478
The ND logging feature logs source MAC inconsistency events, and it sends the log messages to the
information center. The information center can then output log messages from different source
modules to different destinations. For more information about the information center, see Network
Management and Monitoring Configuration Guide.
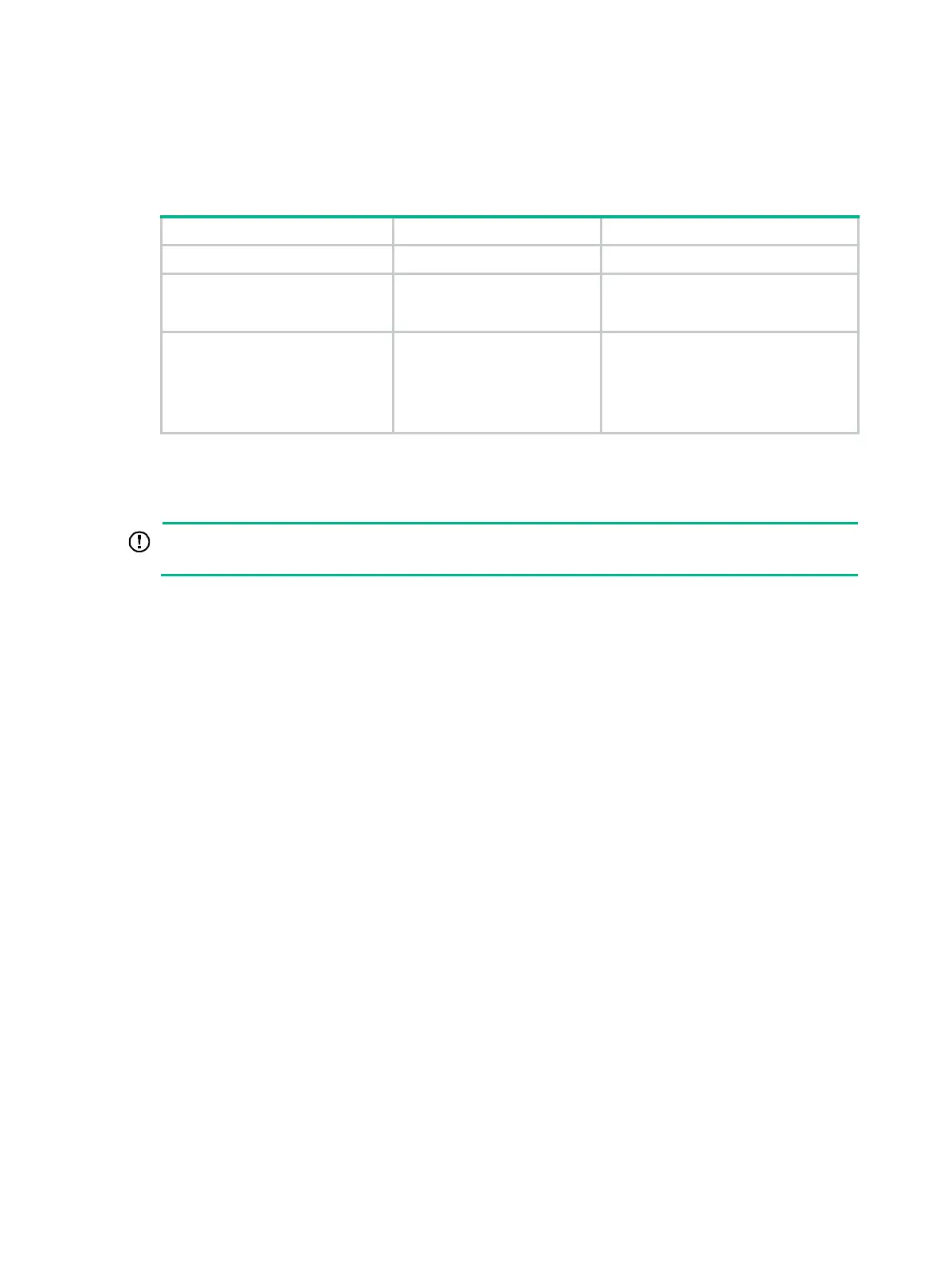
To enable source MAC consistency check for ND messages:
Step Command Remarks
1. Enter system view.
system-view
N/A
2. Enable source MAC
consistency check for ND
messages.
ipv6 nd mac-check enable
By default, source MAC consistency
check is disabled for ND messages.
3. (Optional.) Enable the ND
logging feature.
ipv6 nd check log enable
By default, the ND logging feature is
disabled.
As a best practice, disable the ND
logging feature to avoid excessive ND
logs.
Configuring ND attack detection
IMPORTANT:
This feature is available in Release 2509P02 and later.
About ND attack detection
ND attack detection checks incoming ND messages for user validity to prevent spoofing attacks. It is
typically configured on access devices.
ND attack detection defines the following types of interfaces:
• ND trusted interface—The device directly forwards ND messages or data packets received by
ND trusted interfaces. It does not perform user validity check.
• ND untrusted interface—The device discards RA and redirect messages received by ND
untrusted interfaces. For other types of ND messages received by the ND untrusted interfaces,
the device checks the user validity.
ND attack detection compares the source IPv6 address and the source MAC address in an incoming
ND message against security entries from other modules.
• If a match is found, the device verifies the user as legal in the receiving VLAN, and it forwards
the packet.
• If no match is found, the device verifies the user as illegal, and it discards the ND message.
ND attack detection uses the following security entries for user validity check:
• Static IPv6 source guard binding entries, which are created by using the ipv6 source binding
command. For information about IPv6 source guard, see "Configuring IP source guard."
• ND snooping entries. For information about ND snooping, see Layer 3–IP Services
Configuration Guide.
• DHCPv6 snooping entries. For information about DHCPv6 snooping, see Layer 3–IP Services
Configuration Guide.

 Loading...
Loading...











