Switch Security
6-57
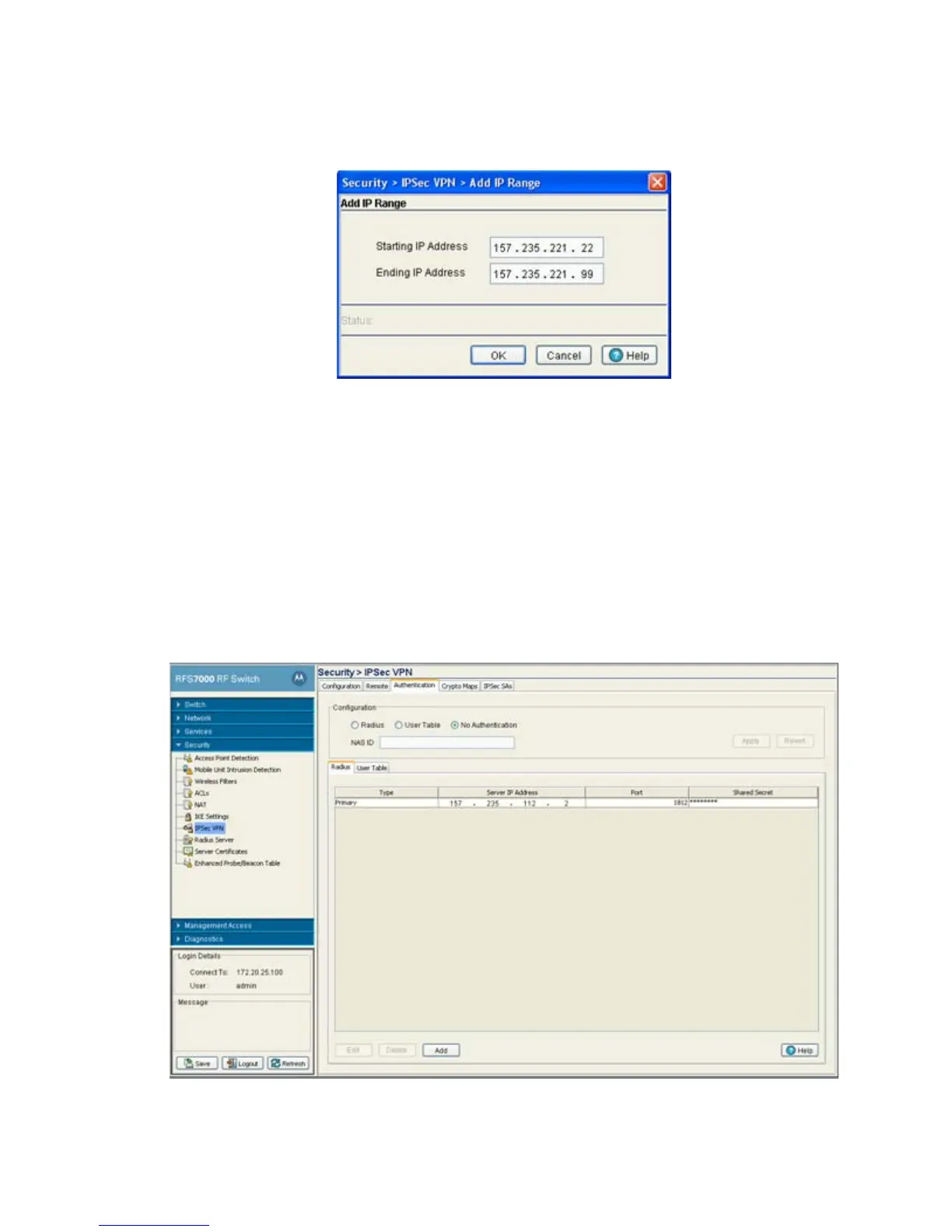
7. To add a new range of IP addresses, click the Add button (within the IP Range tab) and define the
range in the fields provided. Click OK when completed to save the changes.
8. Click Cancel to disregard the changes and revert to the last saved configuration.
6.8.3 Configuring IPSEC VPN Authentication
If IKE is not used for establishing security associations, there is no negotiation of security associations.
Consequently, the configuration information in both systems must be the same for traffic to be processed
successfully by the IPSec resource. Select the Authentication tab to define the credential verification
mechanisms used with the IPSEC VPN configuration.
To define the IPSEc VPN authentication configuration:
1. Select Security > IPSec VPN from the main menu tree.
2. Select the Authentication tab.
3. Define whether IPSec VPN user authentication is conducted using a Radius Server (by selecting the
Radius radio button), by a user-defined set of names and password (by selecting the User Table

 Loading...
Loading...