1-6
Cisco ASA Series CLI Configuration Guide
Appendix 1 Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
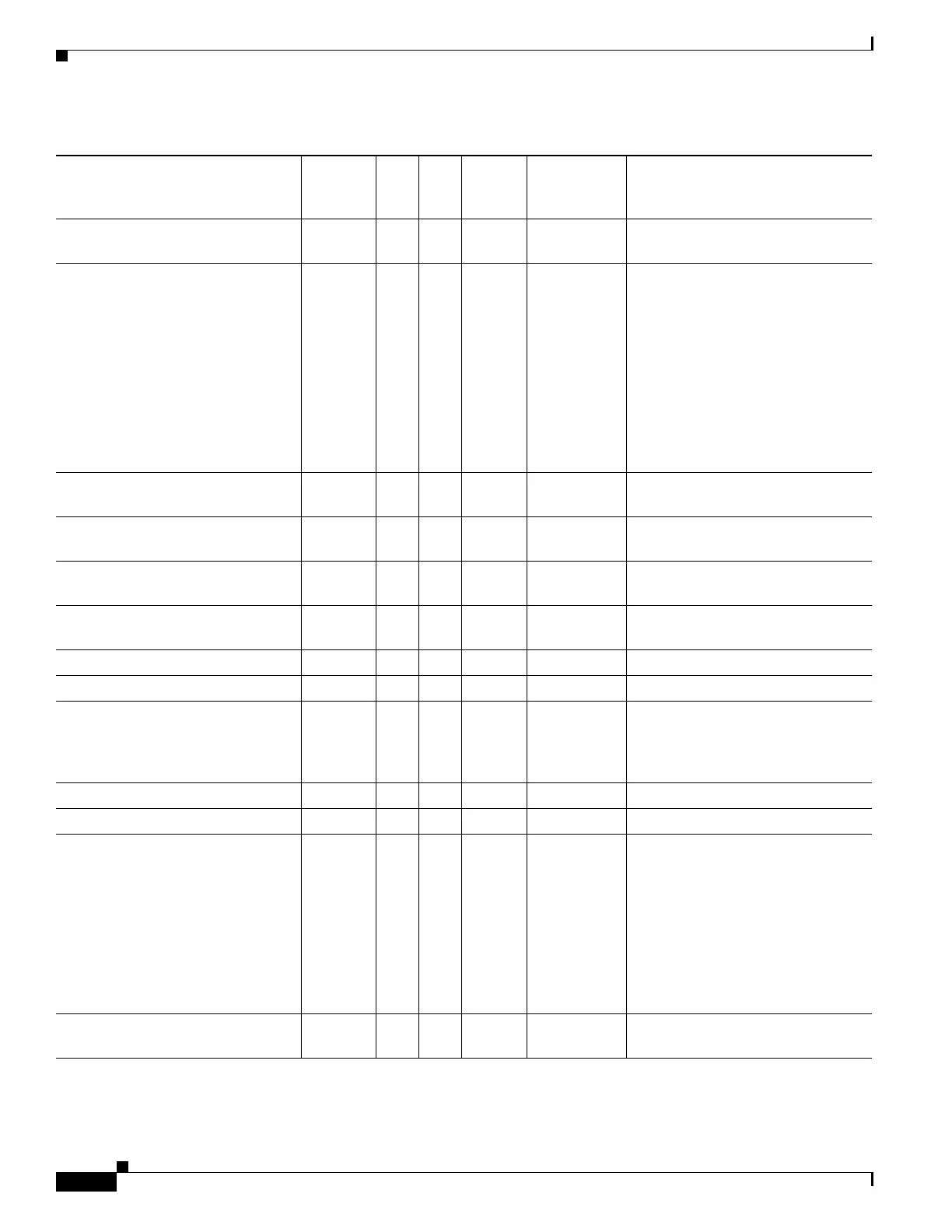
Banner2 Y Y Y String Single Banner string for clientless and
client SSL VPN, and IPsec clients.
Cisco-AV-Pair Y Y Y String Multi An octet string in the following
format:
[Prefix] [Action] [Protocol]
[Source] [Source Wildcard Mask]
[Destination] [Destination Wildcard
Mask] [Established] [Log]
[Operator] [Port]
For more information, see the
“Cisco AV Pair Attribute Syntax”
section on page 1-13.”
Cisco-IP-Phone-Bypass Y Y Y Integer Single 0 = Disabled
1 = Enabled
Cisco-LEAP-Bypass Y Y Y Integer Single 0 = Disabled
1 = Enabled
Client-Intercept-DHCP-
Configure-Msg
Y Y Y Boolean Single 0 = Disabled
1 = Enabled
Client-Type-Version-Limiting Y Y Y String Single IPsec VPN client version number
string
Confidence-Interval Y Y Y Integer Single 10 - 300 seconds
DHCP-Network-Scope Y Y Y String Single IP address
DN-Field Y Y Y String Single Possible values: UID, OU, O, CN,
L, SP, C, EA, T, N, GN, SN, I,
GENQ, DNQ, SER, and
use-entire-name.
Firewall-ACL-In Y Y String Single Access list ID
Firewall-ACL-Out Y Y String Single Access list ID
Group-Policy Y Y String Single Sets the group policy for the remote
access VPN session. For version 8.2
and later, use this attribute instead of
IETF-Radius-Class. You can use
one of the three following formats:
• group policy name
• OU=group policy name
• OU=group policy name:
IE-Proxy-Bypass-Local Boolean Single 0=Disabled
1=Enabled
Table 1-2 ASA Supported Cisco Attributes for LDAP Authorization (continued)
Attribute Name
VPN
3000 ASA PIX
Syntax/
Type
Single or
Multi-Value
dPossible Values
 Loading...
Loading...