• An access control list (ACL) is configured on the Internet interface to allow only
the VPN / ICMP traffic. See step 2 for configuration settings.
Note:
For information about using access control lists, see
Policy lists on page 557.
2. Configure Branch Office 2 as follows:
• The default gateway is the Internet interface
• VPN policy is configured on the Internet interface egress as follows:
- Traffic from the local subnets to the First Spoke subnets -> encrypt, using
tunnel mode IPSec, with the remote peer being the First Spoke
- Traffic from the local subnets to any IP address -> encrypt, using tunnel
mode IPSec, with the remote peer being the Main Office (VPN hub)
• An ACL is configured on the Internet interface to allow only the VPN / ICMP
traffic. See
Mesh VPN topology – Branch Office 2 on page 516 for
configuration settings.
Note:
For information about using access control lists, see
Policy lists on page 557.
3. Configure the VPN Hub (Main Office) as follows:
• Static routing: Branch subnets -> Internet interface
• The VPN policy portion for the branch is configured as a mirror image of the
branch, as follows:
- Traffic from any IP address to branch local subnets -> encrypt, using
tunnel mode IPSec
- The remote peer is the VPN Spoke (Branch Internet address)
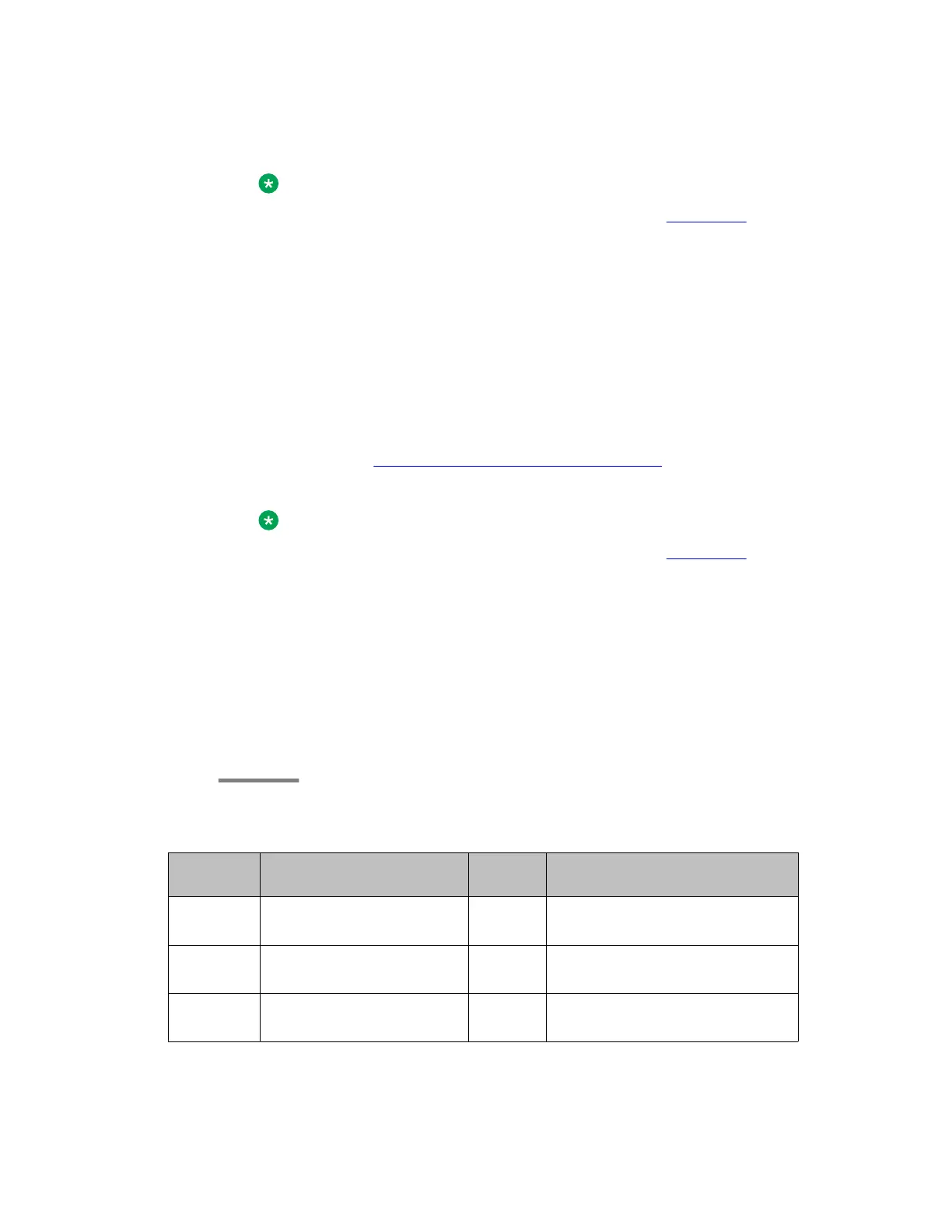
Mesh VPN topology – Branch Office 1
Traffic
direction
ACL parameter ACL
value
Description
Ingress IKE from Main Office IP to
Branch IP
Permit -
Ingress ESP from Main Office IP to
Branch IP
Permit -
Ingress IKE from Second Branch IP
to Branch IP
Permit -
IPSec VPN
Administering Avaya G430 Branch Gateway October 2013 515
 Loading...
Loading...




