Firewall
260
8.3
The BAT Firewall
BAT54-Rail/F..
Release
7.54
06/08
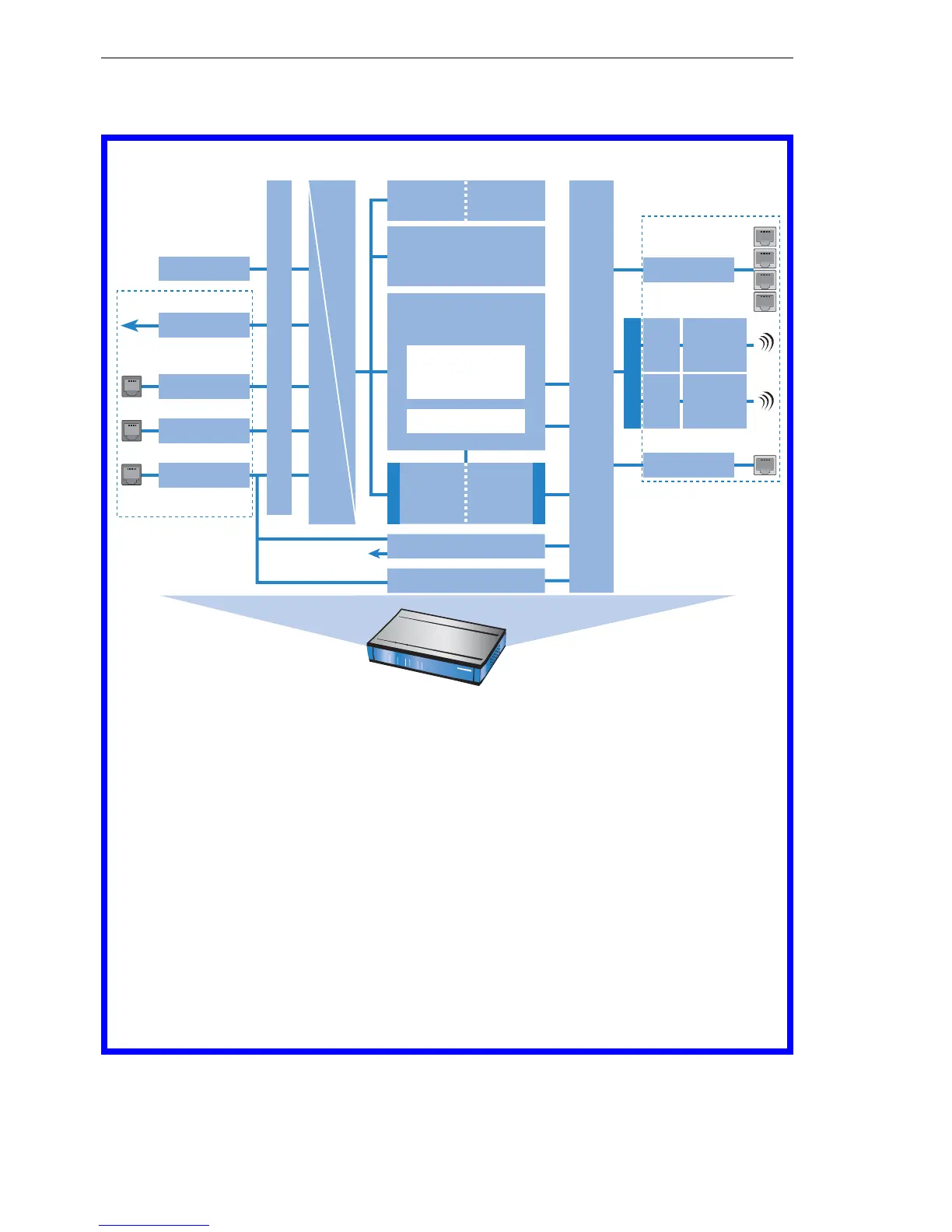
The BAT Firewall uses several lists for checking data packets, which are au-
tomatically generated from Firewall rules, resulting Firewall actions or by ac-
tive data connections:
U The Firewall only checks routed data packets!
The Firewall only checks data packets routed by the IP router of the BAT.
In general, these are the data packets, which are exchanged between
one of the WAN interfaces and the internal networks (LAN, WLAN,
DMZ).
For example, the communication between LAN and WLAN is normally
not carried out by the router, as long as the LAN bridge allows a direct
exchange. Thus the Firewall rules do not apply here. The same applies
to the so-called “internal services” of the BAT like Telnet, TFTP, SNMP
and the web server for the configuration with WEBconfig. The data pack-
ets of these services do not run through the router, and therefore aren’t
influenced by the Firewall.
Note: Due to the positioning behind the masquerading module (seen
from the WAN), the Firewall operates with the “real” internal IP ad-
dresses of the LAN stations, and not with the outside known Internet
address of the BAT.
Firewall / IDS / DoS /
QoS
IP router
LAN bridge with “isolated mode”
Virtual LANs (VLAN)
N:N mapping
ISDN
ADSL
DSL
LAN / Switch
WLAN-1-
1
to
DMZ
DSLoL
Configuration &
management:
WEBconfig, Telnet,
TFTP
VPN / PPTP
DHCP client / PPP
IP module: NetBIOS, DNS,
DHCP server, RADIUS,
RIP, NTP, SNMP, SYS-
LOG, SMTP
IPX router
LAN interfaces
WAN interfaces
IP masquerading
VPN services
LANCAPI
connection via LAN/
WLAN-2-
1
to
MAC/protocol filter
Filter
Filter
IPX over PPTP/
VPN
Encryption:
802.11i/WPA/
IP-Redirect
BAT
user man-
agement
RADIUS
client / server

 Loading...
Loading...