1-10
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring Cisco Unified Presence
Configuring Cisco Unified Presence Proxy for SIP Federation
Creating Trustpoints and Generating Certificates
You need to generate the keypair for the certificate (such as cup_proxy_key) used by the ASA, and
configure a trustpoint to identify the self-signed certificate sent by the ASA to Cisco UP (such as
cup_proxy) in the TLS handshake.
What to Do Next
Install the certificate on the local entity truststore. You could also enroll the certificate with a local CA
trusted by the local entity. See the “Installing Certificates” section on page 1-10.
Installing Certificates
Export the self-signed certificate for the ASA created in the “Creating Trustpoints and Generating
Certificates” section on page 1-10 and install it as a trusted certificate on the local entity. This task is
necessary for local entity to authenticate the ASA.
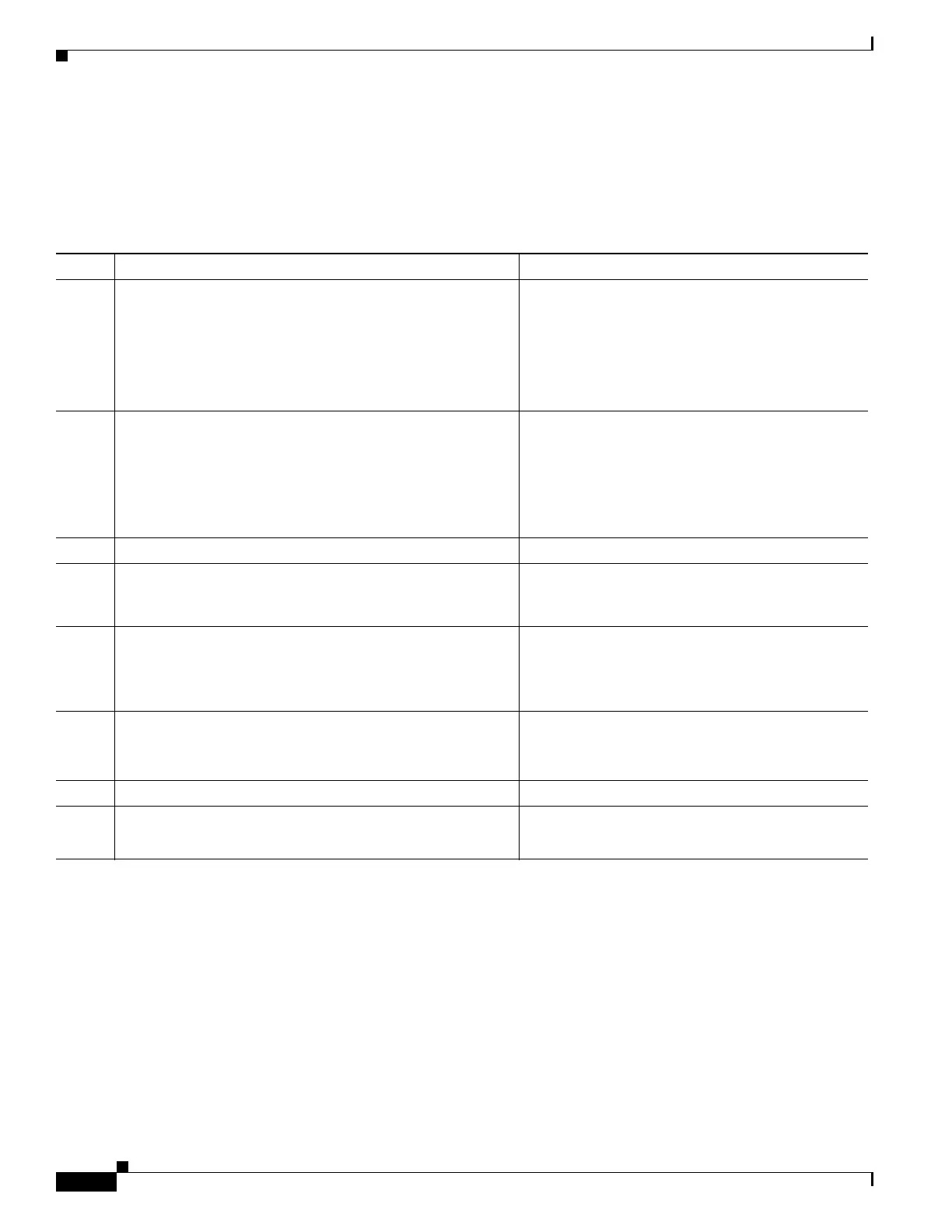
Command Purpose
Step 1
hostname(config)# crypto key generate rsa label
key-pair-label modulus size
Example:
crypto key generate rsa label ent_y_proxy_key
modulus 1024
INFO: The name for the keys will be: ent_y_proxy_key
Keypair generation process begin. Please wait...
hostname(config)#
Creates the RSA keypair that can be used for the
trustpoints.
The keypair is used by the self-signed certificate
presented to the local domain containing the Cisco
UP (proxy for the remote entity).
Step 2
hostname(config)# crypto ca trustpoint
trustpoint_name
Example:
hostname(config)# crypto ca trustpoint ent_y_proxy
Enters the trustpoint configuration mode for the
specified trustpoint so that you can create the
trustpoint for the remote entity.
A trustpoint represents a CA identity and possibly a
device identity, based on a certificate issued by the
CA.
Step 3
hostname(config-ca-trustpoint)# enrollment self
Generates a self-signed certificate.
Step 4
hostname(config-ca-trustpoint)# fqdn none
Specifies not to include a fully qualified domain
name (FQDN) in the Subject Alternative Name
extension of the certificate during enrollment.
Step 5
hostname(config-ca-trustpoint)# subject-name
X.500_name
Example:
hostname(config-ca-trustpoint)# subject-name
cn=Ent-Y-Proxy
Includes the indicated subject DN in the certificate
during enrollment
Step 6
hostname(config-ca-trustpoint)# keypair keyname
Example:
hostname(config-ca-trustpoint)# keypair
ent_y_proxy_key
Specifies the key pair whose public key is to be
certified.
Step 7
hostname(config-ca-trustpoint)# exit
Exits from the CA Trustpoint configuration mode.
Step 8
hostname(config)# crypto ca enroll trustpoint
Example:
hostname(config)# crypto ca enroll ent_y_proxy
Starts the enrollment process with the CA and
specifies the name of the trustpoint to enroll with.

 Loading...
Loading...



