8-1
8 Controlling Login Users
When controlling login users, go to these sections for information you are interested in:
z Introduction
z Controlling Telnet Users
z Controlling Network Management Users by Source IP Addresses
Introduction
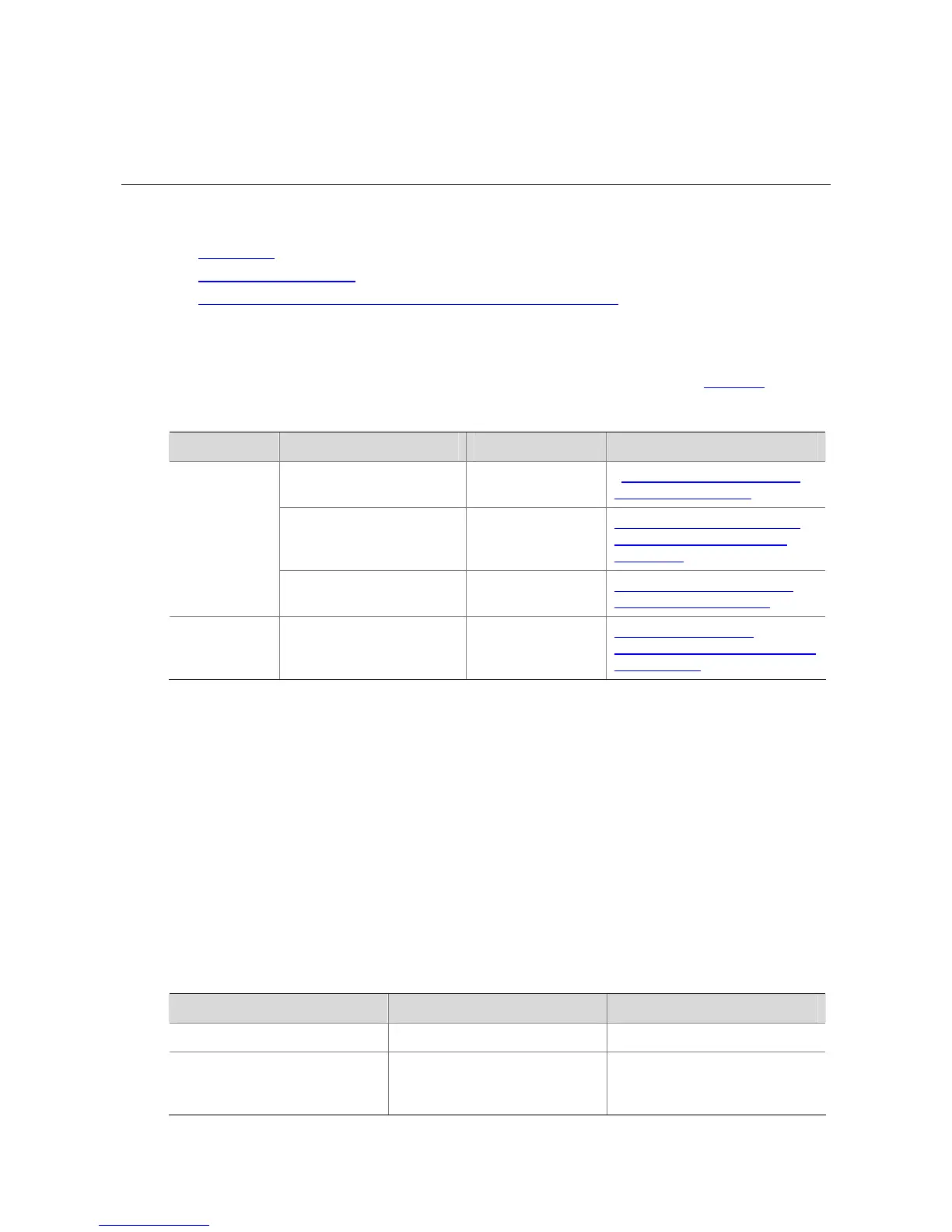
Multiple ways are available for controlling different types of login users, as listed in Table 8-1.
Table 8-1 Ways to control different types of login users
Login mode Control method Implementation Related section
By source IP addresses
Through basic
ACLs
Controlling Telnet Users by
Source IP Addresses
By source and destination
IP addresses
Through advanced
ACLs
Controlling Telnet Users by
Source and Destination IP
Addresses
Telnet
By source MAC
addresses
Through Layer 2
ACLs
Controlling Telnet Users by
Source MAC Addresses
SNMP By source IP addresses
Through basic
ACLs
Controlling Network
Management Users by Source
IP Addresses
Controlling Telnet Users
Prerequisites
The controlling policy against Telnet users is determined, including the source and destination IP
addresses to be controlled and the controlling actions (permitting or denying).
Controlling Telnet Users by Source IP Addresses
This configuration needs to be implemented by basic ACL; a basic ACL ranges from 2000 to 2999. For
the definition of ACL, refer to ACL Configuration in the Security Volume.
Follow these steps to control Telnet users by source IP addresses:
To do… Use the command… Remarks
Enter system view system-view —
Create a basic ACL or enter
basic ACL view
acl [ ipv6 ] number acl-number
[ match-order { config |
auto } ]
As for the acl number
command, the config keyword
is specified by default.

 Loading...
Loading...











