Authentication method
● CA certificate, device and partner certificate (digital signatures)
The use of certificates is an asymmetrical cryptographic system in which every node
(device) has a pair of keys. Each node has a secret, private key and a public key of the
partner. The private key allows the device to authenticate itself and to generate digital
signatures.
● Pre-shared key
The use of a pre-shared key is a symmetrical cryptographic system. Each node has only one
secret key for decryption and encryption of data packets. The authentication is via a
common password.
Local ID and remote ID
The local ID and the remote ID are used by IPsec to uniquely identify the partners (VPN end
point) during establishment of a VPN connection.
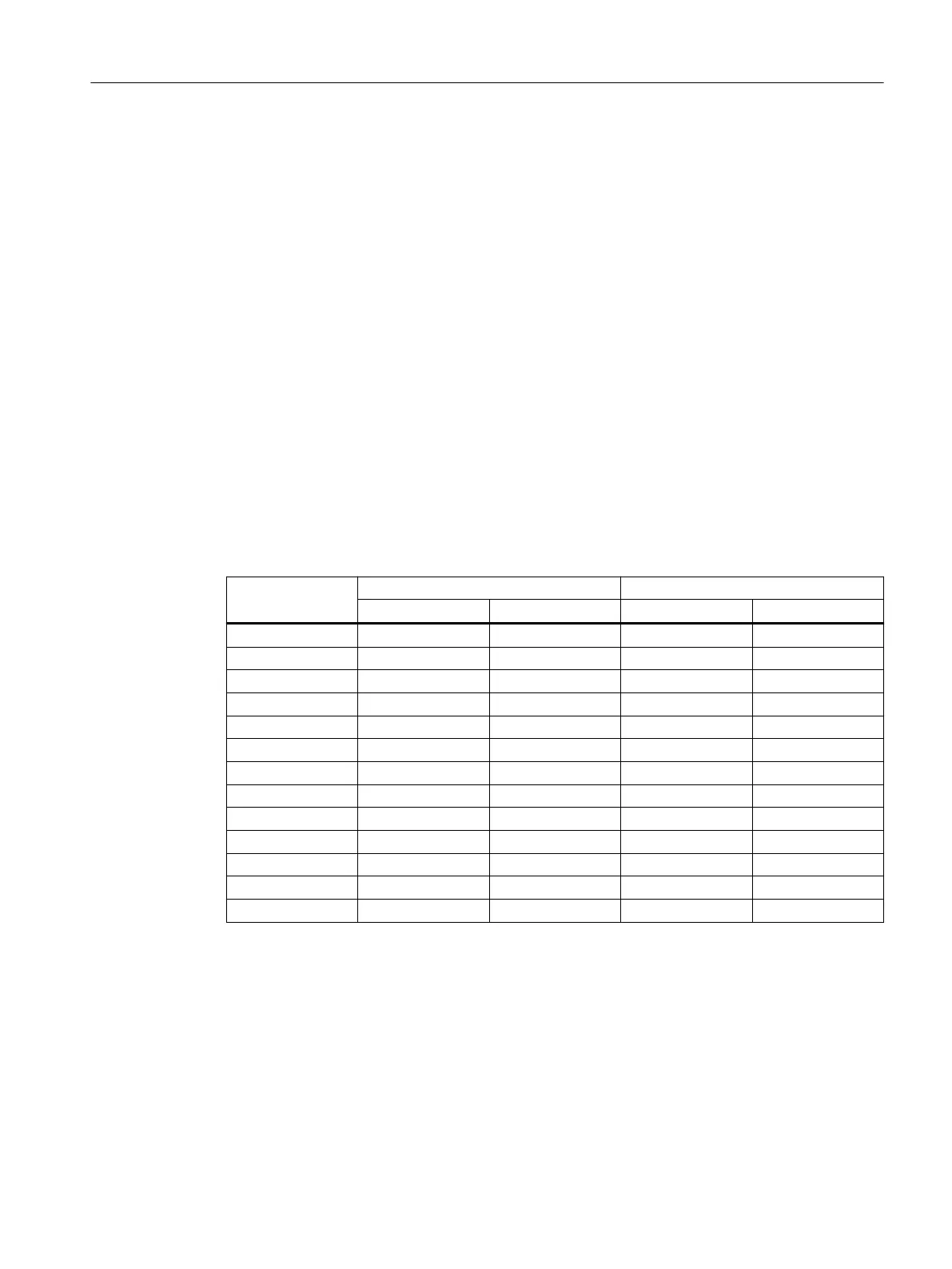
Encryption methods
The following encryption methods are supported. The selection depends on the phase und the
key exchange method (IKE)
Phase 1 Phase 2
IKEv1 IKEv2 IKEv1 IKEv2
3DES x x x x
AES128 CBC x x x x
AES192 CBC x x x x
AES256 CBC x x x x
AES128 CTR - x x x
AES192 CTR - x x x
AES256 CTR - x x x
AES128 CCM 16 - x x x
AES192 CCM 16 - x x x
AES256 CCM 16 - x x x
AES128 GCM 16 - x x x
AES192 GCM 16 - x x x
AES256 GCM 16 - x x x
x: is supported
-: is not supported
Technical basics
3.5 Security functions
SCALANCE S615 Web Based Management
Configuration Manual, 11/2019, C79000-G8976-C388-08 51

 Loading...
Loading...









