1-24
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring the Transparent or Routed Firewall
Firewall Mode Examples
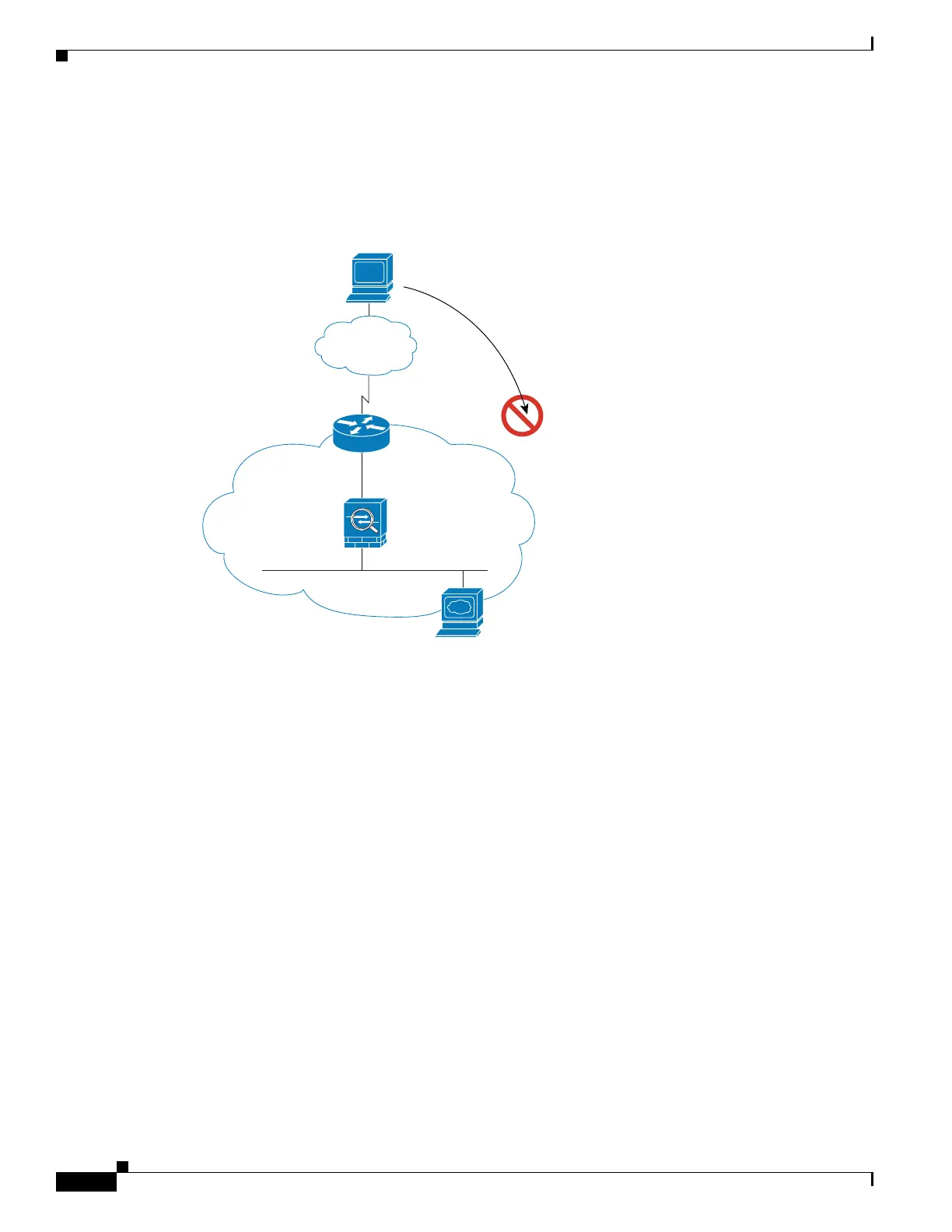
An Outside User Attempts to Access an Inside Host
Figure 1-12 shows an outside user attempting to access a host on the inside network.
Figure 1-12 Outside to Inside
The following steps describe how data moves through the ASA (see Figure 1-12):
1. A user on the outside network attempts to reach an inside host.
2. The ASA receives the packet and adds the source MAC address to the MAC address table, if
required. Because it is a new session, it verifies if the packet is allowed according to the terms of the
security policy (access lists, filters, AAA).
For multiple context mode, the ASA first classifies the packet to a context.
3. The packet is denied because there is no access list permitting the outside host, and the ASA drops
the packet.
4. If the outside user is attempting to attack the inside network, the ASA employs many technologies
to determine if a packet is valid for an already established session.
Management IP
209.165.201.6
Host
209.165.201.2
Host
209.165.201.3
Internet
92410
 Loading...
Loading...