470
[DeviceB-Ten-GigabitEthernet1/0/1] quit
# Enable ARP attack detection for VLAN 10.
[DeviceB] vlan 10
[DeviceB-vlan10] arp detection enable
# Configure the upstream interface as a trusted interface. By default, an interface is an
untrusted interface.
[DeviceB-vlan10] interface ten-gigabitethernet 1/0/3
[DeviceB-Ten-GigabitEthernet1/0/3] arp detection trust
[DeviceB-Ten-GigabitEthernet1/0/3] quit
# Configure a static IP source guard binding entry on interface Ten-GigabitEthernet 1/0/2 for
user validity check.
[DeviceB] interface ten-gigabitethernet 1/0/2
[DeviceB-Ten-GigabitEthernet1/0/2] ip source binding ip-address 10.1.1.6 mac-address
0001-0203-0607 vlan 10
[DeviceB-Ten-GigabitEthernet1/0/2] quit
# Enable ARP packet validity check by checking the MAC addresses and IP addresses of ARP
packets.
[DeviceB] arp detection validate dst-mac ip src-mac
After the configurations are completed, Device B first checks the validity of ARP packets
received on Ten-GigabitEthernet 1/0/1 and Ten-GigabitEthernet 1/0/2. If the ARP packets are
confirmed valid, Device B performs user validity check by using the static IP source guard
bindings and finally DHCP snooping entries.
ARP restricted forwarding configuration example
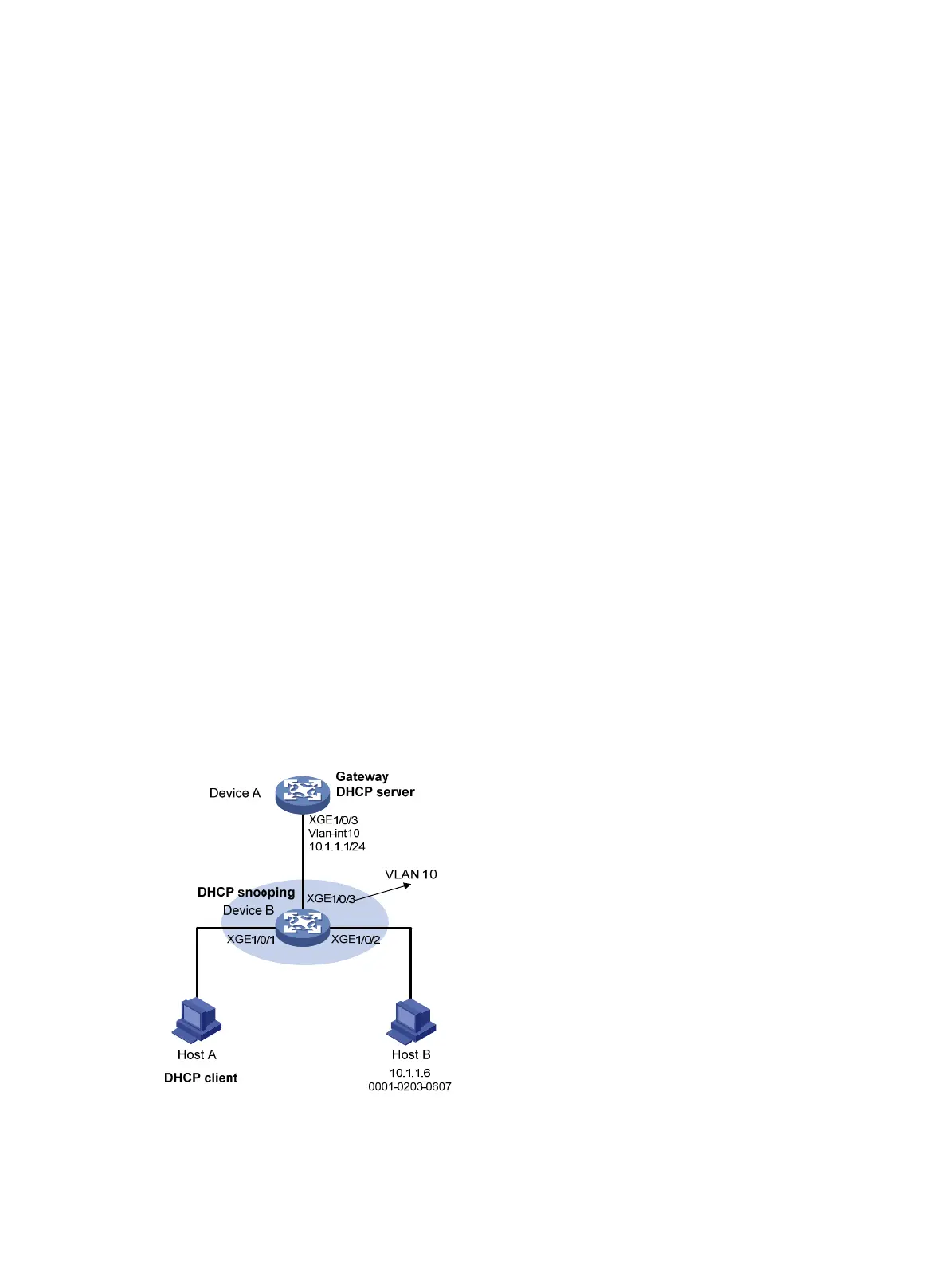
Network requirements
As shown in Figure 134, configure ARP restricted forwarding on Device B where ARP attack
detection is configured. Port isolation configured on Device B can take effect for broadcast ARP
requests.
Figure 134 Network diagram

 Loading...
Loading...











