Firewall
BAT54-Rail/F..
Release
7.54
06/08
8.4
Intrusion Detection
303
U Portscan Detection
The Intrusion Detection system tries to recognize Portscans, to report and to
react suitably on the attack. This happens similarly to the recognition of a
’SYN Flooding’ attack (see ’SYN Flooding’ → page 304): The "half-open"
connections are counted also here, whereby a TCP RESET, which is sent by
the scanned computer, leaves a "half-open" connection open again.
If a certain number of half-open connections between the scanned and the
scanning computer exist, then this is reported as a port scan.
Likewise, the receipt of empty UDP packets is interpreted as an attempted
port scan.
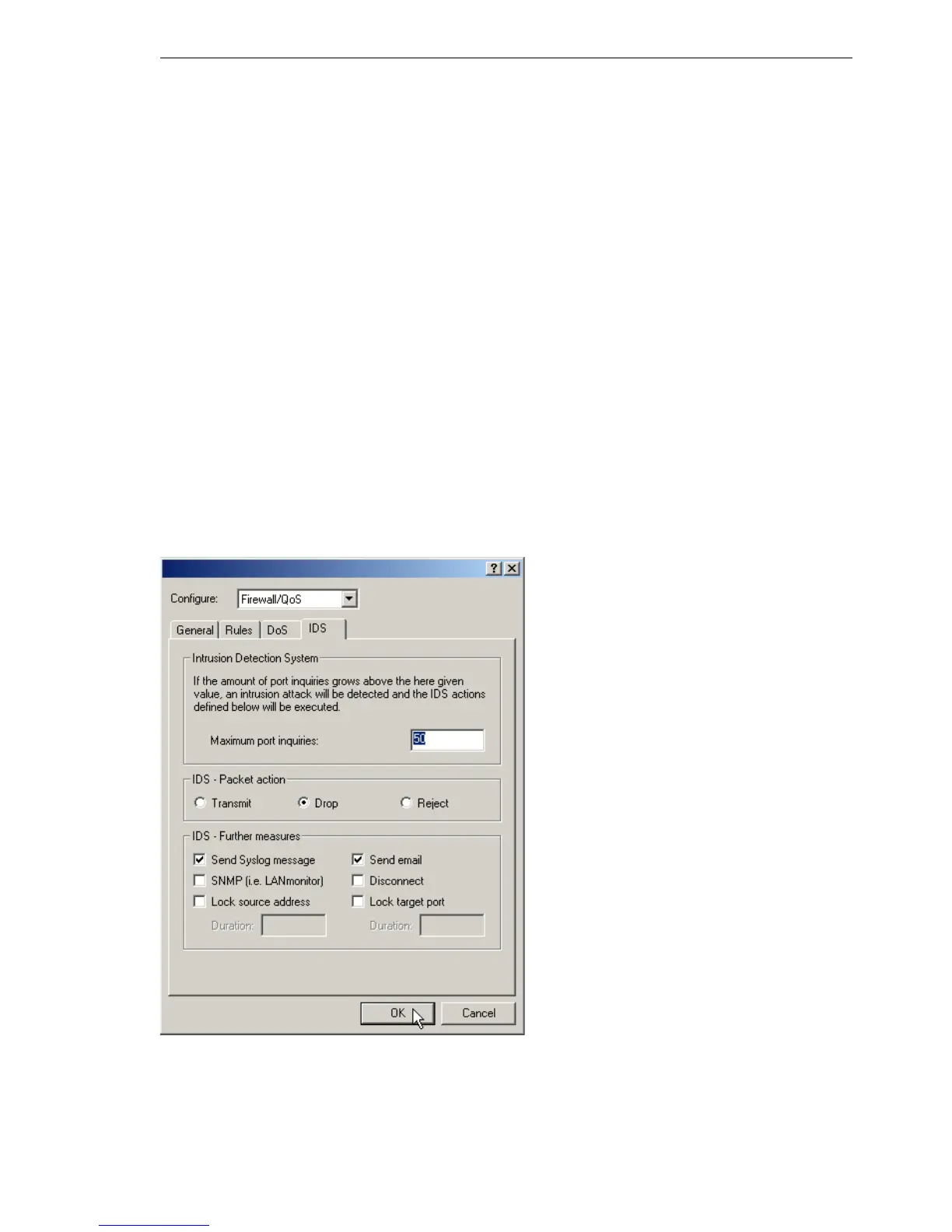
8.4.2 Configuration of the IDS
LANconfig
Parameters of the Intrusion Detection System are set in LANconfig in the
configuration tool 'Firewall/QoS' on index card 'IDS':
Apart from the maximum number of port inquiries, fragment action and the
possible registration mechanisms, also these reactions are possible:
D The connection will be cut off.

 Loading...
Loading...