User manual CHD FiVE
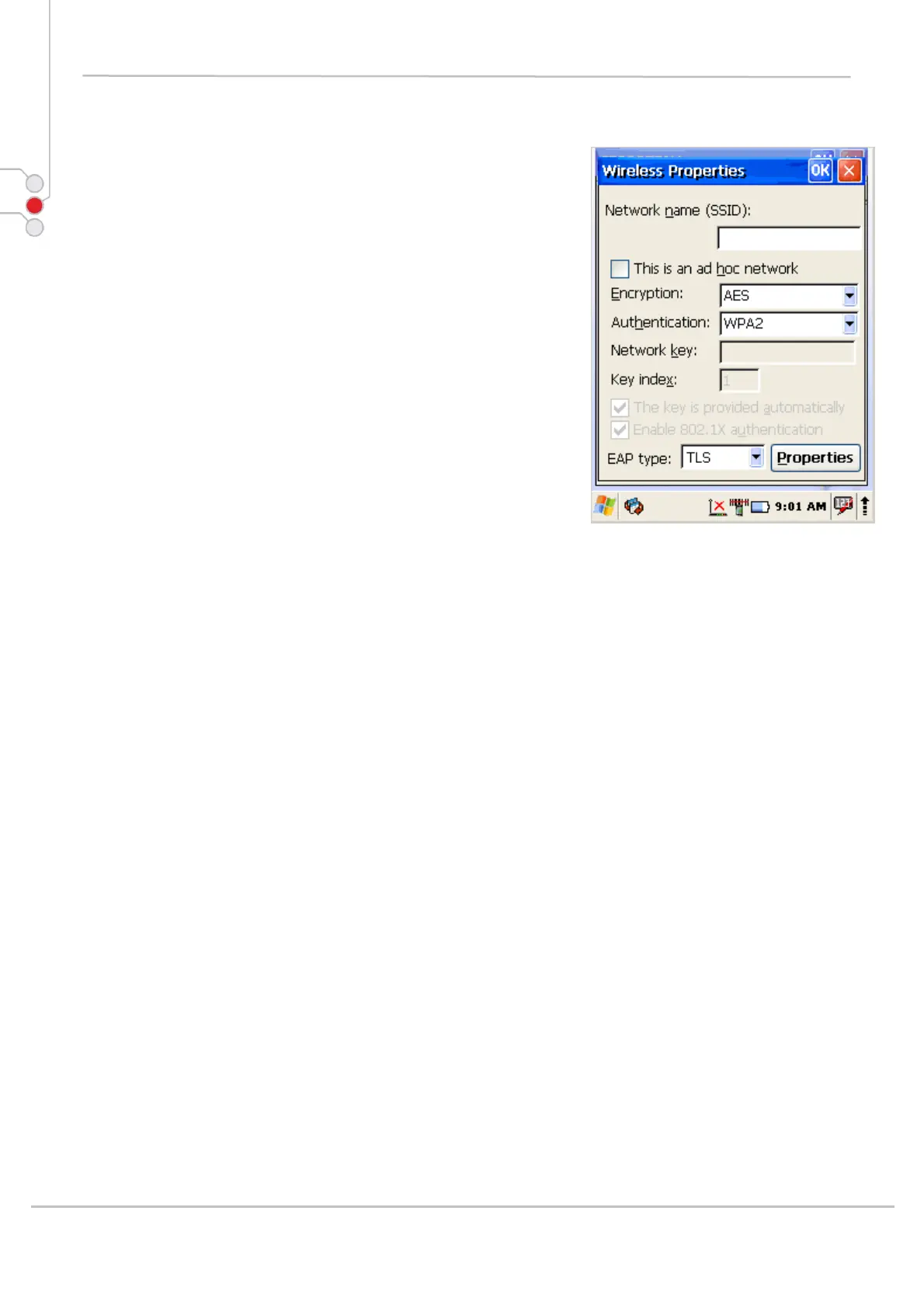
1. Enter Network name (SSID)
2. Check if This is an ad hoc network.
Ad hoc is a network connection method when
connection is established for the duration of one
session and requires no base station. Instead,
devices discover others within range to form a
network for those computers. Devices may
search for target nodes that are out of range by
flooding the network with broadcasts that are
forwarded by each node.
3. Select encryption
AES - Advanced Encryption Standard
TKIP - Temporal Key Integrity Protocol
4. Select authentication methods:
Open
Shared
WPA
WPA2
WPA2-PSK
WPA-PSK
Wi-Fi Protected Access (WPA and WPA2) is a class of systems to secure wireless (Wi-Fi)
computer networks. WPA implements the majority of the IEEE 802.11i standard, and was
intended as an intermediate measure to take the place of WEP while 802.11i was prepared.
WPA is designed to work with all wireless network interface cards, but not necessarily with
first generation wireless access points. WPA2 implements the full standard, but will not work
with some older network cards.
Pre-shared key mode (PSK, also known as personal mode) is designed for networks
without of an 802.1X authentication server. Each user must enter a passphrase to access
the network. The pass phrase may be from 8 to 63 printable ASCII characters or 64
hexadecimal digits (256 bits). The pass phrase may be stored on the user's computer at
their discretion under most operating systems to avoid re-entry. The pass phrase must
remain stored in the Wi-Fi access point.
5. Enter Network key (network passphrase/ password) and if needed Key index.
6. Select EAP type
Extensible Authentication Protocol, or EAP, is a universal authentication framework
frequently used in wireless networks and Point-to-Point connections.
TLS - Transport Layer Security
© All rights reserved
Computer Hardware Design 65
 Loading...
Loading...