• The default gateway is the Internet interface
• VPN policy is configured on the Internet interface egress as follows:
- Traffic from the local subnets to any IP address is encrypted, using tunnel
mode IPSec
- The remote peer is the Main Office (the VPN Hub)
• An access control list (ACL) is configured on the Internet interface to allow only
the VPN / ICMP traffic. See
Simple VPN topology on page 506 for
configuration settings.
2. Configure the VPN Hub (Main Office) as follows:
• Static routing: Branch subnets > Internet interface
• The VPN policy portion for the branch is configured as a mirror image of the
branch, as follows:
- Traffic from any to branch local subnets > encrypt, using tunnel mode
IPSec
- The remote peer is the VPN spoke (Branch Internet address)
Note:
For information about using access control lists, see Policy lists on page 557.
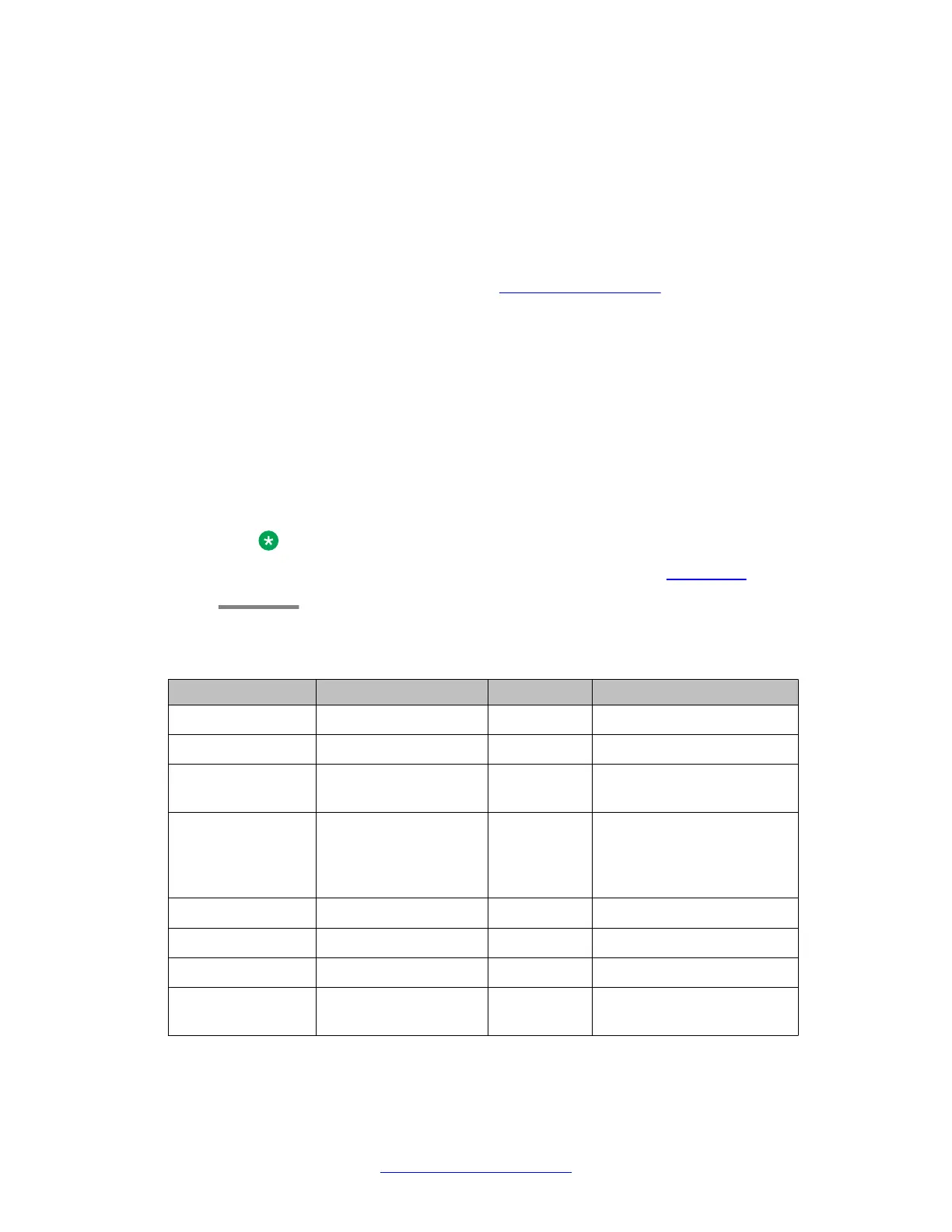
Simple VPN topology
Traffic direction ACL parameter ACL value Description
Ingress IKE Permit -
Ingress ESP Permit -
Ingress ICMP Permit This enables the PMTUD
application to work
Ingress All allowed services
from any IP address to
any local subnet
Permit Due to the definition of the
VPN Policy, this will be
allowed only if traffic comes
over ESP
Ingress Default VPN policy Deny -
Egress IKE Permit -
Egress ESP Permit -
Egress ICMP Permit This enables the PMTUD
application to work
IPSec VPN
506 Administering Avaya G430 Branch Gateway October 2013
Comments? infodev@avaya.com
 Loading...
Loading...




