430
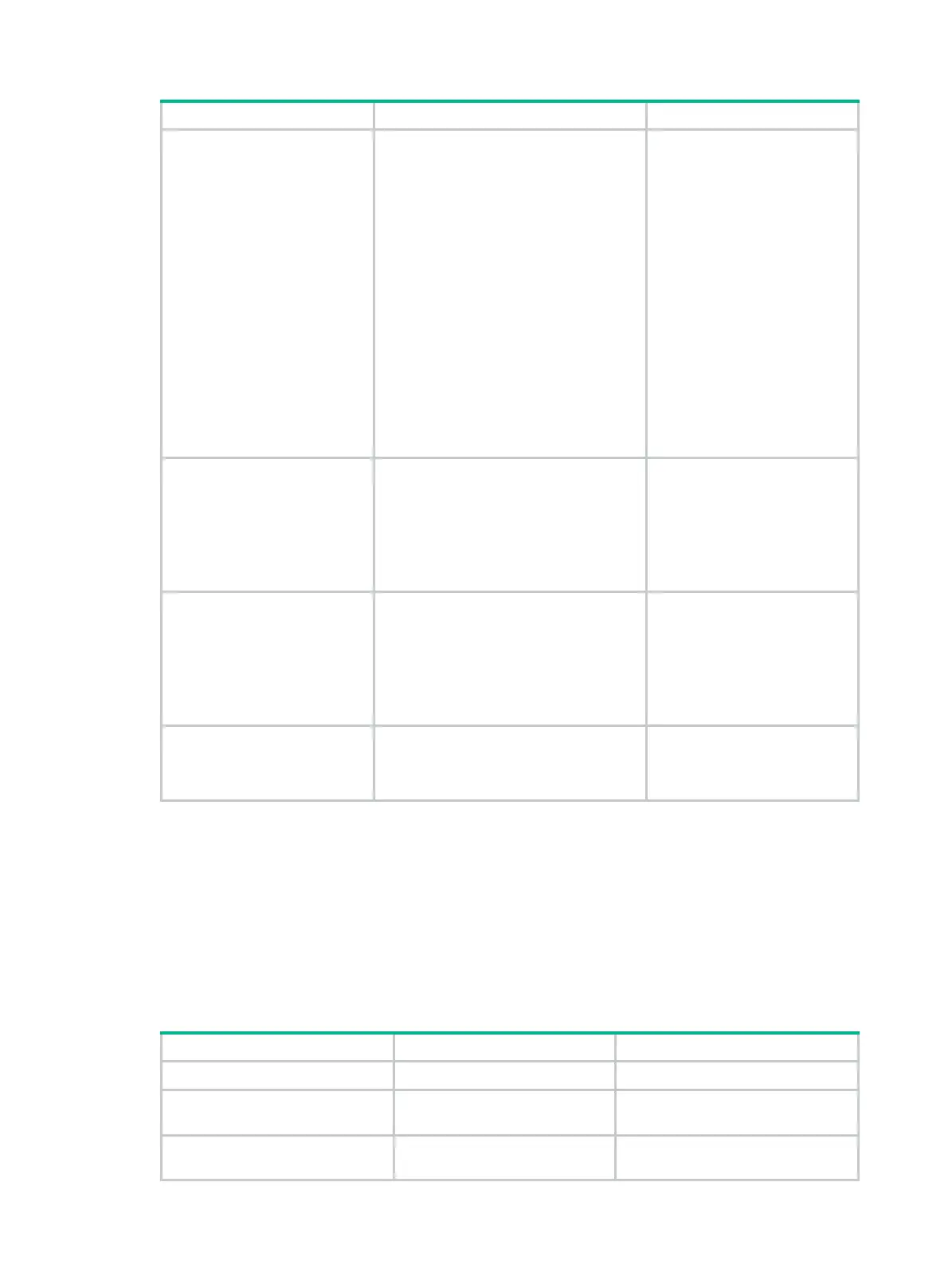
Step Command Remarks
• signature detect icmpv6-type
{ icmpv6-type-value |
destination-unreachable |
echo-reply | echo-request |
group-query | group-reduction |
group-report | packet-too-big |
parameter-problem |
time-exceeded } [ action { { drop |
logging } * | none } ]
• signature detect ip-option
{ option-code | internet-timestamp
| loose-source-routing |
record-route | route-alert |
security | stream-id |
strict-source-routing } [ action
{ { drop | logging } * | none } ]
• signature detect ipv6-ext-header
ext-header-value [ action { { drop |
logging } * | none } ]
4. (Optional.) Set the
maximum length of safe
ICMP or ICMPv6 packets.
signature
{
large-icmp
|
large-icmpv6
}
max-length
length
By default, the maximum
length of safe ICMP or ICMPv6
packets is 4000 bytes.
A large ICMP or ICMPv6
attack occurs if an ICMP or
ICMPv6 packet larger than the
specified length is detected.
5. (Optional.) Specify the
actions against
single-packet attacks of a
specific level.
signature level
{
high
|
info
|
low
|
medium
}
action
{ {
drop
|
logging
} *
|
none
}
The default action is
logging
for single-packet attacks of the
informational and low levels.
The default actions are
logging
and
drop
for
single-packet attacks of the
medium and high levels.
6. (Optional.) Enable
signature detection for
single-packet attacks of a
specific level.
signature level
{
high
|
info
|
low
|
medium
}
detect
By default, signature detection
is disabled for all levels of
single-packet attacks.
Configuring a scanning attack defense policy
Scanning attack detection inspects the incoming packet rate of connections to the device. If a source
initiates connections at a rate equal to or exceeding the pre-defined threshold, the device can take
the following actions:
• Output logs.
• Drop subsequent packets from the IP address of the attacker.
To configure a scanning attack defense policy:
Step Command Remarks
1. Enter system view.
system-view
N/A
2. Enter attack defense policy
view.
attack-defense policy
policy-name
N/A
3. Configure scanning attack
detection.
scan detect level
{
high
|
low
|
medium
}
action
{
drop
|
By default, scanning attack
detection is not configured.

 Loading...
Loading...











