Firewall
BAT54-Rail/F..
Release
7.54
06/08
8.3
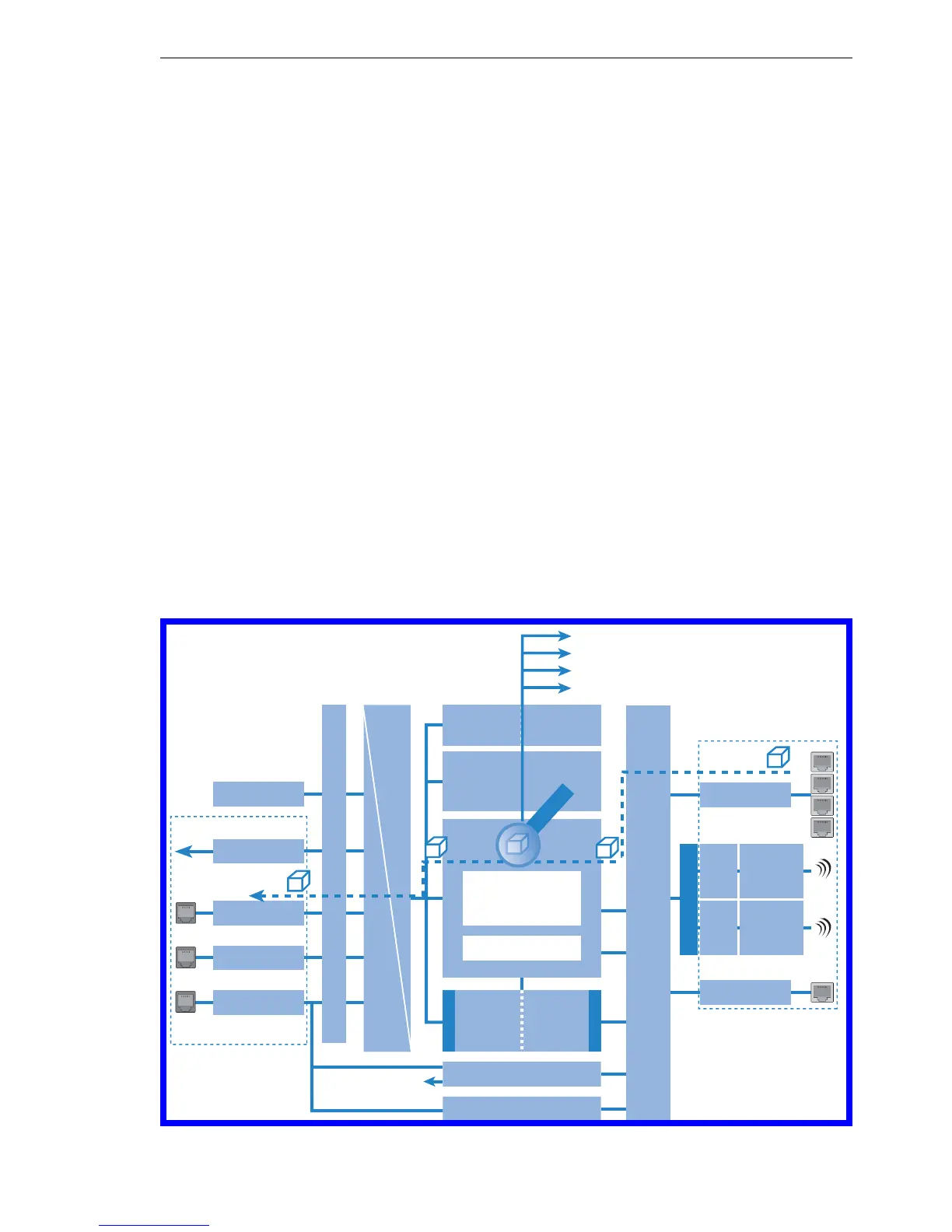
The BAT Firewall
261
D Host block list
D Port block list
D Connection list
D Filter list
When a data packet should be routed via the IP router, the Firewall uses the
lists as follows:
V The first check is, whether the packet was coming from a workstation be-
longing to the host block list. If the sender is blocked, the packet will be
discarded.
V If the sender is not blocked in this list, the port block list will be checked,
if the used port/protocol combination on the destination PC is closed. In
this case the packet will be discarded.
V If sender and destination are not blocked in the first two lists, then it will
be checked whether a connection entry exists for this packet in the con-
nection list. If such an entry exists, then the packet will be handled as
noted in this list.
V If no entry has been found for the packet, then the filter list will be
searched, whether a suitable entry exists and the action indicated in this
list will be carried out. If the action intends to accept the packet, then an
entry is made in the connection list, as well as for any further actions.
Host blocked?
Port blocked?
Active connection?
IP router
LAN bridge with “isolated mode”
Virtual LANs (VLAN)
N:N mapping
ISDN
ADSL
DSL
LAN / Switch
WLAN-1-1
to
WLAN-1-8
DMZ
DSLoL
Configuration &
management:
WEBconfig, Telnet,
TFTP
VPN / PPTP
DHCP client / PPP
IP module: NetBIOS, DNS,
DHCP server, RADIUS,
RIP, NTP, SNMP, SYS-
LOG, SMTP
IPX router
LAN interfaces
WAN interfaces
IP masquerading
VPN services
LANCAPI
connection via LAN/
WLAN-2-
1
to
WLAN-2-
MAC/protocol filter
Filter
Filter
IPX over PPTP/
VPN
Encryption:
802.11i/WPA/
IP-Redirect
BAT
user man-
agement
RADIUS
client / server

 Loading...
Loading...