186
# After the user passes identity authentication and security check, use the following command to
display information about the portal user.
[Switch] display portal user interface vlan-interface 100
Total portal users: 1
Username: abc
Portal server: newpt
State: Online
VPN instance: N/A
MAC IP VLAN Interface
0015-e9a6-7cfe 2.2.2.2 100 Vlan-interface100
Authorization information:
DHCP IP pool: N/A
User profile: N/A
Session group profile: N/A
ACL: 3001
CAR: N/A
Configuring extended re-DHCP portal authentication
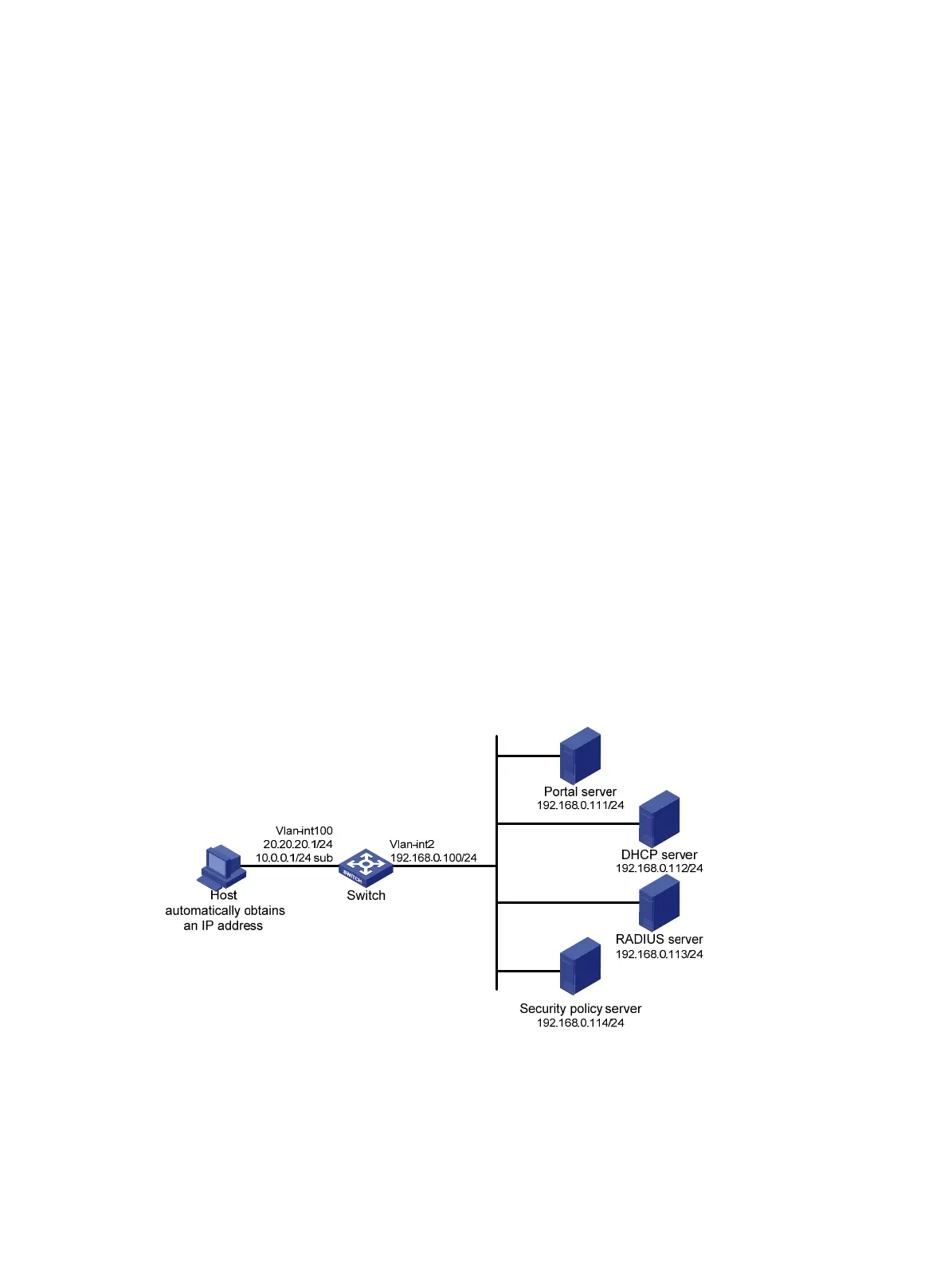
Network requirements
As shown in Figure 59, the host is directly connected to the switch (the access device). The host
obtains an IP address through the DHCP server. A portal server acts as both a portal authentication
server and a portal Web server. A RADIUS server acts as the authentication/accounting server.
Configure extended re-DHCP portal authentication. Before passing portal authentication, the host is
assigned a private IP address. After passing portal identity authentication, the host obtains a public
IP address and accepts security check. If the host fails the security check, it can access only subnet
192.168.0.0/24. After passing the security check, the host can access other network resources.
Figure 59 Network diagram
Configuration prerequisites and guidelines
• Configure IP addresses for the switch and servers as shown in Figure 59 and make sure the
host, switch, and servers can reach each other.
• Configure the RADIUS server correctly to provide authentication and accounting functions.

 Loading...
Loading...











