1-37
AAA for Telnet Users by Separate Servers
Network requirements
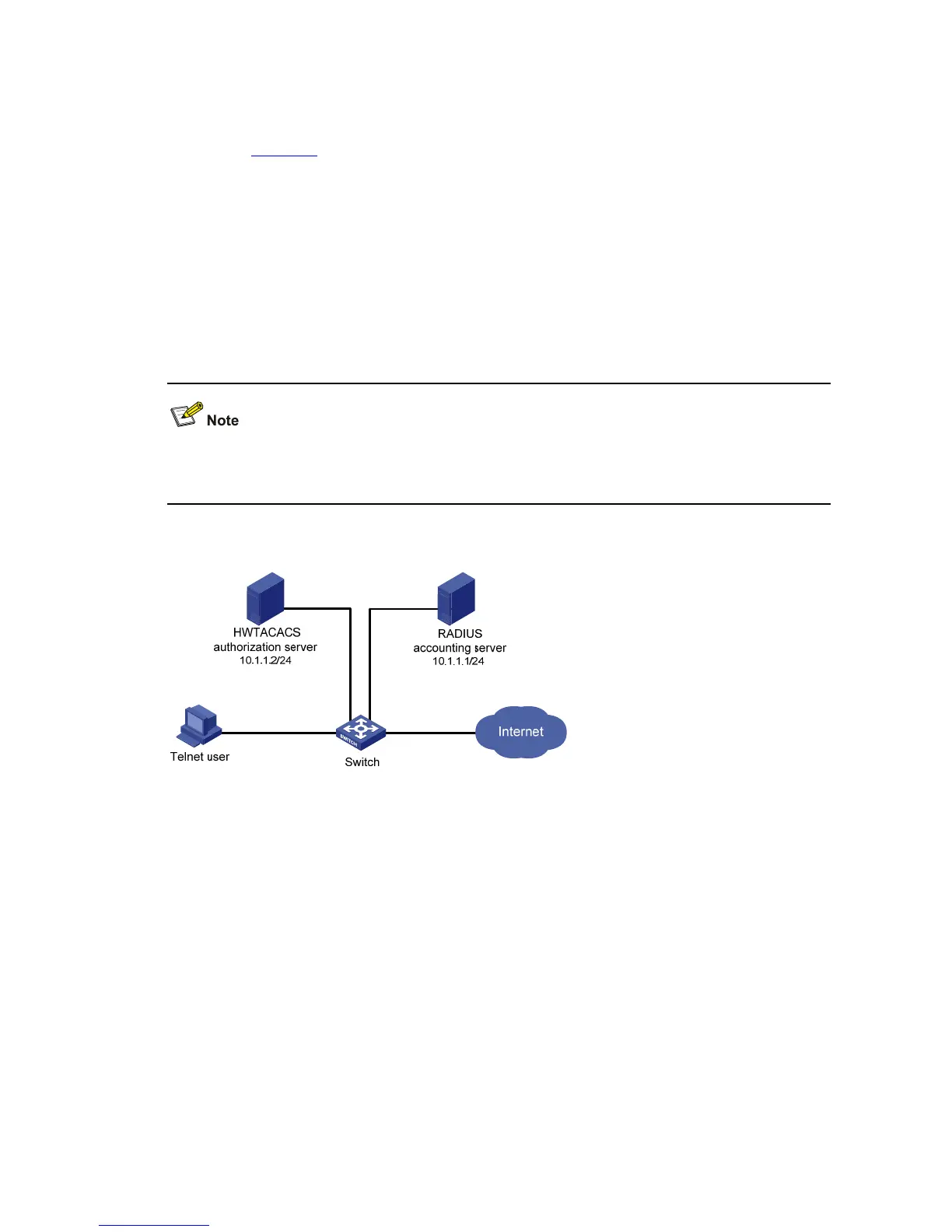
As shown in Figure 1-8, configure the switch to provide local authentication, HWTACACS authorization,
and RADIUS accounting services to Telnet users. The user name and the password for Telnet users
are both hello.
z The HWTACACS server is used for authorization. Its IP address is 10.1.1.2. On the switch, set the
shared keys for packets exchanged with the HWTACACS server to expert. Configure the switch
to remove the domain name from a user name before sending the user name to the HWTACACS
server.
z The RADIUS server is used for accounting. Its IP address is 10.1.1.1. On the switch, set the
shared keys for packets exchanged with the RADIUS server to expert.
Configuration of separate AAA for other types of users is similar to that given in this example. The only
difference lies in the access type.
Figure 1-8 Configure AAA by separate servers for Telnet users
Configuration procedure
# Configure the IP addresses of various interfaces (omitted).
# Enable the Telnet server on the switch.
<Switch> system-view
[Switch] telnet server enable
# Configure the switch to use AAA for Telnet users.
[Switch] user-interface vty 0 4
[Switch-ui-vty0-4] authentication-mode scheme
[Switch-ui-vty0-4] quit
# Configure the HWTACACS scheme.
[Switch] hwtacacs scheme hwtac
[Switch-hwtacacs-hwtac] primary authorization 10.1.1.2 49
[Switch-hwtacacs-hwtac] key authorization expert
 Loading...
Loading...











