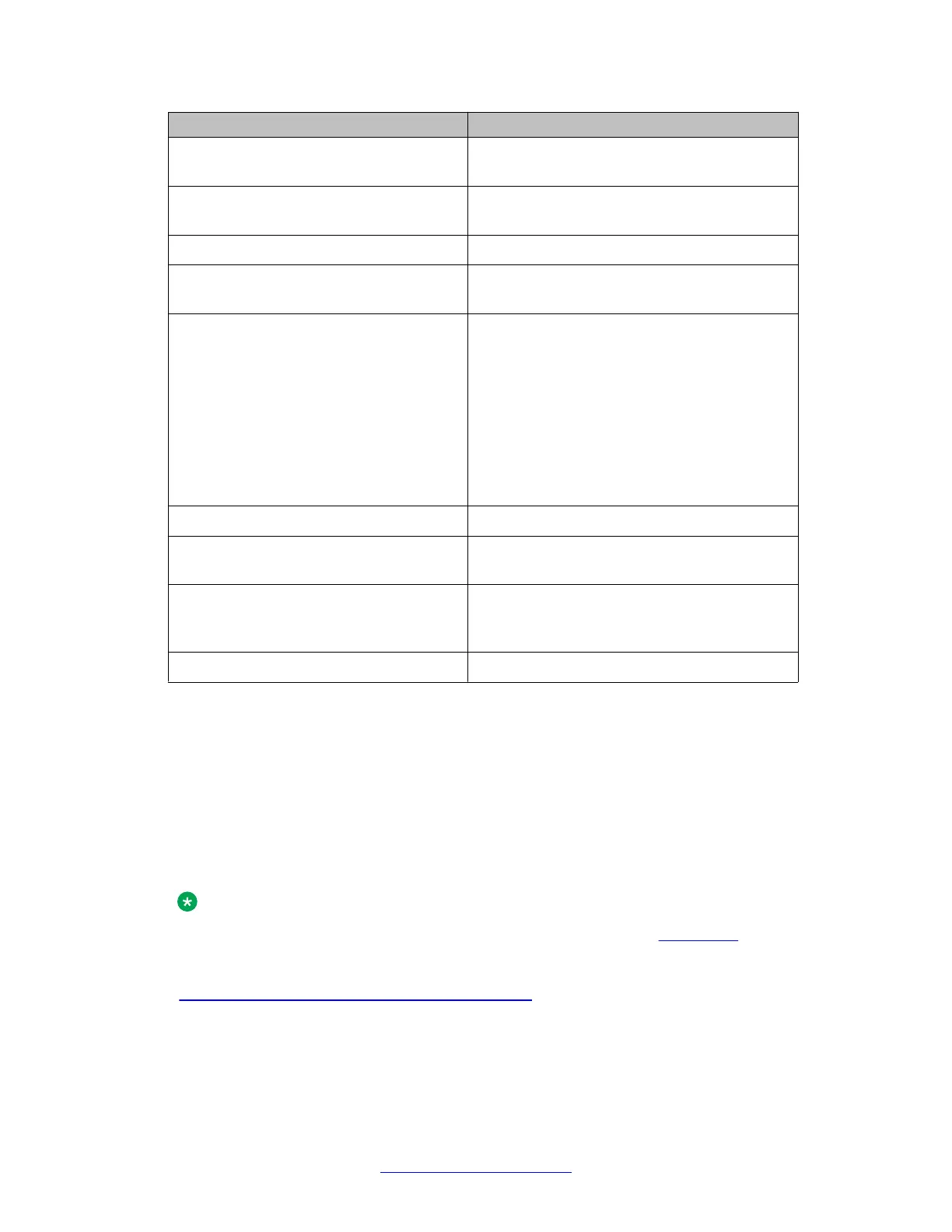
DoS Attack Description
FRAGGLE_ATTACK UDP packets with limited broadcast destination
address
SYN-FLOOD The number of unacknowledged TCP SYN-
ACK exceeds a predefined rate
UNREACHABLE_PORT_ ATTACK TCP/UDP IP packets sent to unreachable ports
MALFRAGMENTED_IP Malfragmented IP packets on TO-ME
interfaces
MALFORMED_IP Malformed IP packets.
The Branch Gateway reports malformed IP
packets when:
• The IP version in the IP header is a value
other than 4
• The IP header length is smaller than 20
• The total length is smaller than the header
length
MALFORMED_ARP ARP messages with bad opcode
SPOOFED_IP For all routable packets, the Branch Gateway
report reception of IP spoofed packets
UNKNOW_L4_IP_PROTOCOL Packets with unknown (unsupported or
administratively closed) protocol in IP packet
with TO-ME interface as a destination
UNATHENTICATED_ACCESS Failure to authenticate services
Custom DoS classifications
You can define custom DoS attack classifications using access control list (ACL) rules. ACL
rules control which packets are authorized to pass through an interface. A custom DoS class
is defined by configuring criteria for an ACL rule and tagging the ACL with a DoS classification
label.
Note:
For general information about configuring policy rules, refer to Policy lists on page 557.
Related topics:
Examples for defining a DoS class using ACLs on page 59
Accessing the Branch Gateway
58 Administering Avaya G430 Branch Gateway October 2013
Comments? infodev@avaya.com
 Loading...
Loading...




