Network Setup
4-89
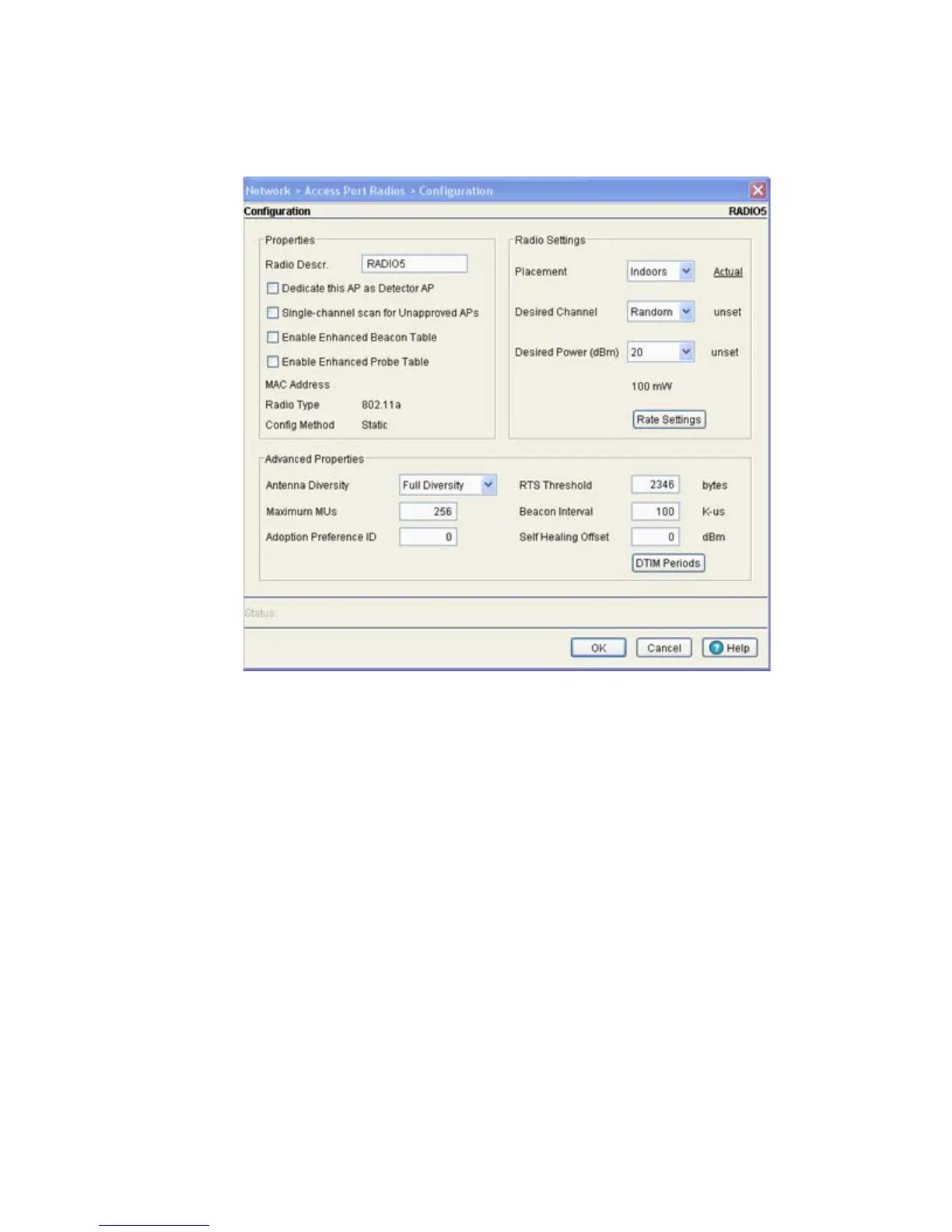
3. Select a radio to edit from the table.
4. Click the Edit button to display a screen containing settings for the selected radio.
5. In the Radio Descr. field, enter a brief description to differentiate the radio. The description is used
to describe radios of the same type and can be used to locate a radio if there are any problems.
6. Select the Dedicate this AP as Detector AP to use this radio as a detector port to identify rogue
APs on the network
Setting this radio as a detector dedicates the radio to detect rogue APs on the network. Dedicated
detectors do not service clients.
7. Select the Single-channel scan for Unapproved APs checkbox to enable the switch to scan for
rogue devices using the radio’s current channel of operation.
8. Select the Enable Enhanced Beacon Table checkbox to allow adopted access port or access point
radios to scan for potentially unauthorized APs across all bands.
This option utilizes radio bandwidth, but is an exhaustive means of scanning across all available
channels and listening for AP beacon traffic. Once probe responses are received, a network device
management application like Motorola RFMS or the Wireless Intrusion Protection System (WIPS) can
locate the device and remove it if defined as unauthorized.
9. Select the Enable Enhanced Probe Table checkbox to enable an adopted access port or access
point radio to forward the probes required to obtain MU RSSI information.
RSSI data (as obtained by at least three detecting radios) can be used by the Motorola RFMS
application to triangulate the location of a MU on a site map representative of the actual physical
dimensions of the switch radio coverage area. Once located on a site map, intuitive decisions can be
made regarding the MU’s authorization within the switch managed network.

 Loading...
Loading...