1-33
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring Management Access
Feature History for Management Access
Feature History for Management Access
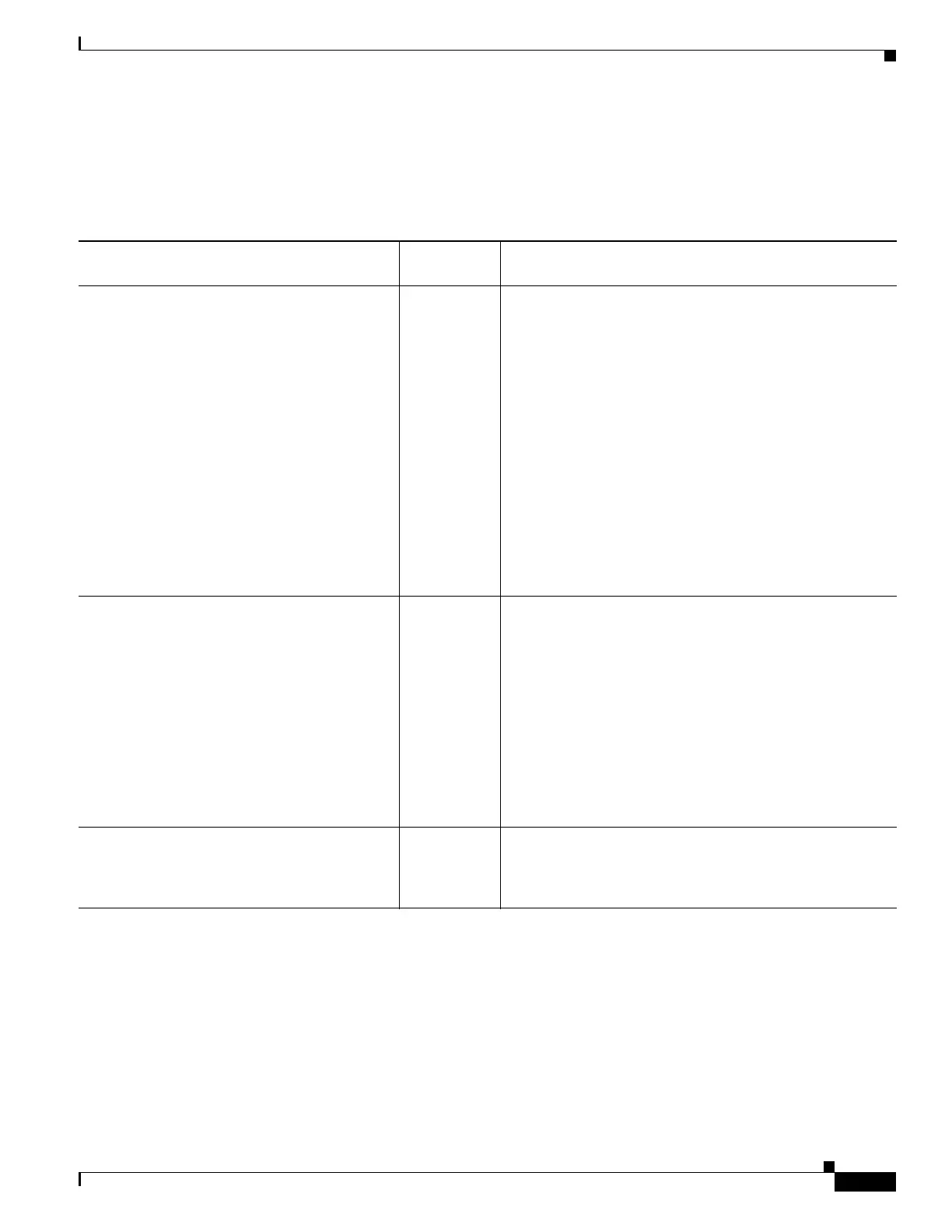
Table 1-3 lists each feature change and the platform release in which it was implemented.
Table 1-3 Feature History for Management Access
Feature Name
Platform
Releases Feature Information
Management Access 7.0(1) We introduced this feature.
We introduced the following commands:
show running-config all privilege all, show
running-config privilege level, show running-config
privilege command, telnet, telnet timeout, ssh, ssh
timeout, http, http server enable, asdm image disk,
banner, console timeout, icmp, ipv6 icmp, management
access, aaa authentication console, aaa authentication
enable console, aaa authentication telnet | ssh console,
service-type, login, privilege, aaa authentication exec
authentication-server, aaa authentication command
LOCAL, aaa accounting serial | telnet | ssh | enable
console, show curpriv, aaa accounting command
privilege.
Increased SSH security; the SSH default
username is no longer supported.
8.4(2) Starting in 8.4(2), you can no longer connect to the ASA
using SSH with the pix or asa username and the login
password. To use SSH, you must configure AAA
authentication using the aaa authentication ssh console
LOCAL command (CLI) or Configuration > Device
Management > Users/AAA > AAA Access >
Authentication (ASDM); then define a local user by
entering the username command (CLI) or choosing
Configuration > Device Management > Users/AAA > User
Accounts (ASDM). If you want to use a AAA server for
authentication instead of the local database, we recommend
also configuring local authentication as a backup method.
For the ASASM in multiple context mode,
support for Telnet and virtual console
authentication from the switch.
8.5(1) Although connecting to the ASASM from the switch in
multiple context mode connects to the system execution
space, you can configure authentication in the admin
context to govern those connections.

 Loading...
Loading...