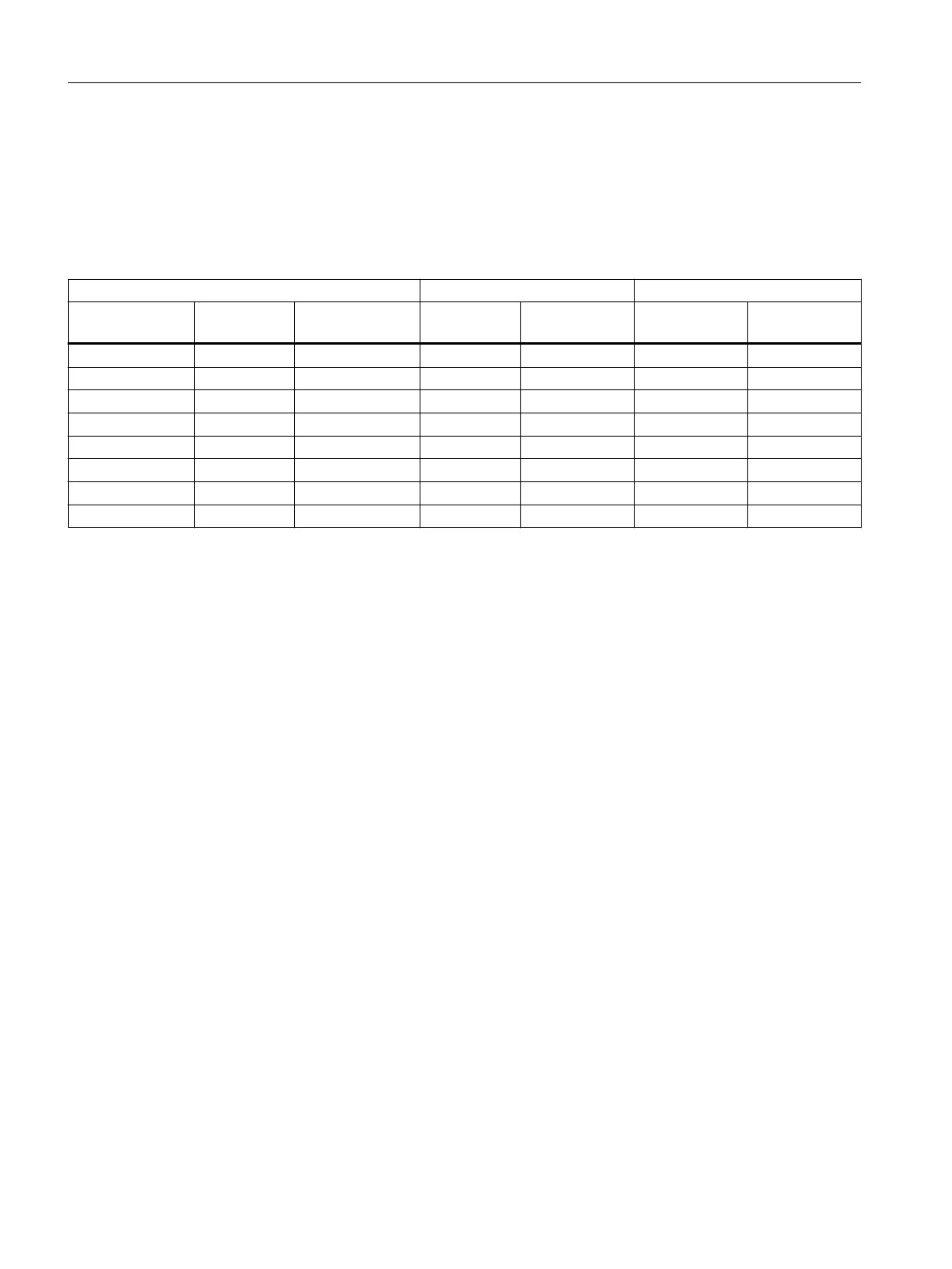
Default Ciphers
During connection establishment a preset list can be transferred to the VPN connection
partners. The list contains combinations of the three algorithms (Encryption, Authentication,
Key Derivation). To establish a VPN connection, the VPN connection partner must support at
least one of these combinations. The combinations depend on the phase und the key exchange
method IKE).
Combination Phase 1 Phase 2
Encryption Authentica‐
tion
Key derivation IKEv1 IKEv2 IKEv1 IKEv2
AES128 SHA1 DH Group 14 x x x x
AES256 SHA512 DH Group 16 x x x x
AES128 CCM 16 SHA256 DH Group 14 - x x x
AES256 CCM 16 SHA512 DH Group 16 - x x x
AES128 SHA1 none - - x x
AES256 SHA512 none - - x x
AES128 CCM 16 SHA256 none - - x x
AES256 CCM 16 SHA512 none - - x x
x: Combination is part of the default cipher
-: Combination is not part of the default cipher
none: For phase 2, no separate keys are exchanged. This means that Perfect Forward Secrecy (PFS) is disabled.
Requirements of the VPN partner
The VPN partner must support IPsec with the following configuration to be able to establish an
IPsec connection successfully:
● Authentication with partner certificate, CA certificates or pre-shared key
● IKEv1 or IKEv2
● Support of at least one of the following DH groups: Diffie-Hellman group 1, 2, 5 and 14 - 18
● 3DES or AES encryption
● MD5, SHA1, SHA256, SHA384 or SHA512
● Tunnel mode
If the VPN partner is downstream from a NAT router, the partner must support NAT-T. Or, the
NAT router must know the IPsec protocol (IPsec/VPN passthrough).
NAT traversal (NAT-T)
There may be a NAT router between the device and the VPN gateway of the remote network.
Not all NAT routers allow IPsec frames to pass through. This means that it may be necessary
to encapsulate the IPsec frames in UDP packets to be able to pass through the NAT router.
Technical basics
3.5 Security functions
SCALANCE S615 Web Based Management
52 Configuration Manual, 11/2019, C79000-G8976-C388-08

 Loading...
Loading...









